Poster - FATIN FAZAIN_KRK_FYP2
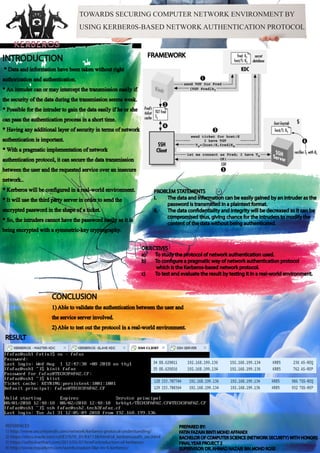
- 1. TOWARDS SECURING COMPUTER NETWORK ENVIRONMENT BY USING KERBER0S-BASED NETWORKAUTHENTICATION PROTOCOL PROBLEM STATEMENTS i. The data and information can be easily gained by an intruder as the password is transmitted in a plaintext format. ii. The data confidentiality and integrity will be decreased as it can be compromised thus, giving chance for the intruders to modify the content of the data without being authenticated. REFERENCES 1) http://www.securityandit.com/network/kerberos-protocol-understanding/ 2) https://docs.oracle.com/cd/E37670_01/E41138/html/ol_kerberosauth_sec.html 3) https://sathisharthars.com/2013/05/07/brief-introduction-of-kerberos/ 4) http://www.roguelynn.com/words/explain-like-im-5-kerberos/ OBJECTIVES a) To study the protocol of network authentication used. b) To configure a pragmatic way of network authentication protocol which is the Kerberos-based network protocol. c) To test and evaluate the result by testing it in a real-world environment. CONCLUSION 1)Able to validate the authentication between the user and the service server involved. 2)Able to test out the protocol in a real-world environment. INTRODUCTION * Data and information have been taken without right authorization and authentication. *An intruder can or may intercept the transmission easily if the security of the data during the transmission seems weak. * Possible for the intruder to gain the data easily if he or she can pass the authentication process in a short time. * Having any additional layer of security in terms of network authentication is important. * With a pragmatic implementation of network authentication protocol, it can secure the data transmission between the user and the requested service over an insecure network.. * Kerberos will be configured in a real-world environment. * It will use the third party server in order to send the encrypted password in the shape of a ticket. * So, the intruders cannot have the password easily as it is being encrypted with a symmetric-key cryptography. FRAMEWORK RESULT PREPARED BY: FATIN FAZAIN BINTI MOHD AFFANDI BACHELOR OF COMPUTER SCIENCE (NETWORK SECURITY) WITH HONORS FINAL YEAR PROJECT 2 SUPERVISOR: DR. AHMAD NAZARI BIN MOHD ROSE