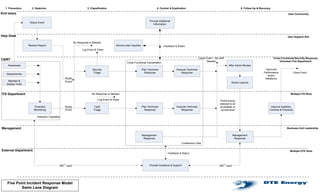
Incident Response Swimlanes
- 1. 1. Prevention 2. Detection 3. Classification 4. Control & Eradication 5. Follow Up & Recovery End Users User Community Provide Additional Notice Event Information Help Desk User Support Silo No Response is Needed Receive Report Service User Inquiries Feedback & Status Log Event & Close Close Event – No AAR Cross Functional Security Response CSIRT Needed Volunteer Fire Department Cross Functional Coordination Awareness After Action Review Security Plan Technical Execute Technical Improved Triage Response Response Performance Close Event Assessments and/or Route Resiliency Maintain & Event Share Lessons Deploy Tools ITS Department No Response is Needed Multiple ITS Silos Log Event & Close Performance restored to an Proactive Route Fault Plan Technical Execute Technical acceptable or Improve Systems, Monitoring Event Triage Response Response normal level Controls & Practices Detection Capability Management Business Unit Leadership Management Management Response Response Conference Calls External Department Multiple DTE Silos Feedback & Status 360° Input Provide Guidance & Support 360° Input Five Point Incident Response Model Swim Lane Diagram
