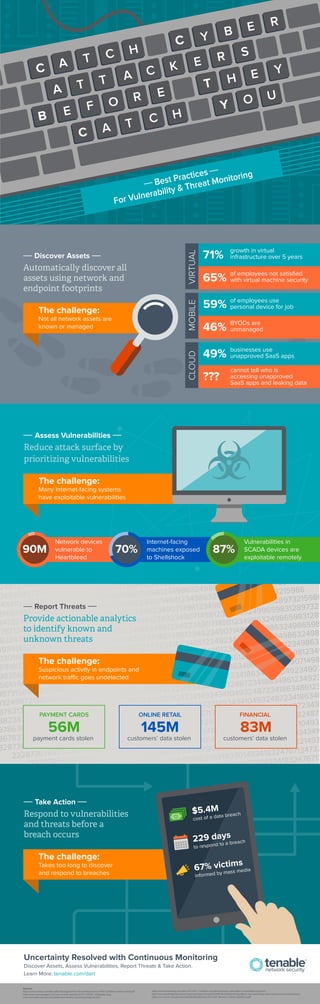
Simultaneous Vulnerability and Threat Monitoring
- 1. C Y B E R C A T C H A T T A C K E R S B E E F O R T H E Discover Assets Automatically discover all assets using network and endpoint footprints Assess Vulnerabilities Reduce attack surface by prioritizing vulnerabilities The challenge: Many Internet-facing systems have exploitable vulnerabilities Report Threats Provide actionable analytics to identify known and unknown threats PAYMENT CARDS 56M payment cards stolen Take Action ONLINE RETAIL customers’ data stolen Respond to vulnerabilities and threats before a breach occurs Sources: http://www.vmware.com/les/pdf/smb/Expand-Your-Virtual-Infrastructure-With-Condence-And-Control.pdf http://www.cxounplugged.com/wp-content/uploads/2012/11/BYOD_Infographic.png www.cioinsight.com/security/slideshows/shadow-it-growing-footprint.html Y 71% growth in virtual infrastructure over 5 years 65% of employees not satisfied with virtual machine security VIRTUAL 59% of employees use personal device for job 46% BYODs are unmanaged MOBILE 49% businesses use unapproved SaaS apps ??? cannot tell who is accessing unapproved SaaS apps and leaking data CLOUD 145M FINANCIAL http://www.bloomberg.com/news/2014-04-11/millions-of-android-devices-vulnerable-to-heartbleed-bug.html http://www.washingtonpost.com/news/morning-mix/wp/2014/09/26/shellshock-bug-aects-macs-and-many-other-internet-connected-devices/ https://ics-cert.us-cert.gov/sites/default/les/Monitors/ICS-CERT_Monitor_%20Jan-April2014.pdf Network devices vulnerable to Heartbleed 90M Internet-facing machines exposed to Shellshock 70% Vulnerabilities in SCADA devices are exploitable remotely 87% C A T C H Y O U Best Practices For Vulnerability Threat Monitoring The challenge: Not all network assets are known or managed The challenge: Suspicious activity in endpoints and network trac goes undetected The challenge: Takes too long to discover and respond to breaches Uncertainty Resolved with Continuous Monitoring Discover Assets, Assess Vulnerabilities, Report Threats Take Action. Learn More: tenable.com/dart 83M customers’ data stolen
