Ransomware Explained
•
0 gefällt mir•103 views
Ransomware attacks—a type of malware (a.k.a. malicious software)— are proliferating around the globe at a blistering pace. In this infographic, learn what to do if you fall prey to an attack, and how data can be protected with cloud backups and disaster recovery.
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
What Businesses Entrepreneurs Are Imperative To Know About Ransomware

What Businesses Entrepreneurs Are Imperative To Know About RansomwareMavrickHost - Reliable Hosting Partner
Weitere ähnliche Inhalte
Ähnlich wie Ransomware Explained
What Businesses Entrepreneurs Are Imperative To Know About Ransomware

What Businesses Entrepreneurs Are Imperative To Know About RansomwareMavrickHost - Reliable Hosting Partner
Ähnlich wie Ransomware Explained (20)
Are ransomware attacks the problem for web hosting firms?

Are ransomware attacks the problem for web hosting firms?
The Most Common Enterprise Malware and how to identify them

The Most Common Enterprise Malware and how to identify them
Corporations - the new victims of targeted ransomware

Corporations - the new victims of targeted ransomware
What Businesses Entrepreneurs Are Imperative To Know About Ransomware

What Businesses Entrepreneurs Are Imperative To Know About Ransomware
Advanced Threats in the Enterprise: Finding an Evil in the Haystack

Advanced Threats in the Enterprise: Finding an Evil in the Haystack
Panda Adaptive Defense 360 - Cyber Extortion Guide

Panda Adaptive Defense 360 - Cyber Extortion Guide
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
Enhancing User Experience - Exploring the Latest Features of Tallyman Axis Lo...

Enhancing User Experience - Exploring the Latest Features of Tallyman Axis Lo...
Passkey Providers and Enabling Portability: FIDO Paris Seminar.pptx

Passkey Providers and Enabling Portability: FIDO Paris Seminar.pptx
Potential of AI (Generative AI) in Business: Learnings and Insights

Potential of AI (Generative AI) in Business: Learnings and Insights
Emixa Mendix Meetup 11 April 2024 about Mendix Native development

Emixa Mendix Meetup 11 April 2024 about Mendix Native development
Use of FIDO in the Payments and Identity Landscape: FIDO Paris Seminar.pptx

Use of FIDO in the Payments and Identity Landscape: FIDO Paris Seminar.pptx
So einfach geht modernes Roaming fuer Notes und Nomad.pdf

So einfach geht modernes Roaming fuer Notes und Nomad.pdf
DevEX - reference for building teams, processes, and platforms

DevEX - reference for building teams, processes, and platforms
(How to Program) Paul Deitel, Harvey Deitel-Java How to Program, Early Object...

(How to Program) Paul Deitel, Harvey Deitel-Java How to Program, Early Object...
The Ultimate Guide to Choosing WordPress Pros and Cons

The Ultimate Guide to Choosing WordPress Pros and Cons
How AI, OpenAI, and ChatGPT impact business and software.

How AI, OpenAI, and ChatGPT impact business and software.
Generative Artificial Intelligence: How generative AI works.pdf

Generative Artificial Intelligence: How generative AI works.pdf
Assure Ecommerce and Retail Operations Uptime with ThousandEyes

Assure Ecommerce and Retail Operations Uptime with ThousandEyes
The Future Roadmap for the Composable Data Stack - Wes McKinney - Data Counci...

The Future Roadmap for the Composable Data Stack - Wes McKinney - Data Counci...
Why device, WIFI, and ISP insights are crucial to supporting remote Microsoft...

Why device, WIFI, and ISP insights are crucial to supporting remote Microsoft...
Generative AI for Technical Writer or Information Developers

Generative AI for Technical Writer or Information Developers
[Webinar] SpiraTest - Setting New Standards in Quality Assurance![[Webinar] SpiraTest - Setting New Standards in Quality Assurance](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[Webinar] SpiraTest - Setting New Standards in Quality Assurance](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[Webinar] SpiraTest - Setting New Standards in Quality Assurance
Scale your database traffic with Read & Write split using MySQL Router

Scale your database traffic with Read & Write split using MySQL Router
Ransomware Explained
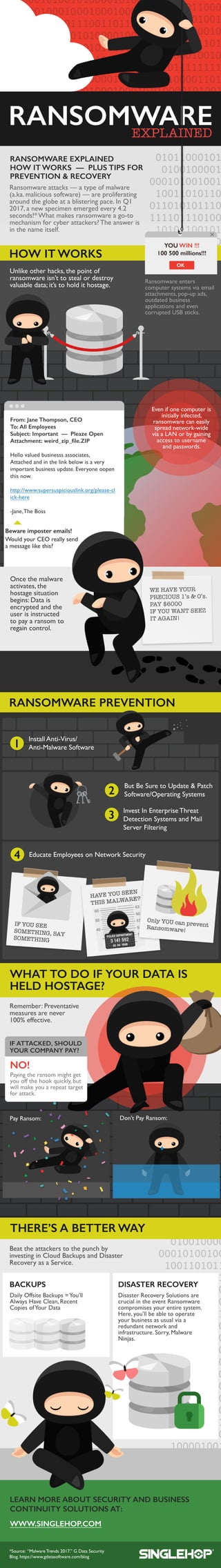
- 1. Unlikeotherhacks,thepointof ransomwareisn’ttostealordestroy valuabledata;it’stoholdithostage. HOW ITWORKS RANSOMWAREPREVENTION RANSOMWAREEXPLAINED HOW ITWORKS— PLUSTIPSFOR PREVENTION&RECOVERY Ransomwareenters computersystemsviaemail attachments,pop-upads, outdatedbusiness applicationsandeven corruptedUSBsticks. Ransomwareattacks— atypeofmalware (a.ka.malicioussoftware)— areproliferating aroundtheglobeatablisteringpace.InQ1 2017,anewspecimenemergedevery4.2 seconds!*Whatmakesransomwareago-to mechanismforcyberattackers?Theansweris inthenameitself. Beattheattackerstothepunchby investinginCloudBackupsandDisaster RecoveryasaService. PayRansom: DailyOffsiteBackups=You’ll AlwaysHaveClean,Recent CopiesofYourData Don’tPayRansom: poster poster poster RANSOMWARE WEHAVEYOUR PRECIOUS1’s&0’s. PAY$6000 IFYOUWANTSEEZ ITAGAIN! 1 2 3 4 IFYOUSEE SOMETHING,SAY SOMETHING HAVEYOUSEEN THISMALWARE? Remember:Preventative measuresarenever 100%effective. WHATTODOIFYOURDATAIS HELDHOSTAGE? DisasterRecoverySolutionsare crucialintheeventRansomware compromisesyourentiresystem. Here,you’llbeabletooperate yourbusinessasusualviaa redundantnetworkand infrastructure.Sorry,Malware NinjasNinjas. THERE’SABETTERWAY BACKUPS DISASTERRECOVERY *Source:“MalwareTrends2017.”GDataSecurity Blog.https://www.gdatasoftware.com/blog Evenifonecomputeris initiallyinfected, ransomwarecaneasily spreadnetwork-wide viaaLANorbygaining accesstousername andpasswords. Bewareimposteremails! WouldyourCEOreallysend amessagelikethis? Oncethemalware activates,the hostagesituation begins:Datais encryptedandthe userisinstructed topayaransomto regaincontregaincontrol. ButBeSuretoUpdate&Patch Software/OperatingSystems EducateEmployeesonNetworkSecurity InstallAnti-Virus/ Anti-MalwareSoftware InvestInEnterpriseThreat DetectionSystemsandMail ServerFiltering Payingtheransommightget youoffthehookquickly,but willmakeyouarepeattarget forattack. IFATTACKED,SHOULD YOURCOMPANYPAY? NO! RANSOMWAREEXPLAINED OnlyYOUcanpreventRansomware!
