Network Security(MD5)
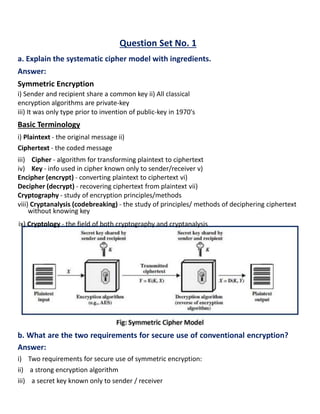
- 1. Question Set No. 1 a. Explain the systematic cipher model with ingredients. Answer: Symmetric Encryption i) Sender and recipient share a common key ii) All classical encryption algorithms are private-key iii) It was only type prior to invention of public-key in 1970's Basic Terminology i) Plaintext - the original message ii) Ciphertext - the coded message iii) Cipher - algorithm for transforming plaintext to ciphertext iv) Key - info used in cipher known only to sender/receiver v) Encipher (encrypt) - converting plaintext to ciphertext vi) Decipher (decrypt) - recovering ciphertext from plaintext vii) Cryptography - study of encryption principles/methods viii) Cryptanalysis (codebreaking) - the study of principles/ methods of deciphering ciphertext without knowing key ix) Cryptology - the field of both cryptography and cryptanalysis b. What are the two requirements for secure use of conventional encryption? Answer: i) Two requirements for secure use of symmetric encryption: ii) a strong encryption algorithm iii) a secret key known only to sender / receiver
- 2. a. Y = EK(X) b. X = DK(Y) iv) Assume encryption algorithm is known v) Implies a secure channel to distribute key c. Mention the dimension of cryptography Answer: Cryptographic systems are characterized along three independent dimensions 1) Type of encryption operations used □ Substitution: In which each element in the plaintext (bit, letter, group of bits or letters) is mapped into another element □ Transposition: In which elements in the plaintext are rearranged □ Product: Involve multiple stages of substitutions and transpositions 2) Number of keys used □ Single-key or private: If both sender and receiver use the same key, the system is referred to as symmetric, single-key, secret-key, or conventional encryption. □ Two-key or public: If the sender and receiver use different keys, the system is referred to as asymmetric, two-key, or public-key encryption. 3) Way in which plaintext is processed □ block / stream A block cipher processes the input one block of elements at a time, producing an output block for each input block. A stream cipher processes the input elements continuously, producing output one element at a time, as it goes along. d. Briefly explain cryptanalysis and brute-force attack. Answer: Cryptanalysis i) Only have 26 possible ciphers □ A maps to A, B,...Z ii) Could simply try each in turn iii) A brute force search iv) Given ciphertext, just try all shifts of letters v) Do need to recognize when have plaintext
- 3. e.g. break ciphertext "GCUA VQ DTGCM" Brute-force attack i) Always possible to simply try every key ii) Most basic attack, proportional to key size iii) Assume either know / recognize plaintext e. Mention the types of attacks on encrypted messages. Answer: i) Ciphertext only □ only know algorithm / ciphertext, statistical, can identify plaintext ii) Known plaintext □ know/suspect plaintext & ciphertext to attack cipher iii) Chosen plaintext □ select plaintext and obtain ciphertext to attack cipher iv) Chosen ciphertext □ select ciphertext and obtain plaintext to attack cipher v) Chosen text □ select either plaintext or ciphertext to en/decrypt to attack cipher Question Set No. 3 a. Explain the silent features of AES. Answer: The features of AES are as follows - i) Private Key symmetric block cipher ii) 128-bit data, 128/192/256-bit keys iii) Stronger & faster than Triple-DES iv) Active life of 20-30 years (+ archival use) v) Provide full specification & design details vi) Both C & Java implementations
- 4. vii) NIST have released all submissions & unclassified analyses b. Mention AES key parameters and the characteristics of Rijndael AES. Answer: AES key parameters i) initial criteria: a. security - effort for practical cryptanalysis b. cost - in terms of computational efficiency c. algorithm & implementation characteristics ii) final criteria a. general security b. ease of software & hardware implementation c. implementation attacks d. flexibility (in en/decrypt, keying, other factors) e. The characteristics of Rijndael AES is given below: i) designed by Rijmen-Daemen in Belgium ii) has 128/192/256 bit keys, 128 bit data iii) an iterative rather than feistel cipher a. treats data in 4 groups of 4 bytes b. operates an entire block in every round iv) designed to be: a. resistant against known attacks b. speed and code compactness on many CPUs c. design simplicity v) processes data as 4 groups of 4 bytes (state) vi) has 9/11/13 rounds in which state undergoes: a. byte substitution (1 S-box used on every byte) b. shift rows (permute bytes between groups/columns) c. mix columns (subs using matrix multiply of groups) d. add round key (XOR state with key material)
- 5. vii) initial XOR key material & incomplete last round viii) ix) all operations can be combined into XOR and table lookups - hence very fast & efficient c. Briefly explain Triple DES encryption and decryption process.
- 6. Answer: Triple DES i) Clear a replacement for DES was needed a. theoretical attacks that can break it b. demonstrated exhaustive key search attacks ii) AES is a new cipher alternative iii) Prior to this alternative was to use multiple encryption with DES implementations iv) TripleDES is the chosen form Triple-DES with Two-Keys i) Hence must use 3 encryptions a. would seem to need 3 distinct keys ii) But can use 2 keys with E-D-E sequence a. C = EK1[DK2[EK1[P]]] b. nb encrypt & decrypt equivalent in security c. if K1=K2 then can work with single DES iii) Standardized in ANSI X9.17 & ISO8732 iv) No current known practical attacks Triple-DES with Three-Keys i) Although are no practical attacks on two-key Triple-DES have some indications ii) Can use Triple-DES with Three-Keys to avoid even these a. C = EK3[DK2[EK1[P]]] iii) Has been adopted by some Internet applications, eg PGP, S/MIME
- 7. d. Explain the key distribution process. Answer: Key Distribution i) Symmetric schemes require both parties to share a common secret key ii) Issue is how to securely distribute this key iii) Often secure system failure due to a break in the key distribution scheme
- 8. - Nonce is also sent - Nonce includes identities of communicating parties and a unique value 2. KDC sends a response encrypted with A's secret key KA - It includes onetime session key KS - Original request message, including the nonce - Message also includes KS and ID of A encrypted with KB intended for B 3. A stores KS and forwards information for B i.e., EKB[KS|| IDA] 4. B sends a nonce to A encrypted with KS 5. A responds by performing some function on nonce like incrementing The last two steps assure B that the message it received was not a replay
- 9. Question Set No. 8 a. Explain MD5 algorithm and mention the strength of MD5 Answer: MD5 i) designed by Ronald Rivest (the R in RSA) ii) latest in a series of MD2, MD4 iii) produces a 128-bit hash value iv) until recently was the most widely used hash algorithm v) specified as Internet standard RFC1321 MD5 algorithm 1. pad message so its length is 448 mod 512 2. Append a 64-bit length value to message 3. initialize 4-word (128-bit) MD buffer (A,B,C,D) 4. process message in 16-word (512-bit) blocks: - using 4 rounds of 16 bit operations on message block & buffer - add output to buffer input to form new buffer value 5. Output hash value is the final buffer value
- 10. Strength of MD5 i) MD5 hash is dependent on all message bits ii) Rivest claims security is good as can be iii) known attacks are: a. Berson 92 attacked any 1 round using differential cryptanalysis (but can't extend) b. Boer & Bosselaers 93 found a pseudo collision (again unable to extend) c. Dobbertin 96 created collisions on MD compression function (but initial constants prevent exploit) iv) Conclusion is that MD5 looks vulnerable soon
- 11. b. Mention the comparison between MD5, SHA-1 & RIPEMD-160 Answer: Comparison of Popular Hash Functions Hash Func. MD5 SHA1 RMD160 HAS160 Digest size(bits) 128 160 160 160 Block size(bits) 512 512 512 512 No of steps 64(4x16) 80(4x20) 160(5x2x16) 80(4x20) Boolean func. 4 4(3) 5 4(3) Constants 64 4 9 4 Endianness Little Big Little Little Speed ratio 1.0 0.57 0.5 0.94
