Aircrack windows web
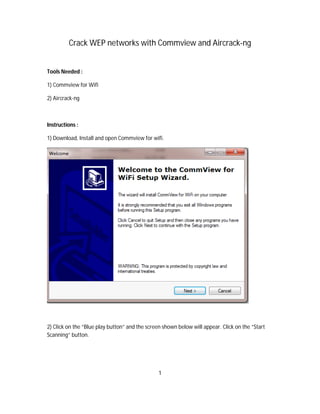
- 1. Crack WEP networks with Commview and Aircrack-ng Tools Needed : 1) Commview for Wifi 2) Aircrack-ng Instructions : 1) Download, Install and open Commview for wifi. 2) Click on the “Blue play button” and the screen shown below will appear. Click on the “Start Scanning” button. 1
- 2. 3) Now as all the available networks start to load, look for your target. Click on your target network (Make sure its WEP) and proceed to press the “Capture” button. (Shown Below) 2
- 3. 4) Now you will see the screen shown below as they collect packets. I have read tutorials claiming that a minimum of 5000 packets is needed. But in my experience, iv had to collect at least 15,000 packets before successfully cracking it. Note : The packets are secondary, What is actually happening here is that we are trying to collect as much IVs (Initialization vector) from those retrieved packets. The more IVs collected the higher the chance of cracking it. So if you collected 5000 packets but have shit loads of IVs in them, Then that is all you will need. But if the IVs is limited then you might have to go for 15,000 3
- 4. +++++++ packets. Do the Math. 5) Now that i have collected around 50,000 packets, i proceed to click on the “blue stop button.” Next click on the “Logging” tab to check where the packets were saved on your hard drive. In my case its saved on my desktop. Or if you prefer in the future do this setting before starting. (Shown Below) 6) Now minimize Commview and locate the logged packets on your hard drive. Once you have found it, double click on it and a screen will appear. Click “File”, “Save as” and change the output file to “WireShark/TCPDump” and press save. 7) Now lets proceed to “aircrack-ng.zip” and unzip the folder to your desktop. 4
- 5. 8) Double click on the extracted folder and locate the bin folder within. 9) Once you are inside the bin folder, locate the file Aircrack-ng-GUI.exe and double click on it. The screen shown below will appear. 10) Click on the “Choose Button” and direct it to your Wireshark file that you just saved a minute ago. 11) Lets keep the Encryption type to “WEP”. 12) Key Size : 128 13) Now proceed to press on the launch button. A command prompt will appear, allow it to fully load . 14) Index number of target network? In my case i key in 1 and press enter. 15) The screen shown below will appear, sit back and wait for it to do its magic. And before you know it! Voila! 5
- 6. Congratulations! We have successfully cracked the WEP password ! Contributed By James (www.jameslovecomputers.wordpress.com) 6
