How to implement cloud computing security
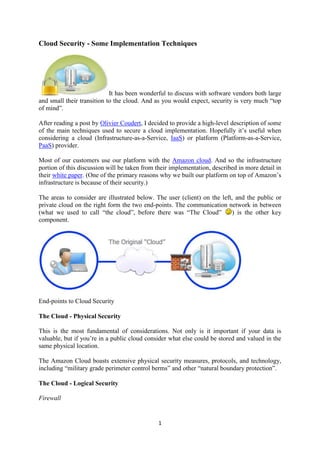
- 1. 1 Cloud Security - Some Implementation Techniques It has been wonderful to discuss with software vendors both large and small their transition to the cloud. And as you would expect, security is very much “top of mind”. After reading a post by Olivier Coudert, I decided to provide a high-level description of some of the main techniques used to secure a cloud implementation. Hopefully it’s useful when considering a cloud (Infrastructure-as-a-Service, IaaS) or platform (Platform-as-a-Service, PaaS) provider. Most of our customers use our platform with the Amazon cloud. And so the infrastructure portion of this discussion will be taken from their implementation, described in more detail in their white paper. (One of the primary reasons why we built our platform on top of Amazon’s infrastructure is because of their security.) The areas to consider are illustrated below. The user (client) on the left, and the public or private cloud on the right form the two end-points. The communication network in between (what we used to call “the cloud”, before there was “The Cloud” ) is the other key component. End-points to Cloud Security The Cloud - Physical Security This is the most fundamental of considerations. Not only is it important if your data is valuable, but if you’re in a public cloud consider what else could be stored and valued in the same physical location. The Amazon Cloud boasts extensive physical security measures, protocols, and technology, including “military grade perimeter control berms” and other “natural boundary protection”. The Cloud - Logical Security Firewall
- 2. 2 Many breaches of security come from bots pinging IP addresses on multiple ports, mechanically looking for a way to get in somewhere (Port Scanning). This type of attack is prevented at the Firewall: (i) Close all ports except those that are to be used. And only open those when they are actually used. (ii) Restrict access by the protocol used (http, ssh, etc.) (iii) Restrict access to only known client IP addresses. In addition to this, AWS detects port scanning, stops it and blocks it. Counter measures are also in place to protect against Distributed Denial of Service (DDoS) and Man In the Middle (MITM) attacks. Operating System (Host and Guest) Operating System Security The Host Operating System that resides on the actual hardware needs to have strong key access to a limited number of Administrators. No one else should have access at this level. And those that do have access should only have it on a limited basis and only when they are doing actual work. Guest OS’s (the virtual instances that are actually used by the hosted software) are isolated from the Host by the hypervisor (which also provides isolation between running instances). Unprivileged Access to these instances should only be allowed via token or key-based authentication. Key control is paramount for success at this level. Data - Backup & Encryption All stored data should be redundantly backed up, ideally (as with AWS) in multiple physical locations. In addition, data can be encrypted on the remote instance. In fact, encryption can be taken down to a very low level, but performance trade-offs come into play very quickly.
- 3. 3 The Network Other than protection from threats residing elsewhere on the network, data interception should be protected against. Therefore, data traveling across the network should be encrypted. In our case, we implemented communication and data transfer protocols that use AES-128 symmetric key encryption for all data sent between the client and the cloud server. The User After all of the above (and much more) has been put in place, we still need to provide access to users (customers) outside of the firewall. And so we need to know who the users are, and to be able to confirm that they are indeed who they say they are. In order to scale the business, the authentication and validation process must be automated and built into the on-boarding and access process. Fortunately, as we’re dealing in a business-to-business environment, the easiest and most reliable way to automatically confirm identity is via an email validation process during user on-boarding. Once validated and prior to accessing the cloud, the user’s identity should be authenticated again using the email address (or a username linked to the email address) and a password. On the Xuropa Platform, we go one step further and add an additional security protocol to ensure that only the previously authenticated user can gain access to the cloud from a detected IP address. Life’s a Trade-off These are just a few of the techniques employed - when it comes down to it, anything is possible. However, people need to have access, and in order for businesses to run, access needs to be straight forward for the user, monitored, controlled, and automated. In architecting our platform, security is paramount, which means we have to put a great deal of effort into automation and the user experience (UX) design. How are you securing your cloud processes? And what are your concerns related to security find out how the Cloud is going to Operate compared to the DMZ wen it comes to logical Information Security. By the looks of things the Clouds is going to operate outside the DMZ. if that is True, that will make the Cloud computing to be highly vulnerable. o Please explain to me how logical security will operate in the clouds. James Colgan May 25, 2011 12:23 pm o Thanks for your comment Putso. Unfortunately “DMZ” really doesn’t mean that much without context.
- 4. 4 How To Implement Cloud Computing Security o Logical security involves such strategies as the encryption of data traversing to/from the cloud, and between instances within the cloud. It also refers to the issuance of credentials to authorized users and then logically locking communication between that user’s client and the cloud resource. o o It also refers to locking down the ports on firewalls at the points of entry to the cloud. We can also go further up the stack and look at access control interfaces, etc. There’s so much in this domain…I’ll put together more posts on the subject in the near future. Maintaining security after a cloud computing implementation You've successfully migrated your organization's selected applications and data into the cloud, and everyone has said what a great job you've done. But you and I both know the task of maintaining the security of these apps and data has only just begun. In this tip, I'll review which technologies and processes must be initiated, monitored and secured after a cloud computing implementation or initiative is up and running. IAM Cloud computing turns us all into remote workers, which makes identity and access management (IAM) one of the key challenges after a cloud computing move. It is important to have robust lifecycle management regarding users and user access so that user accounts, credentials and access rights are always relevant and up to date, including disabling an account when an employee leaves. Also look to initiate an IAM strategy that can make full use of federated identity management, which enables users to securely access data or systems across autonomous security domains. More specifically, consider introducing single sign-on (SSO) for enterprise applications and leveraging this architecture to simplify cloud provider implementations. A move to the cloud will appear far more seamless to your users if they are already used to SSO, and it'll make managing trust across different types of cloud services less onerous. You will also have logged baseline data to help you monitor and gauge changes due to cloud activity. How To Implement Cloud Computing Security How To Implement Cloud Computing Security You may not realize it but your company may have adopted cloud computing. Your company may have subscribed to other miscellaneous services like the ones being offered by Salesforce.com or you may be using a hosted email. Your organization may even be implementing an internal private cloud. With all the uncertainties and fears of using the cloud, one must accept the fact that cloud computing will be here for a long time.
- 5. 5 It is but expected that everyone will have security as their number one fear when a new technology is introduced to the market especially when media tends to play up the security inconsistencies of cloud computing. But when you really look deeper into the problem, you’ll realize that these security breaches happen because the organization allows them to happen. Cyber criminals often look at cloud computing loopholes and attach those which have loose controls in place. When an organization decides to move to the clouds, it must first determine its foundational controls which form the backbone of the company’s security principles. Plans must be laid out in order to secure the company’s assets so that when the company subscribes to cloud computing, all the needed security controls must already be in place. Also, the company will have to be workload-focused instead of cloud-focused. When moving to the clouds, the organization must take into consideration each workload so that it will be able to enforce a security program which is focused on the workload with a possibility to implement non-traditional security measures. More often than not, a company decides to move to the clouds because higher management has decided it. Because not all parties are included in the decision process, some security measures may not have been considered. When this happens, the organization may face usability and integration challenges. Concerned departments must be included in the decision making so that people working with the affected departments will know what to expect when cloud computing is finally implemented. A plan must be enforced to mitigate the risks. It must have a documented plan so that employees will be able to quickly resolve cloud computing issues when they arise. Training, education, as well as documentation and management of risks must be included in the risk mitigation plan. A major advantage of cloud computing is that it is capable of virtualization and because of this advantage an organization must have a management process for its storage image implemented. This will guarantee that the required images are made available when needed. The images must also be appropriately managed and identified so that image sprawl will be avoided. Before a company migrates to the clouds, it must first check the cloud computing provider’s infrastructure and applications for any security hazards so that controls can be set in place in order to ensure that the transfer to the clouds are secure. The company must also take note of ethical hacking so that they can use it to check their own cloud applications for the usual security vulnerabilities. There are also security services available in the market which can help the company obtain the best security without the traditional overhead expense. These services include security event log management, identity and access management, and intrusion prevention which transfer the strain of implementing them from the organization to the security services provider. A resiliency program must also be considered when adopting cloud computing because cloud technologies are not perfect. Critical workloads must be restored quickly in case
- 6. 6 of attack or catastrophe. Restoration must be done quickly and responsibly so that there is less impact on the business process. Monitoring is also important when the organization moves to the clouds. If the company fails to oversee the implementations in cloud computing, there is a great possibility that there will be security, satisfaction, and performance issues. A monitoring program must be actively implemented so that security threats are properly identified. By diligently ensuring security measures are in place, the company can be a step in allaying fears of security breaches. Security plans must be reviewed regularly because new threats may be just lurking around the corner and as such the company must be prepared to deal with them. Florence de Borja “Choosing a Cloud Provider with Confidence” Cloud computing is rapidly transforming the IT landscape and the conversation around adopting cloud technology has progressed from “if” to “when”… Free Download Report (Disclaimer: CloudTweaks publishes news and opinion articles from different contributors. All views and opinions in these articles belong entirely to our contributors. They do not reflect or represent in any way the personal or professional opinions of CloudTweaks.com or those of its staff.) Tagged as: adopting cloud computing, business process, Cloud Application, Cloud applications, Cloud Computing, cloud computing loopholes, Cloud Computing Security, cloud technologies, clouds, computing security, Crime preventionCrime prevention, cyber criminals, depa, implement cloud computing, miscellaneous services, new technology, Private Cloud, Salesforce .com, security breach, security breaches, security event log management, security measures, security principles, security program, security services, security threats, security vulnerabilities, services provider, traditional security, virtualization Cloud Security Guidance IBM Recommendations for the Implementation of Cloud Security Abstract Cloud computing is a flexible, cost-effective, and proven delivery platform for providing business or consumer IT services over the Internet. Cloud resources can be rapidly deployed and easily scaled, with all processes, applications, and services provisioned "on demand", regardless of user location or device. As a result, cloud computing gives organizations the opportunity to increase their service delivery efficiencies, streamline IT management, and better align IT services with dynamic business requirements. In many ways, cloud computing offers the "best of both worlds", providing solid support for core business functions along with the capacity to develop new and innovative services.
- 7. 7 Cloud Security In addition to the usual challenges of developing secure IT systems, cloud computing presents an added level of risk, because essential services are often outsourced to a third party. The "externalized" aspect of outsourcing makes it harder to maintain data integrity and privacy, support data and service availability, and demonstrate compliance. The security measures discussed in this IBM Redpapers™ publication represent best practice implementations for cloud security.
