Mc Ch6
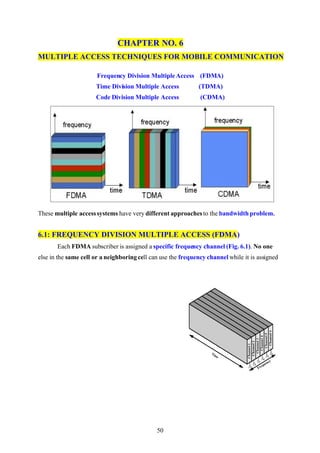
- 1. CHAPTER NO. 6 MULTIPLE ACCESS TECHNIQUES FOR MOBILE COMMUNICATION Frequency Division Multiple Access (FDMA) Time Division Multiple Access (TDMA) Code Division Multiple Access (CDMA) These multiple access systems have very different approaches to the bandwidth problem. 6.1: FREQUENCY DIVISION MULTIPLE ACCESS (FDMA) Each FDMA subscriber is assigned a specific frequency channel (Fig. 6.1). No one else in the same cell or a neighboring cell can use the frequency channel while it is assigned 50
- 2. to a user. This reduces interference, but severely limits the number of users. FIG. NO. 6.1 FREQUENCY DIVISION MULTIPLE ACCESS (FDMA) Frequency-division multiplexing (FDM) advantage of the fact that the useful bandwidth of the medium exceeds the required bandwidth of a given signal 6.2: TIME DIVISION MULTIPLE ACCESS (TDMA) TDMA users share a common frequency channel (Fig. 6.2), but use the channel for only a very short time. They are each given a time slot and only allowed to transmit during that time slot. When all available time slots in a given frequency are used, the next user must be assigned a time slot on another frequency. These time slices are so small that the human ear does not perceive the time slicing 51
- 3. FIG. NO. 6.2: TIME DIVISION MULTIPLE ACCESS (TDMA) Time-division multiplexing (TDM) takes advantage of the fact that the achievable bit rate of the medium exceeds the required data rate of a digital signal 6.3: CODE DIVISION MULTIPLE ACCESS (CDMA) Code-Division Multiple Access (CDMA) is one of the most important concepts to any cellular telephone system is that of “multiple access”. A large number of users share a common pool of radio channels and any user can gain access to any channel. In other words CDMA is a form of multiplexing, which allows numerous signals to occupy a single transmission channel, optimizing the use of available bandwidth. Though CDMA’s application in cellular telephone is relatively new, but it is not a new technology. CDMA has been used in many military applications, such as anti-jamming (because of the spread signal In March 1992, the TIA (Telecommunications Industry Association) established the TR- 45.5 subcommittee with the charter of developing a spread spectrum digital cellular standard. In July of 1993, the TIA gave its approval for the CDMA Technology standard .A CDMA call starts with a standard rate of 9.6 Kbps. This is then spread to a transmitted rate of about 1.23 Mbps. The CDMA channel is nominal 1.23 MHz Wide CDMA is compatible with other cellular technologies 52
- 4. CDMA users share a common frequency channel (Fig 6.3). All users are on the same frequency at the same time. However, each pair of users is assigned a special code that reduces interference while increasing privacy. FIG. NO. 6.3: CODE DIVISION MULTIPLE ACCESS (CDMA) 6.4: GENERATING A CDMA SIGNAL There are five steps in generating a CDMA signal (Fig. 6.4). I. Analog to digital conversion II. Vocoding III. Encoding and interleaving IV. Channelizing the signals V. Conversion of the digital signal to a Radio Frequency (RF) signal The use of codes is a key part of this process. 53
- 5. FIG. NO. 6.4: GENERATING A CDMA SIGNAL (I) ANALOG TO DIGITAL CONVERSION The first step of CDMA signal generation is analog to digital conversion, sometimes called A/D conversion. CDMA uses a technique called Pulse Code Modulation (PCM) to accomplish A/D convers ion. (II) VOCODING (or Voice Compression) The second step of CDMA signal generation is voice compression. CDMA uses a device called a vocoder to accomplish voice compression (Fig. 6.5). The term quot;vocoderquot; is a contraction of the words quot;voicequot; and quot;code.quot; Vocoders are located at the BSC and in the phone. A CDMA vocoder varies compression of the voice signal into one of four data rates based on the rate of the user's speech activity. The four rates are: Full, 1/2, 1/4 and 1/8. The vocoder uses its full rate when a person is talking very fast. It uses the 1/8 rate when the person is silent or nearly so. 54
- 6. FIG. NO. 6.5: GENERATING AN A/D COMPRESSED SIGNAL (III) ENCODING AND INTERLEAVING Encoders and interleavers are built into the BTS and the phones. The purpose of the encoding and interleaving is to build redundancy into the signal so that information lost in transmission can be recovered. The type of encoding done at this stage is called quot;convolutional encoding.quot; A simplified encoding scheme is shown here. A digital message consists of four bits (A, B, C, D) of vocoded data. Each bit is repeated three times. These encoded bits are called symbols. The decoder at the receiver uses a majority logic rule. Thus, if an error occurs, the redundancy can help recover the lost information. EXAMPLE: BURST ERROR: A burst error is a type of error in received digital telephone signals. Burst errors occur in clumps of adjacent symbols. These errors are caused by fading and interference. Encoding and interleaving reduce the effects of burst errors. Interleaving is a simple but powerful method of reducing the effects of burst errors and recovering lost bits. In the example shown in the Fig. 6.6, the symbols from each group are interleaved (or scrambled) in a pattern that the receiver knows. De-interleaving at the receiver unscrambles the bits, spreading any burst errors that occur during transmission. 55
- 7. FIG. NO. 6.6: ENCODING AND INTERLEAVING (IV) CHANNELIZING The encoded voice data is further encoded to separate it from other encoded voice data. The encoded symbols are then spread over the entire bandwidth of the CDMA channel. This process is called channelization. The receiver knows the code and uses it to recover the voice data. KINDS OF CODES: CDMA uses two important types of codes to channelize users. (a) Walsh codes channelize users on the forward link (BTS to mobile). Walsh codes provide a means to uniquely identify each user on the forward link. Walsh codes have a unique mathematical property, that is, they are quot;orthogonal.quot; In other words, Walsh codes are unique enough that a receiver applying the same Walsh code can only recover the voice data. All other signals are discarded as background noise. (a) Pseudorandom Noise (PN) codes channelize users on the reverse link (mobile to BTS). Pseudorandom Noise (PN) codes uniquely identify users on the reverse link. A PN code is one that appears to be random, but isn't. The PN codes used in CDMA yield about 4.4 trillion combinations of code. This is a key reason why CDMA is so secure. 56
- 8. (IV) CONVERSION OF DIGITAL TO RADIO FREQUENCY (RF) SIGNAL The BTS combines channelized data from all calls into one signal. It then converts the digital signal to a Radio Frequency (RF) signal for transmission. 6.5: CODE CHANNELS USED IN CDMA A code channel is a stream of data designated for a specific use or person. This channel may be voice data or overhead control data. Channels are separated by codes. The forward and reverse links use different types of channels. (I) FORWARD LINK CHANNELS: uses four types of channels to transmit voice and control data to the mobile. The types of forward link channels are: i. Pilot ii. Sync iii. Paging iv. Traffic FIG. NO. 6.7: FORWARD LINK CHANNELS (i) PILOT CHANNEL The BTS constantly transmits the pilot channel. The mobile uses the pilot signal to acquire the system. It then uses the pilot signal to monitor and adjust the power needed in order to transmit back to the BTS. 57
- 9. FIG. NO. 6.8: PILOT CHANNEL (ii) SYNC CHANNEL The BTS constantly transmits over the sync channel so the mobile can synchronize with the BTS. It provides the mobile with the system time and the identification number of the cell site. The mobile ignores the sync channel after it is synchronized. FIG. NO. 6.9: SYNC CHANNEL (III) PAGING CHANNEL CDMA uses up to seven paging channels. The paging channel transmits overhead information such as commands and pages to the mobile. The paging channel also 58
- 10. sends commands and traffic channel assignment during call set-up. The mobile ignores the paging channel after a traffic channel is established. FIG. NO. 6.10: PAGING CHANNEL (IV) FORWARD LINK TRAFFIC CHANNEL CDMA uses between fifty-five and sixty-one forward traffic channels to send both voice and overhead control data during a call. Once the call is completed, the mobile tunes back in to the paging channel for commands and pages. FIG. NO. 6.11: TRAFFIC CHANNEL (II) REVERSE LINK CHANNELS: uses two types of channels to transmit voice and control data to BTS. The types of reverse link channels are: i. Access ii. Traffic 59
- 11. FIG. NO. 6.12: REVERSE LINK CHANNELS (i) ACCESS CHANNEL The mobile uses the access channel when not assigned to a traffic channel. The mobile uses the access channel to: Register with the network Originate calls Respond to pages and commands from the base station Transmit overhead messages to the base station FIG. NO. 6.13: ACCESS CHANNEL (II) REVERSE LINK TRAFFIC CHANNEL The reverse traffic channel is only used when there is a call. The reverse traffic channel transmits voice data to the BTS. It also transmits the overhead control information during the call. 60
- 12. FIG. NO. 6.14: REVERSE LINK TRAFFIC CHANNNEL 6.6: CALL PROCESSING STAGES IN CDMA There are four stages or modes in CDMA call processing (Fig. 6.15): Initialization mode Idle mode Access mode Traffic mode. (I) INITIALIZATION MODE: During initialization, the mobile acquires the system via the Pilot code channel synchronizes with the system via the Sync code channel (II) IDLE MODE: The mobile is not involved in a call during idle mode, but it must stay in communication with the base station. The mobile and the base station communicate over the access and paging code channels. The mobile obtains overhead information via the paging code channel. 61
- 13. FIG. NO. 6.15: CALL PROCESSING STAGES IN CDMA (III) ACCESS MODE: The mobile accesses the network via the Access code channel during call origination. The Access channel and Paging channel carry the required call set-up communication between the mobile phone and the BTS until a traffic channel is established. (IV) TRAFFIC MODE: During a land to mobile (LTM) call: The mobile receives a page on the paging channel. The mobile responds on the access channel. The traffic channel is established and maintained throughout the call. During a mobile to land call (MTL): The call is placed using the Access channel. The base station responds on the paging channel. The traffic channel is established and maintained throughout the call. Call processing (messages): During the call overhead messaging continues on the traffic channel in a limited fashion. This messaging uses quot;Dim and Burstquot; or quot;Blank and Burstquot; signaling, which replaces part of the voice traffic with system messages. The user does not detect this signaling, however, due to the strong data recovery schemes inherent to CDMA. 62
- 14. FIG. NO. 6.16: MOBILE CALL PROCESSING 6.7: FEATURES OF CDMA CDMA has several unique features that make it a cost-effective, high quality wireless solution. The following features are unique to CDMA technology: (a) Universal frequency reuse (b) Fast and accurate power control (c) Different types of handoff (a) FREQUENCY REUSE: The frequency spectrum is a limited resource. Therefore, wireless telephony, like radio, must reuse frequency assignments. Each BTS in a CDMA network can use all available frequencies. Adjacent cells can transmit at the same frequency because users are separated by code channels, not frequency channels. This feature of CDMA, called quot;frequency reuse of one,quot; eliminates the need for frequency planning 63
- 15. FIG. NO. 6.17: POWER CONTROL (b) POWER CONTROL: Power control is a CDMA feature that enables mobiles to adjust the power at which they transmit. This ensures that the base station receives all signals at the appropriate power. The CDMA network independently controls the power at which each mobile transmits. Both forward and reverse links use power control techniques. Reverse link power control: Reverse link power control consists of two processes: Open loop power control: Open loop is the mobile's estimate of the power at which it should transmit. The open loop estimate is based on the strength of the pilot signal the mobile receives. As the pilot signal gets weaker or stronger, the mobile adjusts its transmission strength upwards or downwards. Open loop is used any time the mobile transmits. Closed loop power control: In closed loop, the BTS sends a command to the mobile to increase or decrease the strength at which it is transmitting. The BTS determines this command based on the quality of the signal it receives from the mobile. Closed loop is only used during a call. Closed loop commands are sent on the forward traffic channel. (C) HANDOFF IN CDMA: Handoff is the process of transferring a call from one cell to another. This is necessary to continue the call as the phone travels. CDMA is unique in how it handles handoff. 64
- 16. TYPES OF CDMA HANDOFF: CDMA has three primary types of handoff: i. SOFT ii. HARD iii. IDLE (i) SOFT HANDOFF A soft handoff establishes a connection with the new BTS prior to breaking the connection with the old one. This is possible because CDMA cells use the same frequency and because the mobile uses a rake receiver. FIG. NO. 6.18: SOFT HANDOFF Variations of the soft handoff: There are two variations of soft handoffs involving handoffs between sectors within a BTS: Softer Soft-softer The softer handoff: occurs between two sectors of the same BTS. The BTS decodes and combines the voice signal from each sector and forwards the combined voice frame to the BSC. The soft-softer handoff is combination handoff involving multiple cells and multiple sectors within one of the cells. 65
- 17. FIG. NO. 6.19: SOFTER HANDOFF (ii) HARD HANDOFF A hard handoff requires the mobile to break the connection with the old BTS prior to making the connection with the new one. CDMA phones use a hard handoff when moving from a CDMA system to an analog system because soft handoffs are not possible in analog systems. A Pilot Beacon Unit (PBU) at the analog cell site alerts the phone that it is reaching the edge of CDMA coverage. The phone switches from digital to analog mode as during the hard handoff. Hard handoff may also be used when moving to a different: - RF channel - MTSO - Carrier - Market (iii) IDLE HANDOFF An idle handoff occurs when the phone is in idle mode. The mobile will detect a pilot signal that is stronger than the current pilot. The mobile is always searching for the pilots from any neighboring BTS. When it finds a stronger signal, the mobile simply begins attending to the new pilot. 66
- 18. 6.8: ADVANTAGES OF CDMA CDMA technology has numerous advantages including: i. COVERAGE ii. CAPACITY iii. CLARITY iv. COST v. COMPATIBILITY vi. CUSTOMER SATISFACTION (i) COVERAGE CDMA's features result in coverage that is between 1.7 and 3 times that of TDMA. Power control helps the network dynamically expand the coverage area. Coding and interleaving provide the ability to cover a larger area for the same amount of available power used in other systems. (II) CAPACITY CDMA capacity is ten to twenty times that of analog systems, and it's up to four times that of TDMA. Reasons for this include: CDMA's universal frequency reuse CDMA users are separated by codes, not frequencies Power control minimizes interference, resulting in maximized capacity. CDMA's soft handoff also helps increase capacity. This is because a soft handoff requires less power. FIG. NO. 6.20: ADVANTAGES OF CDMA 67
- 19. (iii) CLARITY Often CDMA systems can achieve quot;wire linequot; clarity because of CDMA's strong digital processing. Specifically: The rake receiver reduces errors The variable rate vocoder reduces the amount of data transmitted per person, reducing interference. The soft handoff also reduces power requirements and interference. Power control reduces errors by keeping power at an optimal level. CDMA's wide band signal reduces fading. Encoding and interleaving reduce errors that result from fading. (iv) COST CDMA's better coverage and capacity result in cost benefits: Increased coverage per BTS means fewer are needed to cover a given area. This reduces infrastructure costs for the providers. Increased capacity increases the service provider's revenue potential. CDMA costs per subscriber has steadily declined since 1995 for both cellular and PCS applications. FIG. NO. 6.21: COST OF CDMA (v) COMPATIBILITY 68
- 20. CDMA phones are usually dual mode. This means they can work in both CDMA’s systems and analog cellular systems. Some CDMA phones are dual band as well as dual mode. They can work in CDMA mode in the PCS band, CDMA mode in the cellular band, or analog mode in an analog cellular network. (vi) CUSTOMER SATISFACTION CDMA results in greater customer satisfaction because CDMA provides better: Voice quality Longer battery life due to reduced power requirements No cross-talk because of CDMA's unique coding Privacy--again, because of coding FIG. NO. 6.22 CDMA CUSTOMER SATISFACTION 6.8: ARCHITECTURE OF THE CDMA NETWORK A CDMA network is composed of several functional entities, whose functions and interfaces are specified. The CDMA network can be divided into three broad parts. The Mobile Station is carried by the subscriber. The Base Station Subsystem controls the radio link with the Mobile Station. The Network Subsystem, the main part of which is the Mobile services Switching Center (MSC), performs the switching of calls between the mobile users, and between mobile and fixed network users. The MSC also handles the mobility management operations. Not shown is the Operations and Maintenance Center, which oversees the proper operation and setup of the network. The Mobile Station and the Base Station Subsystem communicate across the Um interface, also known as the air interface or radio link. The Base Station Subsystem communicates with the Mobile services Switching Center across the A interface. 69
- 21. FIG. NO. 6.23 GENERAL ARCHITECTURE OF A CDMA NETWORK (I) MOBILE STATION The mobile station (MS) consists of the mobile equipment. The mobile equipment is uniquely identified by the International Mobile Equipment Identity (IMEI). FIG. NO. 6.24: MOBILE EQUIPMENTS (II) BASE STATION SUBSYSTEM The Base Station Subsystem is composed of two parts: (a) The Base Transceiver Station (BTS) (b) The Base Station Controller (BSC). These communicate across the standardized Abis interface, allowing operation between components made by different suppliers. 70
- 22. FIG. NO. 6.25: BASE STATION SUBSYSTEM (a) The Base Transceiver Station (BTS) houses the radio transceivers that define a cell and handles the radio-link protocols with the Mobile Station. In a large urban area, there will potentially be a large number of BTSs deployed, thus the requirements for a BTS are ruggedness, reliability, portability, and minimum cost. The base station is under direction of a base station controller so traffic gets sent there first. The base station controller gathers the calls from many base stations and passes them on to a mobile telephone switch. From that switch come and go the calls from the regular telephone network. (b) The Base Station Controller (BSC) manages the radio resources for one or more BTSs. It handles radio-channel setup, frequency hopping, and handovers, as described below. The BSC is the connection between the mobile station and the Mobile service Switching Center (MSC). Another difference between conventional cellular and CDMA is the base station controller. It's an intermediate step between the base station transceiver and the mobile switch. This a better approach for high-density cellular networks. As If every base station talked directly to the MSC, traffic would become too congested. To ensure quality communications via traffic management, the wireless infrastructure network uses Base Station Controllers as a way to segment the network and control congestion. The result is that MSCs route their circuits to BSCs which in turn are responsible for connectivity and routing of calls for 50 to 100 wireless base stations.quot; 71
- 23. FIG. NO. 6.26: BASE STATION CONTROLLER BSC functions includes: Performs vocoding of the voice signal Routes calls to the MTSO Handles call control processes Maintains a database of subscribers Maintains records of calls for billing The voice coders or vocoders are built into the handsets a cellular carrier distributes. They're the circuitry that turns speech into digital. The carrier specifies which rate they want traffic compressed, either a great deal or just a little. The cellular system is designed this way, with handset vocoders working in league with the equipment of the base station subsystem. (III) THE MOBILE SWITCHING CENTER The central component of the Network Subsystem is the Mobile services Switching Center (MSC). FIG. NO. 6.27: THE MOBILE SWITCHING CENTER It acts like a normal switching node of the PSTN or ISDN, and additionally provides all the functionality needed to handle a mobile subscriber, such as registration, authentication, location updating, handovers, and call routing to a roaming subscriber. These services are provided in conjunction with several functional entities, which together 72
- 24. form the Network Subsystem. The MSC provides the connection to the fixed networks (such as the PSTN or ISDN). Signaling between functional entities in the Network Subsystem uses Signaling System Number 7 (SS7), used for trunk signaling in ISDN and widely used in current public networks. (IV) HOME LOCATION REGISTER (HLR) & VISITED LOCATION REGISTER (VLR) The Home Location Register (HLR) and Visitor Location Register (VLR), together with the MSC, provide the call routing and roaming capabilities. The HLR contains all the administrative information of each subscriber registered in the network, along with the current location of the mobile. The location of the mobile is typically in the form of the signaling address of the VLR associated with the mobile station. The Visitor Location Register (VLR) contains selected administrative information from the HLR, necessary for call control and provision of the subscribed services, for each mobile currently located in the geographical area controlled by the VLR. Most often these two directories are located in the same place. The HLR and VLR are big databases maintained on computers called servers, often UNIX workstations. To operate its nationwide cellular system, iDEN, Motorola uses over 60 HLRs nationwide. (V) EQUIPMENT IDENTITY REGISTER (EIR) The other two registers are used for authentication and security purposes. The Equipment Identity Register (EIR) is a database that contains a list of all valid mobile equipment on the network, where each mobile station is identified by its International Mobile Equipment Identity (IMEI). An IMEI is marked as invalid if it has been reported stolen or is not type approved. (Vi) THE INTERFACES Cellular radio's most cryptic terms belong to these names: A, Um, Abis, and Ater. A telecom interface means many things. It can be a mechanical or electrical link connecting equipment together. Or a boundary between systems, such as between the base station system and the network subsystem. Interfaces are standardized methods for passing information back and forth. The transmission media isn't important. Whether copper or fiber optic cable or microwave radio, an interface insists that signals go back and forth in the same way, in the same format. With this approach different equipment from any manufacturer will work together. 73
- 25. “A-bis quot; is a French term meaning 'the second A Interface”. In most cases the actual span or physical connection is made on an E1 line. But regardless of the material used, the transmission media, it is the signaling protocol that is most important. Although the interface is unlabeled, the mobile switch communicates with the telephone network using Signaling System Seven, an internationally agreed upon standard. More specifically, it uses ISUP over SS7. quot;ISUP defines the protocol and procedures used to set-up, manage, and release trunk circuits that carry voice and data calls over the public switched telephone network (PSTN). ISUP is used for both ISDN and non-ISDN calls.quot; 6.9: COMPARISON OF MULTIPLE ACCESS SYSTEMS The table summarizes in Fig.6.28 shows some of the technical aspects of the multiple access technologies. The technology used determines the channel's capacity. TDMA triples the capacity of FDMA, but CDMA capacity can be up to seven times that of TDMA. FIG. NO. 6.28: COMPARISON OF MULTIPLE ACCESS SYSTEMS ******** 74
