Remove Backdoor.Streamex with SpyHunter
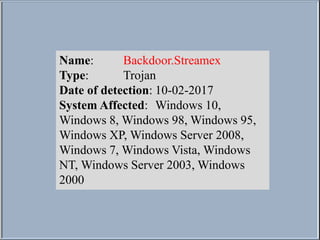
- 1. Name: Backdoor.Streamex Type: Trojan Date of detection: 10-02-2017 System Affected: Windows 10, Windows 8, Windows 98, Windows 95, Windows XP, Windows Server 2008, Windows 7, Windows Vista, Windows NT, Windows Server 2003, Windows 2000
- 2. Slow Internet Connection Modification in registry folder Open backdoor Hijacked search results Hijacked homepage Sluggish Respond of software Strange Icons on desktop and/or taskbar Tons of pop ups Sponsored ads with redirect links Crashing OS frequently Symptoms of Backdoor.Streamex
- 3. Only two known methods to get rid of Backdoor.Streamex completely from PC: Step 1: Manual method Step 2: Automatic method (Recommended) Removal Methods for Backdoor.Streamex
- 4. Manual method to remove Backdoor.Streamex includes several different steps that captures entire PC section including registry folder and start up folder. Few steps to get rid of Backdoor.Streamex infection from PC: -Uninstall harmful and unknown programs from control panel - Remove additional programs from start up list -Clean desktop by removing additional shortcuts -Clear registries by deleting malicious executables - Clear browsers by setting them up to correct domains Manual Methods for Backdoor.Streamex
- 5. Step 1: Uninstall Trojan from control panel On any windows, simply go to control panel and then programs and features. Search for new and irrelevant installation and double click on that to uninstall. Manual Methods for Backdoor.Streamex
- 6. Step 1: Uninstall Trojan from control panel Manual Methods for Backdoor.Streamex
- 7. Step 2: Remove additional program from Start up Click Ctrl+Shift+esc to open task manager. Shift the tab to startup and disable unexpected program. Manual Methods for Backdoor.Streamex
- 8. Step 2: Remove additional program from Start up Manual Methods for Backdoor.Streamex
- 9. Step 3: Clear Registry Folder by removing additional attachments Click windows button+r, then type regedit. Now delete the programs you find related with Trojan infection. Manual Methods for Backdoor.Streamex
- 10. Step 4: Reset all installed affected browsers by settings their homepage and default search provider to genuine location. Manual Methods for Backdoor.Streamex
- 11. Automatic method is recommend solution to get rid of Backdoor.Streamex infection completely. You need to download free security provider SpyHunter by clicking here. It is proven solution to provide PC security in future also. Automatic Method for Backdoor.Streamex Download SpyHunter
- 12. After Downloading, double click on exe file and click yes to continue Automatic Method for Backdoor.Streamex Download SpyHunter
- 13. Choose language Automatic Method for Backdoor.Streamex
- 14. To proceed the installation, click continue button Automatic Method for Backdoor.Streamex
- 15. Read and accept, end user license agreement and click Install button Automatic Method for Backdoor.Streamex
- 16. Click Finish on last step. Automatic Method for Backdoor.Streamex
- 17. Take Step to Remove Backdoor.Streamex Permanents and Give Future Security to Your PC Thanks for Watching