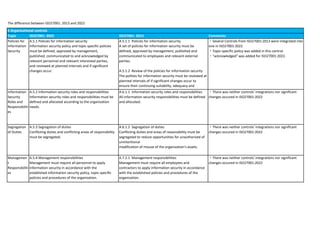
My Gap analysis results between ISO27001: 2022 and 2013 version as of 2022 fall.
- 1. Topic ISO27001: 2022 ISO27001: 2013 Comments Policies for Information Security A.5.1 Policies for information security Information security policy and topic-specific policies must be defined, approved by management, published, communicated to and acknowledged by relevant personnel and relevant interested parties, and reviewed at planned intervals and if significant changes occur. A.5.1.1 Policies for information security A set of policies for information security must be defined, approved by management, published and communicated to employees and relevant external parties. A.5.1.2 Review of the policies for information security The polities for information security must be reviewed at planned intervals of if significant changes occur to ensure their continuing suitability, adequacy and ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. ・Topic-specific policy was added in this control. ・"acknowledged" was added for ISO27001:2022. Information Security Roles and Responsibiliti es A.5.2 Information security roles and responsibilities Information security roles and responsibilities must be defined and allocated according to the organization needs. A.6.1.1 Information security roles and responsibilities All information security responsibilities must be defined and allocated. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Segregation of Duties A.5.3 Segregation of duties Conflicting duties and conflicting areas of responsibility must be segregated. A.6.1.2 Segregation of duties Conflicting duties and areas of reasonability must be segregated to reduce opportunities for unauthorized of unintentional modification of misuse of the organization's assets. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Managemen t Responsibiliti es A.5.4 Management responsibilities Management must require all personnel to apply information security in accordance with the established information security policy, topic-specific policies and procedures of the organization. A.7.2.1 Management responsibilities Management must require all employees and contractors to apply information security in accordance with the established policies and procedures of the organization. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 5 Organizational controls The difference between ISO27001: 2013 and 2022
- 2. Contact with Authorities A.5.5 Contact with authorities The organization must establish and maintain contact with relevant authorities. A.6.1.3 Contact with authorities 【CLOUD】 Appropriate contacts with relevant authorities must be maintained. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Contact with Special Interest Groups A.5.6 Contact with specialinterest groups The organization must establish and maintain contact with special interest groups or other specialist security forums and professional associations. A.6.1.4 Contact with special interest groups Appropriate contacts with special interest groups or other specialist security forms and professional associations must be maintained. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Threat Intelligence A.5.7 Threat intelligence Information relating to information security threats must be collected and analysed to produce threat intelligence. none ・Significant Changes in ISO27001:2022. ・None from ISO27001:2013 is relevant to this control in ISO27001:2022. ・Cybersecurity topic was added from ISO27001:2022. Information Security in Project Managemen t A.5.8 Information security in project management Information security must be integrated into project management. A.6.1.5 Information security in project management Information security must be addressed in project management,regardless of the type of the project. A.14.1.1 Information security requirements analysis and specification 【CLOUD】 The information security related requirements must be included in the requirements for information systems or enhancements to existing information systems ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. Inventory of Information and Other Associated Assets A.5.9 Inventory of information and other associated assets An inventory of information and other associated assets, including owners, must be developed and maintained. A.8.1.1 Inventory of assets 【CLOUD】 Information,other assets associated with information and information processing facilities must be identified and an inventory of these assets must be drawn up and maintained. A.8.1.2 Ownership of assets Assets maintained in the inventory must be owned ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022.
- 3. Acceptable Use of Information and Other Associated Assets A.5.10 Acceptable use of information and other associated assets Rules for the acceptable use and procedures for handling information and other associated assets must be identified, documented and implemented. A.8.1.3 Acceptable use of assets Rules for the acceptable use of information and of assets associated with information and information processing facilities must be identified, documented and implemented A.8.2.3 Handling of assets Procedures for handling assets must be developed and implemented in accordance with the information classification scheme adopted by the organization ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. Return of Assets A.5.11 Return of assets Personnel and other interested parties as appropriate must return all the organization’s assets in their possession upon change or termination of their employment, contract or agreement. A.8.1.4 Return of assets All employees and external party users must return all of the organizational assets in their possession upon termination of their employment, contract or agreement. ・"upon change" was added to "termination, Contract or agreement" to add change management aspect on ISO27001:2022. Classification of Information A.5.12 Classification of information Information must be classified according to the information security needs of the organization based on confidentiality, integrity, availability and relevant interested party requirements to ensure identification and understanding of protection needs of information in accordance with its importance to the organization. A.8.2.1 Classification of information Information must be classified in terms of legal requirements, value, criticality and sensitivity to unauthorized disclosure or modification. ・CIA is clearly stated in ISO27001:2022 Labelling of Information 5.13 Labelling of information An appropriate set of procedures for information labelling must be developed and implemented in accordance with the information classification scheme adopted by the organization. A.8.2.2 Labelling of information 【CLOUD】 An appropriate set of procedures for information labeling must be developed and implemented in accordance with the information classification scheme adopted by the organization. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022
- 4. Information Transfer A.5.14 Information transferInformation transfer rules, procedures, or agreements must be in place for all types of transfer facilities within the organization and between the organization and other parties. A.13.2.1 Information transfer policies and procedures Formal transfer policies, procedures and controls must be in place to protect the transfer of information thru the use of all types of communication facilities. A.13.2.2 Agreements on information transfer Agreements must address the secure transfer of business information bet the organization and external parties. A.13.2.3 Electronic messagingInformation involved in electronic messaging must be appropriately protected. ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. Access Control A.5.15 Access control Rules to control physical and logical access to information and other associated assets must be established and implemented based on business and information security requirements. A.9.1.1 Access control policy An access control policy must be established, documented and reviewed based on business and information security requirements. A.9.1.2 Access to networks and network services 【CLOUD】 Users must only be provided with access to the network and network services that they have been specifically authorized to use. ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. Identity Managemen t A.5.16 Identity managementThe full life cycle of identities must be managed. A.9.2.1 User registration and de-registration 【CLOUD】 A formal user registration and de- registration process must be implemented to enable assignment of access rights ・There was neither controls' integrations nor significant changes occured in ISO27001:2022
- 5. Authenticati on Information A.5.17 Authentication information Allocation and management of authentication information must be controlled by a management process,including advising personnel on the appropriate handling of authentication information. A.9.2.4 Management of secret authentication information of users 【CLOUD】 The allocation of secret authentication information must be controlled thru a formal management process. A.9.3.1Use of secret authentication information Users must be required to follow the organization's practices in the use of secret authentication information. A.9.4.3 Password management system Password management system must be interactive and must ensure quality passwords ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. Access Rights A.5.18 Access rights Access rights to information and other associated assets must be provisioned, reviewed, modified and removed in accordance with the organization’s topic- specific policy on and rules for access control. A.9.2.2 User access provisioning 【CLOUD】 A formal user access provisioning process must be implemented to assign or revoke access rights for all user types to all systems and services. A.9.2.5 Review of user access rights.Asset owners must review users' access rights at regular intervals. A.9.2.6 Removal or adjustment of access rights The access rights of all employees and external party users to information and information processing facilities must be removed upon termination of their employment, contract, contract or agreement, or ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. ・Topic-specific policy was added in this control. Information Security in Supplier Relationships A.5.19 Information security in supplier relationships Processes and procedures must be defined and implemented to manage the information security risks associated with the use of suppliers products or services. A.15.1.1 Information security policy for supplier relationships. 【CLOUD】 Information security requirements for mitigating the risks associated with supplier's access to the organization's assets must be agreed with the supplier and documented. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022
- 6. Addressing Information Security within Supplier Agreements A.5.20 Addressing information security within supplier agreementsRelevant information security requirements must be established and agreed with each supplier based on the type of supplier relationship. A.15.1.2 Addressing security within supplier agreements 【CLOUD】 All relevant information security requirements must be established and agreed with each supplier that may access, process, store, communicate, or provide IT infrastructure components form the organization's information. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Managing Information Security in the ICT Supply Chain A.5.21 Managing information security in the ICT supply chain Processes and procedures must be defined and implemented to manage the information security risks associated with the ICT products and services supply chain. A.15.1.3 Information and communication tech supply chain 【CLOUD】 Agreements with suppliers must include requirements to address the information security risks associated with information and communications tech services and product supply chain. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Monitoring, Review and Change Managemen t of Supplier Services A.5.22 Monitoring, review and change management of supplier services The organization must regularly monitor, review, evaluate and manage change in supplier information security practices and service delivery. A.15.2.1 Monitoring and review of supplier services Organizations must regularly monitor, review and audit supplier service delivery. A.15.2.2 Managing changes to supplier services Changes to the provision of services by suppliers, including maintaining and improving existing information security policies, procedures and controls, must be managed, taking account of the criticality if business information, systems and processes involved and re- assessment of risks. ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. ・"audit" was removed from controls in ISO27001:2022; however, it was still included in its guidance. Information Security for Use of Cloud Services A.5.23 Information security for use of cloud【CLOUD】 servicesProcesses for acquisition, use, management and exit from cloud services must be established in accordance with the organization’s information security requirements. none ・Significant Changes on in ISO27001:2022. ・None from ISO27001:2013 is relevant to this control in ISO27001:2022. ・Cloud Technologies are newly added to ISO27001:2022. ・This control may be originated from ISO27017.
- 7. Information Security Incident Managemen t Planning and Preparation A.5.24 Information security incident management planning and preparation The organization must plan and prepare for managing information security incidents by defining,establishing and communicating information security incident management processes, roles and responsibilities. A.16.1.1 Responsibilities and procedures 【CLOUD】 Management responsibilities and procedures must be established to ensure a quick, effective and orderly response to information security incidents. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 ・However,the competency, training and certifications towards incidents response personnel is focused as well as the roles and responsibilities in a guidance. Assessment and Decision on Information Security Events A.5.25 Assessment and decision on information security events The organization must assess information security events and decide if they are to be categorized as information security incidents. A.16.1.4 Assessment of and decision on information security events Information security events must be assessed and it must be decided if they are to be classified as information security incidents. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Response to Information Security Incidents A.5.26 Response to information security incidentsInformation security incidents must be responded to in accordance with the documented procedures. A.16.1.5 Response to information security incidents Information security incidents must be responded to in accordance with the documented procedures. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Learning from Information Security Incidents A.5.27 Learning from information security incidents Knowledge gained from information security incidents must be used to strengthen and improve the information security controls. A.16.1.6 Learning from information security incidents Knowledge gained from analyzing and resolving and resolving information security incidents must be used to reduce the likelihood or impact of secuerity incidents. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Collection of Evidence A.5.28 Collection of evidence The organization must establish and implement procedures for the identification, collection,acquisition and preservation of evidence related to information security events. A.16.1.7 Collection of evidence 【CLOUD】 The organization must define and apply procedures for the identification, collection, acquisition and preservation of information, which can serve as evidence. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022
- 8. Information Security during Disruption A.5.29 Information security during a disruption The organization must plan how to maintain information security at an appropriate level during a disruption. A.17.1.1 Planning information security continuity The organization must determine its requirements for information security and the continuity of information security management in adverse situations, e.g. during a crisis or disaster. A.17.1.2 Implementing information security continuity The organization must establish, document, implement and maintain processes, procedures and controls to ensure the required level of continuity for information security during an adverse situation. A.17.1.3 Verify, review and evaluation information security continuity The organization must verify the established and implemented information security continuity controls at regular intervals in order to ensure that they are valid and effective during adverse situations. ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. ICT Readiness for Business Continuity A.5.30 ICT readiness for business continuity ICT readiness must be planned, implemented, maintained and tested based on business continuity objectives and ICT continuity requirements. none ・Significant Changes in ISO27001:2022. ・None from ISO27001:2013 is relevant to this control in ISO27001:2022. ・Conducting BIA(Business Impact Analysis) was added to ISO27001:2022 guidance. ・BIA in a guidance would be originated from ISO22301(Business Continuity Management System)
- 9. Legal, Statutory, Regulatory and Contractual Requirement s A.5.31 Legal, statutory, regulatory and contractual requirements Legal, statutory, regulatory and contractual requirements relevant to information security and the organizations approach to meet these requirements must be identified,documented and kept up to date. A.18.1.1 Identification of applicable legislation and contractual requirements 【CLOUD】 A.18.1.5 Regulation of cryptographic controls 【CLOUD】 Cryptographic controls must be used in compliance with all relevant agreements, legislation and regulations. ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. ・"validity of digital signatures, seals and certificates, encrypted information or cryptography tools across jurisdictional borders" is in a guidance for 2022 version. Intellectual Property Rights A.5.32 Intellectual property rights The organization must implement appropriate procedures to protect intellectual property rights to ensure compliance with legal, statutory, regulatory and contractual requirements, as well as community or societal expectations related to the protection and availability of records. A.18.1.2 Intellectual property rights 【CLOUD】 Appropriate procedures must be implemented to ensure compliance with legislative, regulatory and contractual requirements related to intellectual property rights and use of proprietary software products. ・"community or societal expectations" was added to compliance with legal, statutory, regulatory and contractual requirements. Protection of records A.5.33 Protection of records Records must be protected from loss, destruction, falsification, unauthorized access and unauthorized release to ensure compliance with legal, statutory, regulatory and contractual requirements, as well as community or societal expectations related to the protection and availability of records. A.18.1.3 Protection of records 【CLOUD】 Records must be protected form loss, destruction, falsification, unauthorized access and unauthorized release, in accordance with legislatory, regulatory, contractual and business requirements. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 ・Topic-specific policy was added in this control. ・"personnel records", "metadata", and "chain of custody" were added in guidance. ・"community or societal expectations" were added to legislatory, regulatory, contractual and business requirements.
- 10. Privacy and Protection of PII(Personall y Identifiable Information) A.5.34 Privacy and protection of PII The organization must identify and meet the requirements regarding the preservation of privacy and protection of PII according to applicable laws and regulations and contractual requirements. A.18.1.4 Privacy and protection of personally identifiable information 【CLOUD】 Privacy and protection of personally identifiable information must be ensured as required in relevant legislation and regulation where applicable. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 ・"contractual requirements" was added to "legislation and regulation". Independent Review of Information Security A.5.35 Independent review of information security The organization’s approach to managing information security and its implementation including people, processes and technologies must be reviewed independently at planned intervals, or when significant changes occur. A.18.2.1 Independent review of information security 【CLOUD】 The organization's approach to managing information security and its implementation(i.e. control objectives, controls, policies, processes and procedures for information security) must be reviewed independently at planned intervals or when significant changes occur. ・"people,processes and technologies" was added or changed to "control objectives, controls, policies, processes and procedures". Compliance with Policies, Rules and Standards for Information Security A.5.36 Compliance with policies, rules and standards for information security Compliance with the organization’s information security policy, topic-specific policies, rules and standards must be regularly reviewed to ensure that information security is implemented and operated in accordance with the organization's information security policy,topic-specific policies,rules and standards. A.18.2.2 Compliance with security policies and standard Managers must regularly review the compliance of information processing and procedures within their area of responsibility with the appropriate security policies, standards and any other security requirements. A.18.2.3 Technical compliance review Information systems must be regularly reviewed for compliance with the organization's information security policies and standards. ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. ・Topic-specific policy was added in this control. ・"rules" is added to "security policies, standards and any other security requirements". Documented Operating Procedures A.5.37 Documented operating procedures Operating procedures for information processing facilities must be documented and made available to personnel who need them to ensure the correct and secure operation of information processing facilities. A.12.1.1 Documented operating procedures Operating procedures must be documented and made available to all users who need them. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 ・"all users who need them" was replaced with "Personnel who need them". Topic ISO27001: 2022 ISO27001: 2013 Comments 6 People controls
- 11. Screening A.6.1 Screening Background verification checks on all candidates to become personnel must be carried out prior to joining the organization and on an ongoing basis taking into consideration applicable laws, regulations and ethics and be proportional to the business requirements, the classification of the information to be accessed and the perceived risks to ensure all personnel are eligible and suitable for the roles for which they are considered and remain eligible and suitable during their employment. A.7.1.1 Screening Background verification checks on all candidates for employments must be carried out in accordance with relevant laws, regulations and ethics and must be proportional to the business requirements, the classification of the information to be accessed and the perceived risks. ・"All candidates for employment" was replaced with "all candidates to become personnel". Terms and Conditions of Employment A.6.2 Terms and conditions of employment The employment contractual agreements must state the personnel’s and the organization’s responsibilities for information security. Purpose to ensure personnel understand their information security responsibilities for the roles for which they are considered. A.7.1.2 Terms and conditions of employment The contractual agreements with employees and contractors must state their and the organizations' responsibilities for information security. ・"employees and contractors" was replaced with "personnel". Information Security Awareness, Education and Training A.6.3 Information security awareness, education and training Personnel of the organization and relevant interested parties must receive appropriate information security awareness, education and training and regular updates of the organization's information security policy, topic-specific policies and procedures, as relevant for their job function to ensure personnel and relevant interested parties are aware of and fulfil their information security responsibilities. A.7.2.2 Information security awareness, education and training 【CLOUD】 All employment of the organization and, where relevance contractors must receive appropriate awareness education and training and regular updates in organizational policies and procedures, as relevant for their job function. ・Topic-specific policy was added in this control. ・"contractors" was replaced with "Relevant Interested Parties".
- 12. Disciplinary Process A.6.4 Disciplinary process A disciplinary process must be formalized and communicated to take actions against personnel and other relevant interested parties who have committed an information security policy violation to ensure personnel and other relevant interested parties understand the consequences of information security policy violation, to deter and appropriately deal with personnel and other relevant interested parties who committed the violation. A.7.3.1 Termination or change of employment responsibilities Information security responsibilities and duties that remain valid after termination of change of employment must be defied, communicated to the employee or contractor and enforced. ・"the employee or contractor" was replaced with "personnel and other relevant interested parties". Responsibiliti es after Termination or Change of Employment A.6.5 Responsibilities after termination or change of employment Information security responsibilities and duties that remain valid after termination or change of employment must be defined, enforced and communicated to relevant personnel and other interested parties to protect the organization’s interests as part of the process of changing or terminating employment contracts. A.7.3.1 Termination or change of employment responsibilities Information security responsibilities and duties that remain valid after termination of change of employment must be defied, communicated to the employee or contractor and enforced. ・"the employee or contractor" was replaced with "personnel and other relevant interested parties". Confidentiali ty or Non- Disclosure Agreements (NDA) A.6.6 Confidentiality or non-disclosure agreements Confidentiality or non-disclosure agreements reflecting the organization’s needs for the protection of information must be identified, documented, regularly reviewed and signed by personnel and other relevant interested parties to maintain confidentiality of information accessible by personnel or external parties. A.13.2.4 Confidentiality or non-disclosure agreements Requirements for confidentiality or non- disclosure agreements reflecting the organization's needs for the protection of information must be identified, regularly reviewed and documented. ・"signed by personnel" in the only guidance for the 2013 version was newly added to control in ISO27001:2022.
- 13. Remote Working A.6.7 Remote working Security measures must be implemented when personnel are working remotely to protect information accessed, processed or stored outside the organization’s premises to ensure the security of information when personnel are working remotely. A.6.2.2 Teleworking A policy and supporting security measures must be implemented to protect information accessed, processed or stored at teleworking sites. ・Significant change. ・"teleworking" replaced with "remote working" which includes “teleworking",“telecommuting”,“flexible workplace",“virtual work environments" and “remote maintenance”. Information Security Event Reporting A.6.8 Information security event reporting The organization must provide a mechanism for personnel to report observed or suspected information security events through appropriate channels in a timely manner to support timely, consistent and effective reporting of information security events that can be identified by personnel. A.16.1.2 Reporting information security weaknesses 【CLOUD】 Information security events must be reported thru appropriated management channels as quickly as possible. A.16.1.3 Reporting information security weaknesses Employees and contractors using the organization's information systems and services must be required to note and report any observed or suspected information ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. ・"the employee or contractor" was replaced with "personnel". Topic ISO27001: 2022 ISO27001: 2013 Comments Physical Controls A.7 Physical controls Security perimeters must be defined and used to protect areas that contain information and other associated assets to prevent unauthorized physical access, damage and interference to the organization’s information and other associated assets. A.11.1.1 Physical security perimeter Security perimeters must be defied and used to protect areas that contain either sensitive or critical information and information processing facilities. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022. 7.Physical Controls
- 14. Physical Entry A.7.2 Physical entry Secure areas must be protected by appropriate entry controls and access points to ensure only authorized physical access to the organization’s information and other associated assets occurs. A.11.1.2 Physical entry controls Secure areas must be protected by appropriate entry controls to ensure that only authorized personnel are allowed access. A.11.1.6 Delivery and loading areas Access point such as delivery and loading areas and other points where unauthorized persons could enter the premises must be controlled and, if possible, isolated form information processing facilities to avoid unauthorized access. ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. Securing Offices, Rooms and Facilities A.7.3 Securing offices,rooms and facilities Physical security for offices, rooms and facilities must be designed and implemented to prevent unauthorized physical access, damage and interference to the organization’s information and other associated assets in offices, rooms and facilities. A.11.1.3 Securing offices, rooms and facilities Physical security for offices, rooms, and facilities must be designed and applied. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Physical Security Monitoring A.7.4 Physical security monitoring Premises must be continuously monitored for unauthorized physical access to detect and deter unauthorized physical access. none ・Significant Changes in ISO27001:2022. ・None from ISO27001:2013 is relevant to this control in ISO27001:2022.
- 15. Protecting Against Physical and Environment al Threats A.7.5 Protecting against physical and environmental threats Protection against physical and environmental threats, such as natural disasters and other intentional or unintentional physical threats to infrastructure must be designed and implemented to prevent or reduce the consequences of events originating from physical and environmental threats. A.11.1.4 Protecting against external and environmental threats Physical protection against natural disasters, malicious attack or accidents shall be designed and applied. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 ・Risk assessment for this contorol was added in the guidance. Working in Secure Areas A.7.6 Working in secure areas Security measures for working in secure areas must be designed and implemented to protect information and other associated assets in secure areas from damage and unauthorized interference by personnel working in these areas. A.11.1.5 Working in secure areas Procedures for working in secure areas must be designed and applied. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 A.7.7 Clear Desk and Clear Screen A.7.7 Clear desk and clear screen Clear desk rules for papers and removable storage media and clear screen rules for information processing facilities must be defined and appropriately enforced to reduce the risks of unauthorized access, loss of and damage to information on desks, screens and in other accessible locations during and outside normal working hours. A.11.2.9 Clear desk and clear screen policy A clear desk policy for papers and removable storage media and a clear screen policy for information processing facilities must be adopted, ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 ・New word for ISO27001:2022; "Topic-specific policy" is discussed in this control's guidance. Equipment Siting and Protection A.7.8 Equipment siting and protection Equipment must be sited securely and protected to reduce the risks from physical and environmental threats, and from unauthorized access and damage. A.11.2.1 Equipment siting and protection Equipment must be sited and protected to reduce the risks from env. Threats and hazards, and opportunities for unauthorized access. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022
- 16. Security of Assets Off- Premiss A.7.9 Security of assets off-premises Off-site assets must be protected to prevent loss, damage, theft or compromise of off-site devices and interruption to the organization’s operations. A.11.2.6 Security of equipment and assets off-premises Security must be applied to off-site assets taking into account the different risks of working outside the organization's premises. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Storage Media A.7.10 Storage media Storage media must be managed through their life cycle of acquisition, use, transportation and disposal in accordance with the organization’s classification scheme and handling requirements to ensure only authorized disclosure, modification, removal or destruction of information on storage media. A.8.3.1 Management of removable media Procedures must be implemented for the management of removable media in accordance with the classification scheme adopted by the organization. A.8.3.2 Disposal of media Media must be disposed of securely when no longer required, using formal procedures. A.8.3.3 Physical media transfer Media containing information must be protected against unauthorized access, misuse or corruption during transportation. A.11.2.5 Removal of assets Equipment, information or software must not be taken off-site w/o prior authorization. ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. Supporting Utilities A.7.11 Supporting utilities Information processing facilities must be protected from power failures and other disruptions caused by failures in supporting utilities to prevent loss, damage or compromise of information and other associated assets, or interruption to the organization’s operations due to failure and disruption of supporting utilities. A.11.2.2 Supporting utilities Equipment must be protected from power failures and other disruptions caused by failures in supporting utilities. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022
- 17. Cabling Security A.7.12 Cabling security Cables carrying power, data or supporting information services must be protected from interception, interference or damage to prevent loss, damage, theft or compromise of information and other associated assets and interruption to the organization’s operations related to power and communications cabling. A.11.2.3 Cabling security Power and telecommunications cabling carrying data or supporting information services must be protected from interception, interference or damage. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Equipment Maintenance A.7.13 Equipment maintenance Equipment must be maintained correctly to ensure availability, integrity and confidentiality of information to prevent loss, damage, theft or compromise of information and other associated assets and interruption to the organization’s operations caused by lack of maintenance. A.11.2.4 Equipment maintenance Equipment must be correctly maintained to ensure its continued availability and integrity. ・Significant change. ・"Confidentiality" was added to "Integrity and Availability" for the CIA. Secure Disposal or Re-Use of Equipment A.7.14 Secure disposal or re-use of equipment Items of equipment containing storage media must be verified to ensure that any sensitive data and licensed software has been removed or securely overwritten prior to disposal or re-use to prevent leakage of information from equipment to be disposed or re-used. A.11.2.7 Secure disposal or re-use of equipment 【CLOUD】 All items of equipment containing storage media must be verified to ensure that any sensitive data and licensed software has been removed or securely overwritten prior to disposal or re-use. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Topic ISO27001: 2022 ISO27001: 2013 Comments 8 Technological controls
- 18. User Endpoint Devices A.8.1 User endpoint devicesInformation stored on, processed by or accessible via user endpoint devices must be protected to protect information against the risks introduced by using user endpoint devices. A.6.2.1 Mobile device policy A policy and supporting security measures must be adopted to manage the risks introduced by using mobile devices. A.11.2.8 Unattended user equipment Users must ensure that unattended equipment has appropriate protection. ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. ・New word for ISO27001:2022; "user endpoint devices", amd "Topic-specific policy" are discussed in this control's guidance. Privileged Access Rights A.8.2 Privileged access rights The allocation and use of privileged access rights must be restricted and managed to ensure only authorized users, software components and services are provided with privileged access rights A.9.2.3 Management of privileged access rights 【CLOUD】 特権的アクセス権の管理 The allocation and use of privileged access rights must be restricted and controlled. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Information Access Restriction A.8.3 Information access restriction Access to information and other associated assets must be restricted in accordance with the established topic-specific policy on access control to ensure only authorized access and to prevent unauthorized access to information and other associated assets. A.9.4.1 Information access restriction 【CLOUD】情報へのアクセス制御 Access to information and application system functions must be restricted in accordance with the access control policy. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 ・Topic-specific policy was added in this control. Access to Source Code A.8.4 Access to source code Read and write access to source code, development tools and software libraries must be appropriately managed to prevent the introduction of unauthorized functionality, avoid unintentional or malicious changes and to maintain the confidentiality of valuable intellectual property. A.9.4.5 Access control to program source code Access to program source code must be restricted. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022
- 19. Secure Authenticati on A.8.5 Secure authentication Secure authentication technologies and procedures must be implemented based on information access restrictions and the topic-specific policy on access control to ensure a user or an entity is securely authenticated, when access to systems, applications and services is granted. A.9.4.2 Secure log-on procedures Where required by the access control policy,access to systems and applications shall be controlled by a secure log-on procedure. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 ・Topic-specific policy was added in this control. Capacity management A.8.6 Capacity management The use of resources must be monitored and adjusted in line with current and expected capacity requirements to ensure the required capacity of information processing facilities, human resources, offices and other facilities. A.12.1.3 Capacity management 【CLOUD】容量・能力の管理 The use of resources must be monitored, tuned and projections made of future capacity requirements to ensure the required system performance. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Protection Against malware A.8.7 Protection against malware Protection against malware must be implemented and supported by appropriate user awareness to ensure information and other associated assets are protected against malware. A.12.2.1 Controls against malware Detection, prevention and recovery controls to protect against malware must be implemented, combined with appropriate user awareness. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Managemen t of Technical Vulnerabiliti es A.8.8 Management of technical vulnerabilities Information about technical vulnerabilities of information systems in use must be obtained, the organization's exposure to such vulnerabilities must be evaluated and appropriate measures must be taken to prevent exploitation of technical vulnerabilities. A.12.6.1 Management of technical vulnerabilities 【CLOUD】技術的ぜい弱性の管理 Information about technical vulnerabilities of information systems being used must be obtained in a timely fashion, the organization's exposure to such vulnerabilities evaluated and appropriate measures taken to address the associated risk, A.18.2.3 Technical compliance review Information systems must be regularly reviewed for compliance with the organization's information security ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022.
- 20. Configuratio n Mnagement A.8.9 Configuration management Configurations, including security configurations, of hardware, software, services and networks must be established, documented, implemented, monitored and reviewed to ensure hardware, software, services and networks function correctly with required security settings, and configuration is not altered by na thori ed or incorrect changes none ・Significant Changes in ISO27001:2022. ・None from ISO27001:2013 is relevant to this control in ISO27001:2022. ・This control may be originated from ISO20000-1:2018 (Service Management System),PCIDSS, NIST SP 800-53, GDPR,etc. Information Deletion A.8.10 Information deletionIn formation stored in information systems, devices or in any other storage media must be deleted when no longer required to prevent unnecessary exposure of sensitive information and to comply with legal, statutory regulatory and contractual requirements for none ・Significant Changes in ISO27001:2022. ・None from ISO27001:2013 is relevant to this control in ISO27001:2022. ・This control may be originated from PCIDSS, NIST SP 800- 53, GDPR,etc. Data masking A.8.11 Data masking control and other related topic- specific policies, and business requirements, taking applicable legislation into consideration to limit the exposure of sensitive data including PII, and to comply with legal, statutory, regulatory and contractual requirements. none ・Significant Changes in ISO27001:2022. ・None from ISO27001:2013 is relevant to this control in ISO27001:2022. ・This control may be originated from PCIDSS, NIST SP 800- 53, GDPR,etc. Data Leakage Prevention A.8.12 Data leakage prevention Data leakage prevention measures must be applied to systems, networks and any other devices that process, store or transmit sensitive information to detect and prevent the unauthorized disclosure and extraction of information by individuals or systems none ・Significant Changes in ISO27001:2022. ・None from ISO27001:2013 is relevant to this control in ISO27001:2022. ・This control may be originated from PCIDSS, NIST SP 800- 53, GDPR,etc. Information Backup A.8.13 Information backup Backup copies of information, software and systems must be maintained and regularly tested in accordance with the agreed topic-specific policy on backup to enable recovery from loss of data or systems. A.12.3.1 Information backup 【CLOUD】情報のバックアップ Backup copies of information, software and system images must be taken and tested regularly in accordance with an agreed backup policy. ・Topic-specific policy was added in this control. Redundancy of Information Processing Facilities A.8.14 Redundancy of information processing facilities Information processing facilities must be implemented with redundancy sufficient to meet availability requirements to ensure the continuous operation of information processing facilities. A.17.2.1 Availability or information processing facilities Information processing facilities must be implemented with redundancy sufficient to meet availability requirements. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022
- 21. Logging A.8.15 Logging Logs that record activities, exceptions, faults and other relevant events must be produced, stored, protected and analysed to record events, generate evidence, ensure the integrity of log information, prevent against unauthorized access, identify information security events that can lead to an information security incident and to support investigations. A.12.4.1 Event logging 【CLOUD】イベントログの取得 Event logs recording user activities, exceptions, faults and information security events must be produced, kept and regularly reviewed. A.12.4.2 Protection of log information Logging facilities and log information must be protected ageist tempering and unauthorized access. A.12.4.3 Administrator and operator logs 【CLOUD】 ・Significant changes ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. ・"Log analysis" was newly added to "Log review". ・This control may be originated from PCIDSS, NIST SP 800- 92. Monitoring Activities A.8.16 Monitoring activities Networks, systems and applications must be monitored for anomalous behaviour and appropriate actions taken to evaluate potential information security incidents to detect anomalous behaviour and potential information security incidents. none ・Significant Changes in ISO27001:2022. ・None from ISO27001:2013 is relevant to this control in ISO27001:2022. Clock Synchronizat ion A.8.17 Clock synchronization The clocks of information processing systems used by the organization must be synchronized to approved time sources to enable the correlation and analysis of security-related events and other recorded data, and to support investigations into information security incidents. A.12.4.4 Clock synchronization 【CLOUD】 The clocks of all relevant information processing systems within an organization or security domain must be synchronized to a single reference time source. ・Significant Changes in ISO27001:2022. ・"synchronized to a single reference time source" was changed to "synchronized to approved time sources". Use of Privileged Utility Programs A.8.18 Use of privileged utility programs The use of utility programs that can be capable of overriding system and application controls must be restricted and tightly controlled to ensure the use of utility programs does not harm system and application controls for information security. A.9.4.4 Use of privileged utility programs The use of utility programs that might be capable of overriding system and application controls must be restricted and tightly controlled. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022
- 22. Installation of Software on Operational Systems A.8.19 Installation of software on operational systems Procedures and measures must be implemented to securely manage software installation on operational systems to ensure the integrity of operational systems and prevent exploitation of technical vulnerabilities. A.12.5.1 Installation of software on operational systems Procedures must be implemented to control the installation of software on operational systems. A.12.6.1 Management of technical vulnerabilities 【CLOUD】 Information about technical vulnerabilities of information systems being used must be obtained in a timely fashion, the organization's exposure to such vulnerabilities evaluated and appropriate measures taken to address the associated risk. ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. Networks security A.8.20 Networks security Networks and network devices must be secured, managed and controlled to protect information in systems and applications.to protect information in networks and its supporting information processing facilities from compromise via the network. A.13.1.1 Network controls Networks must be managed and controlled to protect information in systems and applications. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Security of Network Services A.8.21 Security of network services Security mechanisms, service levels and service requirements of network services must be identified, implemented and monitored to ensure security in the use of network services. A.13.1.2 Security of network services Security mechanisms, service levels and management requirements of all network services must be identified and included in network services agreements, whether these services are provided in- house or outsourced. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Segregation of Networks A.8.22 Segregation of networks Groups of information services, users and information systems must be segregated in the organization’s networks to split the network in security boundaries and to control traffic between them based on business A.13.1.3 Segregation in networks 【CLOUD】ネットワークの分離 Groups of information services, users and information systems must be segregated on networks. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022
- 23. Web filtering A.8.23 Web filtering Access to external websites must be managed to reduce exposure to malicious content to protect systems from being compromised by malware and to prevent access to unauthorized web resources. none ・Significant Changes in ISO27001:2022. ・None from ISO27001:2013 is relevant to this control in ISO27001:2022. Use of Cryptograph y A.8.24 Use of cryptography Rules for the effective use of cryptography, including cryptographic key management, must be defined and implemented to ensure proper and effective use of cryptography to protect the confidentiality, authenticity or integrity of information according to business and information security requirements, and taking into consideration legal, statutory, regulatory and contractual requirements related to cryptography. A.10.1.1 Policy on the use of cryptographic controls. 【CLOUD】 A policy on the use of cryptographic controls for protection of information must be developed and implemented. A.10.1.2 Key management 【CLOUD】鍵管理 A policy on the use, protection and lifetime of cryptographic keys must be developed and implemented thru their whole lifecycle. ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. Secure Developmen t Life Cycle A.8.25 Secure development life cycle Rules for the secure development of software and systems must be established and applied to ensure information security is designed and implemented within the secure development life cycle of software and systems. A.14.2.1 Secure development policy 【CLOUD】 Rules for the development of software and systems must be established and applied to developments within the organization. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022
- 24. Application Security Requirement s A.8.26 Application security requirements Information security requirements must be identified, specified and approved when developing or acquiring applications to ensure all information security requirements are identified and addressed when developing or acquiring applications. A.14.1.2 Securing application services on public networks Information involved in applications services passing over public networks must be protected from fraudulent activity, contract dispute and unauthorized disclosure and modification. A.14.1.3 Protecting application services transactions Information involved in application service transactions must be protected to prevent incomplete transmission, mis-routing, unauthorized message alteration, unauthorized disclosure, unauthorized message duplication or replay. ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. Secure system Architecture and Engineering Principles A.8.27 Secure system architecture and engineering principles Principles for engineering secure systems must be established, documented, maintained and applied to any information system development activities to ensure information systems are securely designed, i l t d d t d ithi th d l t lif A.14.2.5 Secure system engineering principles Principles for engineering secure system must be established, documented, maintained and applied to any information system implementation efforts. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Secure coding A.8.28 Secure coding Secure coding principles must be applied to software development to ensure software is written securely thereby reducing the number of potential information security vulnerabilities in the software none ・Significant Changes in ISO27001:2022. ・None from ISO27001:2013 is relevant to this control in ISO27001:2022. Security Testing in Developmen t and Acceptance A.8.29 Security testing in development and acceptance Security testing processes must be defined and implemented in the development life cycle.to validate if information security requirements are met when applications or code are deployed to the production environment. A.14.2.8 System security testing Testing of security functionality must be carried out during development. A.14.2.9 System acceptance testing 【CLOUD】 システムの受入れ基準 Acceptance testing programs and related criteria must be established for information systems, upgrades, and versions. ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022.
- 25. Outsourced Developmen t A.8.30 Outsourced development The organization must direct, monitor and review the activities related to outsourced system development to ensure information security measures required by the organization are implemented in outsourced system development. A.14.2.7 Outsourced development The organization must supervise and monitor the activity of outsourced system development. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Separation of Developmen t, Test and Production Environment s A.8.31 Separation of development, test and production environments Development, testing and production environments must be separated and secured to protect the production environment and data from compromise by development and test activities. A.12.1.4 Separation of development, testing and operational env. Development, testing, and operational environments must be separate to reduce the risks of unauthorized access or changes to the operational environment. A.14.2.6 Secure development environment Organizations must establish and appropriately protect secure development environments for system development and integration efforts that cover the ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022. Change Managemen t A.8.32 Change management Changes to information processing facilities and information systems must be subject to change management procedures.to preserve information security when executing changes. A.12.1.2 Change management 【CLOUD】変更管理 Changes to the organization, business processes, information processing facilities and systems that affect information security must be controlled. A.14.2.2 System change control procedures Changes to systems within the development lifecycle must be controlled by the use of formal change control procedures. A.14.2.3 Technical review of applications after operating platform changes When operating platforms are changed, business critical applications must be reviewed and tested to ensure there is no adverse impact on organizational operations or security. A.14.2.4 Restrictions on changes to software packages Modifications to software packages must be discouraged, limited to necessary changes and all changes must be strictly controlled. ・Several Controls from ISO27001:2013 were integrated into one in ISO27001:2022.
- 26. Test Information A.8.33 Test information Test information must be appropriately selected, protected and managed to ensure relevance of testing and protection of operational information used for testing. A.14.3.1 Protection of test data Test data must be selected carefully, protected and controlled. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022 Protection of Information Systems during audit Testing A.8.34 Protection of information systems during audit testing Audit tests and other assurance activities involving assessment of operational systemAudit tests and other assurance activities involving assessment of operational systems must be planned and agreed between the tester and appropriate management. to minimize the impact of audit and other assurance activities on operational systems and business processes. A.12.7.1 Information systems audit controls Audit requirements and activities involving verification of operational systems must be carefully planned and agreed to minimize disruptions to business processes. ・There was neither controls' integrations nor significant changes occured in ISO27001:2022