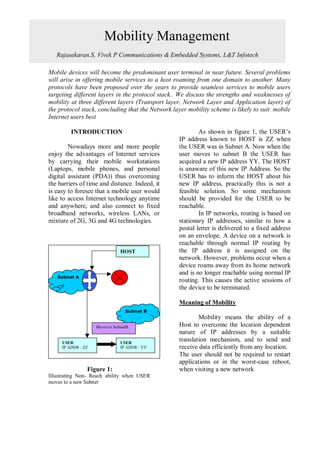
Mobility Management
- 1. Mobility Management ABSTRACT Rajasekaran.S, Vivek P Communications & Embedded Systems, L&T Infotech Mobile devices will become the predominant user terminal in near future. Several problems will arise in offering mobile services to a host roaming from one domain to another. Many protocols have been proposed over the years to provide seamless services to mobile users targeting different layers in the protocol stack.. We discuss the strengths and weaknesses of mobility at three different layers (Transport layer, Network Layer and Application layer) of the protocol stack, concluding that the Network layer mobility scheme is likely to suit mobile Internet users best INTRODUCTION As shown in figure 1, the USER’s IP address known to HOST is ZZ when Nowadays more and more people the USER was in Subnet A. Now when the enjoy the advantages of Internet services user moves to subnet B the USER has by carrying their mobile workstations acquired a new IP address YY. The HOST (Laptops, mobile phones, and personal is unaware of this new IP Address. So the digital assistant (PDA)) thus overcoming USER has to inform the HOST about his the barriers of time and distance. Indeed, it new IP address, practically this is not a is easy to foresee that a mobile user would feasible solution. So some mechanism like to access Internet technology anytime should be provided for the USER to be and anywhere, and also connect to fixed reachable. broadband networks, wireless LANs, or In IP networks, routing is based on mixture of 2G, 3G and 4G technologies. stationary IP addresses, similar to how a postal letter is delivered to a fixed address on an envelope. A device on a network is reachable through normal IP routing by HOST the IP address it is assigned on the network. However, problems occur when a device roams away from its home network and is no longer reachable using normal IP Subnet A routing. This causes the active sessions of the device to be terminated. Meaning of Mobility Subnet B Mobility means the ability of a Moves to SubnetB Host to overcome the location dependent nature of IP addresses by a suitable USER USER translation mechanism, and to send and IP ADDR : ZZ IP ADDR : YY receive data efficiently from any location. The user should not be required to restart applications or in the worst-case reboot, Figure 1: when visiting a new network Illustrating Non- Reach ability when USER moves to a new Subnet
- 2. Why do we need mobility? Network Access Identifier. The user is not mandated to use a specific terminal in Mobile Users have to face several order to connect her “home” network. problems that makes roaming with Internet Instead the user may change terminal from enabled mobile devices difficult. Problems time to time and still get access to the arise when somebody disconnects his same network services without being mobile device from the Internet in order to required to go through annoying and connect elsewhere. Normally she would troublesome configuration procedures not be able to continue communication each time she changes terminal equipment. until she configures the system with the Service Mobility: Allowing users to new IP address, the correct netmask, and a maintain access to their services even new default router. while moving or changing devices and network service providers is termed as Flavors of Mobility Service Mobility There are two flavors of Mobility: Micro Mobility: Micro Mobility refers to APPLICATION L AYER MOBILITY movement of nodes within the same subnet. Application Layer Mobility Micro Mobility: Macro Mobility refers to provides mobility of users. i.e. users can movement of nodes between different use different terminals. Application Layer subnet Mobility is based on SIP (Session Initiation Protocol). SIP supports personal Forms of mobility mobility as part of its signalling mechanism and provide adequate means of We shall see the different terminal, and service mobility. definitions of host mobility, not all of them will be useful for our discussion. Application layer mobility Mobility (Micro / Macro Mobility) can be mechanism doesn’t require any changes in divided, rather seen in different forms as the Mobile Hosts kernel as compared to network layer and transport layer Terminal Mobility: The ability of a mechanisms. However, Application layer terminal, while in motion, to access mobility introduces Handoff Delay and telecommunication services from different Signaling Overhead. Application layer locations, and the capability of the mobility is being considered for next network to identify and locate that generation heterogeneous networks terminal is referred to as Terminal because of the fact that application layer Mobility. being the highest layer, it can function Session Mobility: Session Mobility refers across cross networks. Also introducing to maintaining sessions even while mobility at this layer will force all user changing terminals moving parts of the application to become mobility conscious, session to new devices which is not desirable. Personal Mobility: The ability of a user to access services at any terminal on the The detailed discussion of basis of a personal identifier is termed as Application Layer Mobility protocol is Personal Mobility beyond the scope of this document. Personal (user) mobility makes it possible for a user to use any terminal in order to get access to IP services. The user is identified by means of a NAI [15],
- 3. Like TCP, SCTP is reliable and TRANSPORT LAYER MOBILITY offers new features such as “Multi- Streaming” and “Multi-homing”. In Movement between networks will particular, the multi-homing feature of break transport layer connections. These SCTP enables it to be used for mobility broken connections must be made to support, without any special router agents resume transparently from higher layers. in the network. Introducing mobility at this layer will Other features included in SCTP result in a modification of the existing are error-free and non-duplicated data protocols. transfer, network-level fault tolerance through supporting of multi-homing, and Transport layer mobility will resistance to flooding or masquerade minimize the packet losses during attacks. handovers by holding transmissions during As mentioned earlier, the multi- handoffs. There is no requirement of any homing ability enables SCTP to support new infrastructure compared to network mobility. A host is called Multihomed if it layer mobility where deployments of HA has multiple network layer addresses (e.g. (Home Agent), FA (Foreign Agent) and IP addresses).A transport protocol routers for fast and smooth handover is supports multi-homing if the endpoint can required. have more than one transport layer addresses, as is the case with SCTP. The The transport layer is handling the mobility comes here from the ability to congestion control. Good Congestion change the endpoints (e.g. IP addresses) control requires keeping data on the end- while keeping the end-to-end connection to-end path between the hosts. Whenever intact. the path between the hosts changes, then it is better if the transport layer is aware The problem in SCTP is to perform about the change so that it takes suitable these address recon-figurations steps to adjust to the new path. For dynamically. The solution is to use the example the transmission rate may require Dynamic address Reconfiguration modification to avoid the packet loss. (ADDIP) [11] extension for SCTP, which enables the SCTP to add, delete, and The applications will have better change the IP Addresses during an active control over their sessions, by allowing the connection. applications to specify the network The SCTP with the ADDIP interface to be used for transmission of extension is called mobile SCTP (mSCTP) different traffic. SCTP provides support [10], and it provides a seamless handover for multiple addresses per host for mobile hosts that are roaming between (Multihoming), which can be very useful IP networks. in providing transport layer mobility. When the mobile node (MN) initiates an SCTP association with the Overview of SCTP and mSCTP corresponding node (CN). The resulting association consists of MN’s IP address Stream Control Transmission and CN’s IP address(the primary path). Protocol (SCTP) [9] is an IETF proposed After a while, MN decides to move to a standard protocol for the transport layer. It different network. The following steps [6] is designed to eventually replace TCP and are repeated every time MN moves into a perhaps also UDP. new location.
- 4. Step 1: Obtaining an IP address for new NETWORK LAYER MOBILITY location. As MN is moving towards a new network , at some point it reaches the Mobility can be seen as a “Address overlapping region. Then MN obtains the translation”, i.e the IP changes from ZZ to new IP address from the Access router YY (see figure 1) when the user moves with the help of DHCP [5] or IPv6 address from one location to another. So the auto-configuration. problem can be best resolved at Network layer by defining mechanisms to hide this Step 2: Adding the new IP address to the problem from higher layers. This is the SCTP association .MN informs CN of the type of mobility, which has received most new address by sending an Address attention from the research community, Configuration Change (ASCONF) chunk. particularly with the development of As a reply the ASCONF-ACK is sent. MobileIP in the IETF (Internet Engineering Task Force). Step 3: Changing the primary IP address. Mobile IP is a proposed standard While MN further continues to move protocol that builds on the Internet towards a new Access router , it needs to Protocol by making mobility transparent to set the new address as its primary address. applications and higher-level protocols The changing of addresses is done like TCP. There are two variations of according to specific rules, for example as Mobile IP, Mobile IPV4, based on IPV4 soon as a new IP address is detected. and Mobile IPV6, based on IPV6. However, the configuration of this change- triggering rule is a challenging issue for Overview of Mobile IP mSCTP. Mobile IP enables users to keep the Step 4: Deleting the old IP address. As same IP address while traveling to a MN has moved to a new network , the old different network (which may even be IP address becomes inactive, and it is operated by a different wireless operator), deleted from the address list. The thus ensuring that a roaming individual knowledge from underlying layers can be can continue communication without used to determine when the address sessions or connections being dropped. becomes inactive. It is worth noting that if Mobile IP is designed to solve the problem CN is initiating the association towards the of Macro Mobility Management. It is less MN, a location management scheme is well suited for micro mobility needed. Mobile IP can be used, for management. For our further discussion example, for CN to find the current we will consider only Mobile IPV4. location of MN and to establish an SCTP association. After the association is Mobile IP Terminology successfully setup, the mSCTP will be used for providing seamless handover as Mobile Node(MN) discussed above. But this approach is not A host or router that changes its point of independent by itself. i.e. the transport attachment from one Network or sub layer approach requires more co-operation network to another. from other layers. The Mobile Node is a device such as a cell phone, PDA, or laptop whose software Enables network roaming capabilities. Home Agent (HA) A router on a mobile node’s home network which tunnels datagram’s for delivery to
- 5. the mobile node when it is away from protocol. Diameter provides the home, and maintains current location functionalities such as NAI based user information for the mobile node. authentication, Dynamic Home Agent Allocation in etc. Foreign Agent (FA) A router on a mobile node’s visited AAAH network, which provides routing services Diameter Server in Home Network to the mobile node while, registered. The Foreign agent detunnels and delivers AAAF datagram’s to the mobile node that were Diameter Server in Foreign Network tunneled by the mobile node’s home agent. For datagram’s sent by a mobile node, the Mobile IPV4 operation foreign agent may serve as a default router for registered mobile nodes. Mobility agents ( HA and FA) advertise their services in response to Correspondent Node (CN) agent solicitation message from MN and / A peer node with which MN or periodically advertise their services on communicates. CN may be stationary or the local subnet. Based on these Mobile. advertisements MN determines its location ( Home Network or Foreign Network). If Home Link it is at home network, it will operate The link on which the nodes’ Home subnet without the mobility services. When the prefix is defined. Standard IP routing MN moves into a foreign network it Mechanisms will deliver packets destined obtains a new IP address (“Care-of for a node to its home link. Address”) on the foreign Network. The COA can be obtained in two ways: Mobility Agent Either a Home Agent or a Foreign Agent. 1. From FA’s Advertisement: The IP address advertised by the Agent Advertisement FA (through Agent advertisement) can be An agent advertisement is an ICMP router used by the MN for registering with the advertisement that has been extended to Home Network. This is nothing but the IP also carry a mobility agent advertisement address of the FA. extension. 2. External assignment: A “Co-located Care-of Address” can be acquired by the MN by external Home Network mechanisms such as DHCP [5], or may be A network, possibly virtual, having a owned by the MN as a long-term address network prefix matching that of a mobile for its use only while visiting some foreign node’s home address. network. Foreign Network Using Co-located Care-of Address A network other than the MNs Home has the advantage of removing FA from network. the infrastructure. However, IPV4 addresses are limited in number there by Diameter placing constraint on the number of Co- AAA (Authentication, authorization, located Care-of Addresses. accounting) protocol [8]. Diameter is the successor of the well know RADIUS
- 6. serving the MN, the AAAH. The AAAH authenticates and authorizes the MN and forwards the registration request to the HA Home Netowk serving the MN. The HA responds with a CN Registration reply which takes the same HA path backwards. The AAAH can T optionally allocate a Home Agent for an U MN, which has not been configured with 1 MN requests services N 2 FA relays it to HA the HA IP address. Otherwise the HA N 3 HA Accepts or denies itself can handle the home agent allocation 2 3 4 FA relays reply to to such MN’s. E MN L 2. The FA can directly send the registration request to the HA. The HA contacts the AAAH for authenticating the MN and relays the reply to FA. FA 4 MN The detailed discussion related the 1 AAAH and AAAF are beyond the scope of this document. The Registration reply will contains the status of the registration Figure 2: MN in Foreign Network (Success / Failure, and the reason for failure). The FA relays the registration If the MN is using Co-Located reply to the MN. On Successful Care-of Address, it can interact with the registration the MN is granted a home HA directly. (Except when the FA “Lifetime”, the period for which the MN has not forced the MN to send messages can use the services from the foreign via FA. This is done in some networks to network. enforce local policies on the visiting node) The HA will maintain the list of After acquiring the new IP address MNs roaming outside the home network as mentioned above, the MN must register and information which includes the this new address with the HA. The MN registered COA and services granted to the send a Registration Request to the HA. MN. On expiry of the lifetime the MN has The registration request message is used to to issue a new registration to the HA if it register the MN’s COA with the Home wishes to continue using the services. network and also to request services like reception of Broadcast packets from the Mobile IP uses protocol tunneling Home Network, Reverse Tunneling, to hide the MN’s address from Encapsulation type, etc. intermediate routers between its home For our discussion let us assume the MN is network and its current location. Now any using FA COA. Now the MN sends the datagram’s destined to the MN will be registration request to the FA and intercepted by the HA in the home depending on the network configuration, network. The HA tunnels the datagram’s the FA can relay it in two directions. to the MN’s COA. This mechanism is referred to as “Forward Tunneling”. 1. The FA relays it to the AAA server in its domain (AAAF) which based on the realm part of the MN’s NAI(Network Access Identifier) contacts the AAA server
- 7. How does the HA intercept Packets home network update their ARP cache destined to MN? with the hardware address of the HA against the IP address of the MN. Thus the HA makes use of Address Resolution HA fools other nodes about the location of Protocol (ARP). ARP is used to resolve a the MN. Any node wanting to send the target nodes link-layer address from its IP packet to the MN will send it to HA. The – address. In general every node maintains HA then tunnels the packets to the MN. an ARP table containing IP addresses and the corresponding Hardware addresses When the MN is away from the (MAC addresses). So when it has to send a home network any ARP requests seeking packet on the home link it sends it over the MN’s MAC address is answered by the Ethernet by looking up the ARP table for HA on behalf of MN. This is called MAC address of the required destination “Proxy ARP”.( Figure 3) IP address. When the MN returns back to the home If there is no entry for the concerned IP network, it issues a de-Registration address in the ARP table the node Request to the HA and broadcasts a broadcasts an ARP request packet, only Gratuitous ARP packet on the home Link. the concerned node whose MAC address The HA also broadcasts the gratuitous is requested replies for the request. Now ARP packet, this time with the original the Packets are delivered to this Hardware MAC address of MN. This will be useful address. in wireless networks where the coverage Range Of HA will be more compared to MN. Why tunneling? The application must always see a single IP address at all times, inorder to exist TCP connections alive while handovers. Therefore IP tunnels are used. The tunneling mechanisms used are Figure 3: Home Agent sending Proxy ARP 1. IP encapsulation within IP 2. Generic Routing Encapsulation 3. Minimal Encapsulation within IP. Tunneling includes adding an outer header to the existing packet, which as a whole becomes the payload for this new header as shown in the figure 5 Figure 4: Home Agent Broadcasting Gratuitous ARP On accepting the registration request from the MN, the HA broadcasts Gratuitous ARP packet(with HA’s MAC address and MN’s IP address, Figure 4) the home link, so that all nodes in the
- 8. HA CN IPHEADER Original SRC: MNs Home Address Packet DST: CNs IP address PAYLOAD IPHEADER SRC: MNs COA Encapsulated FA DST: HA IP address Packet PAYLOAD IPHEADER SRC: MNs Home Address MN DST : CNs IP address PAYLOAD Figure 6: Tunneling in MIPV4 Forward Tunnel Figure 5: Encapsulated Packet Reverse Tunnel When the MN needs to send the packets to CN, the MN will use its Home Triangular Routing IP address as source address and CN’s IP address as destination. The MN's Home address prefix is not valid in the foreign Route Optimization network. Usually routers are configured to drop packets originating from a The triangular routing is due to topologically incorrect subnet. So packets (from CN) being sent through the “Reverse Tunneling” is employed where HA and HA tunneling it to the MN. in any packets from MN to CN follows the Instead the HA can update the CN about path: MN FA HA CN. the MN’s Location so that it can directly send packets to MN. This is not preferred The Path Followed by the because MN’s privacy is being touched datagram’s is shown in figure 6. The path upon. takes the shape of a triangle. The There is a problem in using Route “Triangular routing“ problem in Mobile optimization, i.e. when the MN moves out IPV4 is of serious concern as the distance of the Foreign Network before the expiry between the HA and FA increases. To of the “Lifetime” the HA is unaware about solve this problem “Route Optimization” its movement. During this time if CN can be used wants to communicate with the MN, it will not be possible for CN's to exchange packets with MN.
- 9. Open issues in Mobile IPV4 The major upside to implementing mobility support in the IP layer is that Inefficient Routing since it is at the waist of the protocol stack We have discussed the triangular routing hourglass model, it is the one place where and route optimization above. But Route mobility support can benefit every higher optimization requires changes in the CN layer. This is not only beneficial from the which is not desirable. standpoint of minimizing reproduction Of effort, but also in limiting potential Security issues bugs or security concerns A great deal of attention is being focused Table1 gives a comparison of on making Mobile IP coexist with the mobility on transport layer and Network security features coming into use within layer. the Internet. Firewalls, in particular, cause Having see the Pros and Cons of mobility difficulty for Mobile IP because they at various layers, we conclude that block all classes of incoming packets that implementing mobility at network layer is do not meet specified criteria. Enterprise the best option. firewalls are typically configured to block packets from entering via the Internet that Transport/Application Network Layer appear to emanate from internal Layer computers. Although this permits Network layer needs to Same IP management of internal Internet nodes be identified with a new address during without great attention to security, it IP address at every the lifetime of presents difficulties for mobile nodes point of new one IP level wishing to communicate with other nodes attachment session within their home enterprise networks. Simple Internet Routing Complexity in Such communications, originating from (No Tunnels) network layer the mobile node, carry the mobile node's End user Applications Not required home address, and would thus be blocked have to be mobility Slight by the firewall. aware fluctuations when changing CONCLUSION to a new access technology or Introducing mobility at application access network, layer has the disadvantage that end user but commodity applications must be aware of mobility. applications and So keeping mobility out of application TCP sessions layer will simplify end user application will survive. design The transport layer approach Table 1: Comparison of Mobility at Transport layer requires more cooperation between layers and Network Layer. than the network layer approach, as the location management functions are handled separately. In some sense, this is more of a cross-layer or interlayer approach than purely a transport layer approach. The transport layer, however, is the only place where protocols may require significant modifications.
- 10. REFERENCES [12] Perkins, C., “IP Encapsulation within IP”, RFC2003, October 1996 [1]. Wesley M. Eddy, “At What Layer Does Mobility Belong?” IEEE [13] Perkins, C., “Minimal Encapsulation Communications Magazine. October 2004 within IP”, RFC2004, October 1996 [2]. H. Schulzrinne and E. Wedlund, [14] Hanks, S., Li, T., Farinacci, D. and P. "Application-Layer Mobility using SIP", Traina, "Generic Routing Encapsulation ACM Mobile Computing and (GRE)", RFC 2784 March 2000. Communications Review, Vol. 4, No. 3, July 2000, pp. 47-57. [15]B.Aboba, M. Beadles “The Network [3] C. Perkins, Ed., "IP Mobility Support Access Identifier.” RFC2486, January for IPv4", IETF RFC 3344 (Proposed 1999 Standard), Aug 2002. [4] http://www.its.bldrdoc.gov/ [5] Droms, R. “Dynamic Host Biography of the author(s). Configuration Protocol”, RFC2131, March 1997 Rajasekaran. S (Project Leader) Larsen and Toubro InfoTech, [6] Nilanjan Banerjee, Wei Wu, and Sajal Communications Department K. Das. “Mobility Support in Wireless Vivek Purushotham, (SET), Larsen and Internet” IEEE wireless Communication Toubro InfoTech, October 2003 Communications Department [7] http:// www.ipunplugged.com [8] P. Calhoun, H. Akhtar, J. Arkko, E.Guttman, A. Rubens, “Diameter Base Protocol”, RFC 3588, September 2003. [9] Stewart, R., Xie, Q., Mornmeault, K., Sharp, H., Taylor, T.,Rytina, I., Kalla, M., Zhang, L. and V. Paxson, "Stream Control Transport Protocol", RFC 2960, October 2000. [10] Mika Ratola, “Which Layer for Mobility? - Comparing Mobile IPv6, HIP and SCTP” Seminar on InterNetworking [11] [AddIP] Stewart, R., et al., "Stream Control Transmission Protocol (SCTP) Dynamic Address Reconfiguration", Work in Progress.
