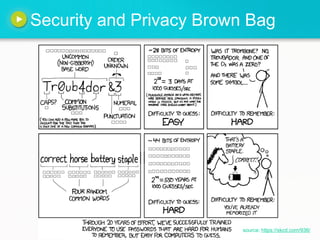
Security and Privacy Brown Bag
- 1. Security and Privacy Brown Bag source: https://xkcd.com/936/
- 2. proudly presents the Security and Privacy brown bag for nonprofits
- 3. Road Map • Setting the context • Your online identity • Examples of social engineering • Passwords and password management • Your email (the skeleton key)
- 4. NPower Northwest • Vision o A thriving community with high performing nonprofits. • Mission o To strengthen the nonprofit sector by catalyzing innovation and driving adoption of technology solutions.
- 5. Introductions Stephen Eggers HandsOn Tech AmeriCorp VISTA Serving at NPower NW stephene@npowernw.org
- 6. Setting the context Privacy • Managing your online presence • What can people learn about you? • What can people do with that knowledge? Security • Best practices • Password management • The skeleton key: your email account
- 7. What do you know about me?
- 8. What do you know about me? From my website & blog: • Which cities I have lived in and now live in • Specific clubs that I am in • The names of some of my friends • Some specific events I participated in From NPower: • Where I work & what I do • Specific projects that I am involved in
- 9. What do you know about me?
- 10. What do you know about me? From all search results: • Some YouTube videos from 2004 - 2012 • My hobbies based on forum posts • Can determine some items I own based on forum posts • More photos Name Alias/handle/username
- 11. Social engineering (hacking) "...social engineering was extremely effective in reaching my goals without resorting to using a technical exploit. I would look for the weakest link in the chain that was the least risk and cost to me [...] if an attacker can walk into the server room without much chance of detection, that's all she wrote" Kevin Mitnick (arrested in 1995)
- 12. Social engineering today HBGary and HBGary Federal are technology security companies that were hacked in February of 2011 • Retrieved username and password database through known vulnerability in CMS • CEO and COO had very short passwords and were recovered • CEO and COO used same credentials for other services (Twitter, email, LinkedIn) • Attackers simply asked the Chief Security Specialist through series of emails for a reminder as to their usernames and passwords • HBGary's website was defaced, thousands of emails made public, people were fired and the CEO resigned
- 13. Social engineering today Want my friends' phone numbers? • Create a "clone" of me on Facebook with public data • Send friend requests to friends of my friends • Assume 500 friend requests were made, and 5% accepted • We now have an account that can friend request direct friends, but this time we have many mutual friends in common At the Silver Bullet security conference in São Paulo, UOLDiveo chief security officer Nelson Novaes Neto demonstrated this in November 2011
- 14. Social engineering today Is your location attached to your tweet, embedded in a photo's metadata, or did you forget to make your Google Maps unlisted?
- 15. What can you do? Everyone: • Review your privacy settings • Know what you put in the public domain • Be aware of social engineering strategies IT best practices: • Use unique, strong passwords • Keep systems up to date and patched
- 16. Passwords Use a long password with a mix of uppercase and lowercase letters and numbers Ideal: Dw0lGgBeAx0h10EiothF8FnU4G7yk37LtPTIuAcuqqGkdKD8cqIN2eIMtXzriX Consider using a password management tool Examples: KeePass, LastPass, Firefox, Chrome
- 17. Passwords - a new model • Consider 1 or 2 long (10+ digits) alphanumeric master passwords • Reset all other passwords and store in password locker • All other passwords should be thought of as "disposable" • Don't bother remembering them • Make them super long • Reset them frequently, whenever you forget them, or don't have access to your locker storage Reset a password? To your email it goes!
- 18. Your email account The skeleton key to your online identity. Protect this! Google account: google.com/accounts Outlook / Exchange: • Account timeout after multiple failed guesses • Phones accessing exchange should require a screen password and allow for a remote wipe
- 19. Final PSA • Do not have to fear online banking and shopping • Use long, unique passwords (and try a password management tool) • Check your privacy settings on commonly used services • Google yourself and any aliases or "handles" • Protect your email account • Understand that you're more likely to be conned than hacked • For IT admins: keep services patched and up to date
- 20. Any questions? Is that it?! photo by http://www.flickr.com/photos/plasticrevolver/164351244/
Hinweis der Redaktion
- What do I mean by security and what do I mean by privacy? Online Identity - what is out there for anyone to discover? Social engineering - what can people do with "public domain" knowledge? What the heck to do with all the passwords Friendly PSA about your email account
- Give live demo of my search results.
- Give live demo of my search results. This is your online alias or username... Need one for just about all websites such as youtube, any forums, etc.
- An important part of security and privacy is knowing what is out there. Knowing what's in the "public domain" meaning anyone who can do some sort of detective work. When you leave today, Google yourself. Google your alias as well. Remember my livejournal? A friend back in middle school wrote a very scathing entry about his father.
- Image from https://twitter.com/#!/kevinmitnick
- SQL injection into CMS Retrieved username/password database DB was not salted and no iterative hashing Passwords were 6 lowercase letters and 2 numbers Recovered passwords from CEO and COO users Linux machine had a 6 month old unpatched privilege escalation vulnerability that allowed superuser access. The other username/password was used for twitter, facebook, google apps, etc. Reset everyone's passwords through google apps Started mailing people through their emails
- Give demo of user information
