C C NA Security Skills Assessment
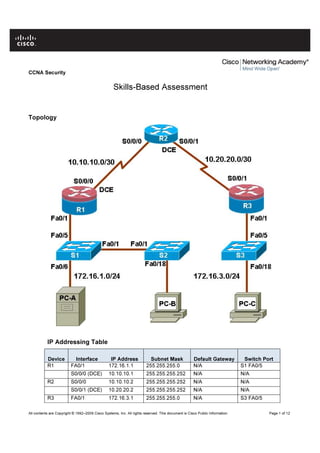
- 1. C C NA Se cu r i t y Skills-B a se d A sse ssm e n t Topology I P A d d r e s s i n g Ta b le D e v i ce I n t e r f ace I P A d d r e ss Su b n e t M ask D e f au l t G at e w ay Sw i t ch Por t R1 F A0/1 17 2.16 .1.1 255.255.255.0 N /A S 1 F A0/5 S 0/0/0 (DCE ) 10.10.10.1 255.255.255.252 N /A N /A R2 S 0/0/0 10.10.10.2 255.255.255.252 N /A N /A S 0/0/1 (DCE ) 10.20.20.2 255.255.255.252 N /A N /A R3 F A0/1 17 2.16 .3.1 255.255.255.0 N /A S 3 F A0/5 All contents are Copyright © 1992–20 0 9 Cisco S ystem s, I nc. All rights reserv ed . T his d ocu m ent is Cisco P u b lic I nf orm ation. P age 1 of 12
- 2. C C NA Se cu r i t y D e v i ce I n t e r f ace I P A d d r e ss Su b n e t M ask D e f au l t G at e w ay Sw i t ch Por t S 0/0/1 10.20.20.1 255.255.255.252 N /A N /A S 1 V LAN 1 17 2.16 .1.11 255.255.255.0 17 2.16 .1.1 N /A S 2 V LAN 1 17 2.16 .1.12 255.255.255.0 17 2.16 .1.1 N /A S 3 V LAN 1 17 2.16 .3.11 255.255.255.0 17 2.16 .3.1 N /A P C-A N IC 17 2.16 .1.3 255.255.255.0 17 2.16 .1.1 S 1 F A0/6 P C-B N IC 17 2.16 .1.2 255.255.255.0 17 2.16 .1.1 S 2 F A0/18 P C-C N IC 17 2.16 .3.3 255.255.255.0 17 2.16 .3.1 S 3 F A0/18 O b je c tiv e s P art 1: Buil d th e netw o rk and co nf ig ure b asic dev ice setting s P art 2: S ecure N etw o rk Ro uters • Co nf ig ure encry pted passw o rds and a l o g in b anner. • Co nf ig ure E X E C tim eo ut o n co nso l e and V T Y l ines. • Co nf ig ure l o g in f ail ure rates and v irtual l o g in enh ancem ents • Co nf ig ure S S H access and disab l e T el net. • Co nf ig ure l o cal AAA auth enticatio n. • Co nf ig ure a z o ne-b ased po l icy f irew al l (Z P F ) and ACLs using Cisco S DM . • Co nf ig ure Intrusio n P rev entio n S y stem (IP S ) using Cisco S DM . P art 3: Co nf ig ure a S ite-to -S ite V P N • Co nf ig ure a S ite-to -S ite V P N using S DM . P art 4: S ecure N etw o rk S w itch es • Co nf ig ure passw o rds, and a l o g in b anner. • Co nf ig ure m anag em ent V LAN access. • S ecure trunk po rts. • S ecure access po rts. • P ro tect ag ainst S T P attack s. • Co nf ig ure po rt security and disab l e unused po rts. Exam O v e rv i e w T h is sk il l s-b ased assessm ent is th e f inal practical ex am f o r th e co urse CCN A S ecurity . T h e ex am is div ided into f o ur parts. T h e parts sh o ul d b e co m pl eted seq uential l y . In P art 1, y o u cab l e th e netw o rk and co nf ig ure th e b asic dev ice setting s. S tatic ro uting is used b etw een th e netw o rk s. In P art 2 y o u secure netw o rk ro uters using Cisco S DM and CLI to co nf ig ure v ario us IO S f eatures incl uding AAA, Z P F , ACLs and IP S . In P art 3 y o u co nf ig ure a S ite-to -S ite V P N b etw een R1 and R3 th ro ug h th e IS P ro uter (R2). In P art 4 y o u co nf ig ure sw itch security f eatures. Not e : T h e ro uter co m m ands and o utput in th is S BA are f ro m a Cisco 1841 w ith Cisco IO S Rel ease 12.4(20)T (Adv anced IP im ag e). T h e sw itch co m m ands and o utput are f ro m a Cisco W S -C29 6 0-24T T -L w ith Cisco IO S Rel ease 12.2(46 )S E (C29 6 0-LAN BAS E K 9 -M im ag e). O th er ro uters, sw itch es, and Cisco IO S v ersio ns m ay b e used. S ee th e Ro uter Interf ace S um m ary tab l e at th e end o f th e S BA to determ ine w h ich interf ace All contents are Copyright © 1992–20 0 9 Cisco S ystem s, I nc. All rights reserv ed . T his d ocu m ent is Cisco P u b lic I nf orm ation. P age 2 of 12
- 3. C C NA Se cu r i t y identif iers to use b ased o n th e eq uipm ent in th e l ab . Depending o n th e ro uter o r sw itch m o del and Cisco IO S v ersio n, th e co m m ands av ail ab l e and o utput pro duced m ig h t v ary f ro m w h at is sh o w n in th is S BA. Not e : M ak e sure th at th e ro uters and sw itch es h av e b een erased and h av e no startup co nf ig uratio ns. Re q u i r e d Re s ou r c e s • 2 ro uters w ith S DM 2.5 instal l ed (Cisco 1841 w ith Cisco IO S Rel ease 12.4(20)T 1 Adv anced IP S erv ice o r co m parab l e) • 1 ro uter (Cisco 1841 w ith Cisco IO S Rel ease 12.4(20)T 1 IP Base o r co m parab l e) • 3 sw itch es (Cisco 29 6 0 w ith Cisco IO S Rel ease 12.2(46 )S E C29 6 0-LAN BAS E K 9 -M im ag e o r co m parab l e) • P C-A: W indo w s X P o r V ista (w ith S S H cl ient, T F T P serv er and IP S f il es) • P C-B: W indo w s X P o r V ista • P C-C: W indo w s X P o r V ista (w ith S S H cl ient, T F T P serv er and IP S f il es) • S erial and E th ernet cab l es as sh o w n in th e to po l o g y • Ro l l o v er cab l es to co nf ig ure th e ro uters and sw itch es v ia th e co nso l e Part 1: B u i l d th e N e tw o rk an d Co n f i g u re B as i c S e tti n g s to Cre ate th e T e s ti n g E n v i ro n m e n t. In P art 1, y o u set up th e netw o rk to po l o g y and co nf ig ure b asic setting s, such as th e h o stnam e, interf ace IP addresses and static ro uting . P erf o rm steps o n ro uters and sw itch es as indicated. S t e p 1: Cab l e t h e n e t w o rk as sh o w n i n t h e t o p o l o g y . If th e S BA to po l o g y is al ready set up, g o to S tep 2. O th erw ise, attach th e dev ices sh o w n in th e to po l o g y diag ram , and cab l e as necessary . S t e p 2: Co n f i g u re b asi c se t t i n g s f o r al l ro u t e rs. a. Co nf ig ure h o st nam es as sh o w n in th e to po l o g y . b . Co nf ig ure th e interf ace IP addresses as sh o w n in th e IP addressing tab l e. c. Co nf ig ure a cl o ck rate f o r th e ro uters w ith a DCE serial cab l e attach ed to th eir serial interf ace. d. Disab l e DN S l o o k up to prev ent th e ro uter f ro m attem pting to transl ate inco rrectl y entered co m m ands as th o ug h th ey w ere h o st nam es. S t e p 3: Co n f i g u re st at i c de f au l t ro u t e s o n e dg e ro u t e rs ( R 1 an d R 3). Co nf ig ure a static def aul t ro ute f ro m R1 to R2 and f ro m R3 to R2. S t e p 4: Co n f i g u re st at i c ro u t e s o n t h e I S P ro u t e r ( R 2). Co nf ig ure a static ro ute f ro m R2 to th e R1 LAN and f ro m R2 to th e R3 LAN . S t e p 5: Co n f i g u re b asi c se t t i n g s f o r e ac h sw i t c h . a. Co nf ig ure h o st nam es as sh o w n in th e to po l o g y . b . Co nf ig ure th e V LAN 1 m anag em ent address o n each sw itch as sh o w n in th e IP Addressing tab l e. All contents are Copyright © 1992–20 0 9 Cisco S ystem s, I nc. All rights reserv ed . T his d ocu m ent is Cisco P u b lic I nf orm ation. P age 3 of 12
- 4. C C NA Se cu r i t y c. Co nf ig ure th e IP def aul t g atew ay f o r each o f th e th ree sw itch es. T h e g atew ay f o r th e S 1 and S 2 sw itch es is th e R1 F a0/1 interf ace IP address. T h e g atew ay f o r th e S 3 sw itch is th e R3 F a0/1 interf ace IP address. d. Disab l e DN S l o o k up to prev ent th e sw itch es f ro m attem pting to transl ate inco rrectl y entered co m m ands as th o ug h th ey w ere h o st nam es. S t e p 6: Co n f i g u re PC h o st I P se t t i n g s. Co nf ig ure a static IP address, sub net m ask , and def aul t g atew ay f o r P C-A, P C-B, and P C-C, as sh o w n in th e IP addressing tab l e. S t e p 7: Ve ri f y c o n n e c t i v i t y b e t w e e n PC-A an d PC-C. S t e p 8: S av e t h e b asi c ru n n i n g c o n f i g u rat i o n f o r e ac h ro u t e r an d sw i t c h . Part 2: S e c u re N e tw o rk R o u te rs In P art 2, y o u co nf ig ure dev ice access, passw o rds, f irew al l s, and intrusio n prev entio n. P erf o rm steps o n ro uters as indicated. Task 1: Configure Passwords and a Login Banner. S t e p 1: Co n f i g u re a m i n i m u m p assw o rd l e n g t h o f 10 c h arac t e rs o n al l ro u t e rs. S t e p 2: Co n f i g u re t h e e n ab l e se c re t p assw o rd o n al l ro u t e rs. Use an enab l e secret passw o rd o f ci scoe n ap a5 5 . S t e p 3: En c ry p t p l ai n t e xt p assw o rds. S t e p 4: Co n f i g u re t h e c o n so l e l i n e s o n al l ro u t e rs. Co nf ig ure a co nso l e passw o rd o f ci scocon p a5 5 and enab l e l o g in. S et th e ex ec-tim eo ut to l o g o ut af ter 5 m inutes o f inactiv ity . P rev ent co nso l e m essag es f ro m interrupting co m m and entry . S t e p 5: Co n f i g u re t h e v t y l i n e s o n R 2. Co nf ig ure a v ty l ines passw o rd o f ci scov t y p a5 5 and enab l e l o g in. S et th e ex ec-tim eo ut to l o g o ut af ter 5 m inutes o f inactiv ity . Not e : T h e v ty l ines f o r R1 and R3 are co nf ig ured f o r S S H in T ask 3. S t e p 6: Co n f i g u re a l o g i n w arn i n g b an n e r o n ro u t e rs R 1 an d R 3. Co nf ig ure a w arning to unauth o riz ed users w ith a m essag e-o f -th e-day (M O T D) b anner th at say s: “Unauth o riz ed access strictl y pro h ib ited and pro secuted to th e f ul l ex tent o f th e l aw !” . Task 2 : Configure Loc al Aut h ent ic at ion Using AAA on R 1 and R 3. S t e p 1: Co n f i g u re t h e l o c al u se r dat ab ase o n R 1. Create a l o cal user acco unt o f A d m i n 01 w ith a secret passw o rd o f A d m i n 01p a5 5 . All contents are Copyright © 1992–20 0 9 Cisco S ystem s, I nc. All rights reserv ed . T his d ocu m ent is Cisco P u b lic I nf orm ation. P age 4 of 12
- 5. C C NA Se cu r i t y S t e p 2: En ab l e A A A se rv i c e s o n R 1. S t e p 3: I m p l e m e n t A A A se rv i c e s u si n g t h e l o c al dat ab ase o n R 1. a. Create th e def aul t l o g in auth enticatio n m eth o d l ist using l o cal auth enticatio n as th e f irst o ptio n and th e enab l e passw o rd as th e b ack up o ptio n. b . E x it to th e initial ro uter screen th at displ ay s: R1 con 0 i s n ow av ai l ab l e , Pr e ss RE T URN t o g e t st ar t e d . c. Lo g in to th e co nso l e as A d m i n 01 w ith a passw o rd o f A d m i n 01p a5 5 to v erif y th at AAA w ith l o cal auth enticatio n is f unctio ning co rrectl y . d. E x it to th e initial ro uter screen th at displ ay s: R1 con 0 i s n ow av ai l ab l e , Pr e ss RE T URN t o g e t st ar t e d . e. Attem pt to l o g in to th e co nso l e as b ad u se r w ith a b ad passw o rd to v erif y th at users no t def ined in th e l o cal ro uter datab ase are denied access. S t e p 4: R e p e at S t e p s 1 t h ro u g h 3 t o c o n f i g u re A A A w i t h l o c al au t h e n t i c at i o n o n R 3. Task 3: Configure t h e S S H S erv er on R out ers R 1 and R 3. S t e p 1: Co n f i g u re t h e do m ai n n am e c c n ase c u ri t y .c o m o n R 1. S t e p 2: Co n f i g u re t h e i n c o m i n g v t y l i n e s o n R 1. S pecif y a priv il eg e l ev el o f 15 so th at a user w ith th e h ig h est priv il eg e l ev el (15) w il l def aul t to priv il eg ed E X E C m o de w h en accessing th e v ty l ines. O th er users w il l def aul t to user E X E C m o de. S pecif y th at th e v ty l ines w il l accept o nl y S S H co nnectio ns. S t e p 3: G e n e rat e t h e R S A e n c ry p t i o n k e y p ai r f o r ro u t e r R 1. Co nf ig ure th e RS A k ey s w ith 1024 as th e num b er o f m o dul us b its. S t e p 4: Ve ri f y S S H c o n n e c t i v i t y t o R 1 f ro m PC-A . Launch th e S S H cl ient (T eraT erm o r P uT T Y ) o n P C-A, enter th e F a0/1 IP address, and l o g in in as A d m i n 01 w ith th e passw o rd A d m i n 01p a5 5 . S t e p 5: R e p e at S t e p s 1 t h ro u g h 4 t o c o n f i g u re S S H o n R 3 an d t e st t h e c o n n e c t i o n f ro m PC-C t o R 3. Task 4: S ec ure against l ogin at t ac ks on R 1 and R 3. S t e p 1: Co n f i g u re t h e f o l l o w i n g p aram e t e rs o n R 1 t o p ro v i de e n h an c e d l o g i n se c u ri t y f o r v i rt u al l o g i n s. • Bl o ck ing perio d w h en l o g in attack detected: 6 0 • M ax im um l o g in f ail ures w ith th e dev ice: 2 • M ax im um tim e perio d f o r cro ssing th e f ail ed l o g in attem pts: 30 • Lo g al l f ail ed l o g in attem pts All contents are Copyright © 1992–20 0 9 Cisco S ystem s, I nc. All rights reserv ed . T his d ocu m ent is Cisco P u b lic I nf orm ation. P age 5 of 12
- 6. C C NA Se cu r i t y S t e p 2: S av e t h e ru n n i n g c o n f i g u rat i o n t o t h e st art u p c o n f i g u rat i o n f o r R 1. S t e p 3: R e p e at st e p s 1 an d 2 t o c o n f i g u re e n h an c e d l o g i n se c u ri t y f o r v i rt u al l o g i n s f o r ro u t e r R 3. Task 5: Configure a Zone-b ased Pol ic y F irewal l ( ZPF ) F irewal l on R 1 and R 3. S t e p 1: En ab l e t h e H T T P se rv e r o n R 1. E nab l e H T T P access o n ro uter R1 and set th e auth enticatio n to use th e l o cal datab ase f o r auth enticatio n. S t e p 2: A c c e ss S D M an d se t c o m m an d de l i v e ry p re f e re n c e s o n R 1. a. Run th e S DM appl icatio n, o r o pen a b ro w ser o n P C-A and start S DM b y entering th e R1 IP address 17 2.16 .1.1 in th e address f iel d. Not e : Y o u m ig h t b e pro m pted b y Internet E x pl o rer to al l o w Activ eX during sev eral o f th ese steps. Cl ick A l l ow . b . Lo g in as A d m i n 01 w ith a passw o rd o f A d m i n 01p a5 5 . E nter th e sam e usernam e and passw o rd f o r sub seq uent l o g in dial o g b o x es, if pro m pted. c. S el ect E d i t > Pr e f e r e n ce s to co nf ig ure S DM to al l o w y o u to prev iew th e co m m ands b ef o re sending th em to th e ro uter. S t e p 3: U se t h e S D M Fi re w al l w i z ard t o c o n f i g u re a ZPF o n R 1. a. Cl ick th e C on f i g u r e b utto n at th e to p o f th e S DM screen, and th en cl ick F i r e w al l an d A C L . b . S el ect B asi c F i r e w al l and cl ick th e L au n ch t h e se l e ct e d t ask b utto n. O n th e Basic F irew al l Co nf ig uratio n w iz ard screen, cl ick Ne x t . c. Ch eck th e I n si d e ( t r u st e d ) ch eck b o x f o r F ast E t h e r n e t 0/1 and th e O u t si d e ( u n t r u st e d ) ch eck b o x f o r Se r i al 0/0/0. Cl ick Ne x t . d. S el ect L ow Se cu r i t y and cl ick Ne x t . In th e S um m ary w indo w , cl ick F i n i sh . e. Cl ick O K in th e Co m m ands Del iv ery S tatus w indo w . S t e p 4: Ve ri f y ZPF f u n c t i o n al i t y . a. F ro m P C-A, p i n g ex ternal ro uter R2 interf ace S 0/0/0 at IP address 10.10.10.2. T h e ping s sh o ul d b e successf ul . b . F ro m ex ternal ro uter R2, p i n g P C-A at IP address 17 2.16 .1.3. T h e ping s sh o ul d N O T b e successf ul . c. F ro m ro uter R2, t e l n e t to R1 at IP address 10.10.10.1. T h e tel net attem pt sh o ul d N O T b e successf ul . d. F ro m P C-A o n th e R1 internal LAN , t e l n e t to R2 at IP address 10.10.10.2 and use passw o rd c is c o v t y p a 5 5 . e. W ith th e T el net sessio n o pen f ro m P C-A to R2, issue th e co m m and s h o w p o l ic y -m a p t y p e in s p e c t z o n e -p a ir s e s s io n o n R1. Co ntinue pressing enter until y o u see an E st ab l i sh e d Se ssi on s sectio n to w ard th e end. W h at is th e so urce address:po rt and destinatio n address:po rt? _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ All contents are Copyright © 1992–20 0 9 Cisco S ystem s, I nc. All rights reserv ed . T his d ocu m ent is Cisco P u b lic I nf orm ation. P age 6 of 12
- 7. C C NA Se cu r i t y S t e p 5: S av e t h e ru n n i n g c o n f i g u rat i o n t o t h e st art u p c o n f i g u rat i o n . S t e p 6: R e p e at S t e p s 1 t h ro u g h 5 t o c o n f i g u re ZPF o n R 3. B e su re t o ac c o u n t f o r di f f e re n c e s i n i n t e rf ac e s an d o t h e r v ari ab l e s. Task 6: Configure I PS on R 1 and R 3 Using S DM . S t e p 1: Pre p are ro u t e r R 1 an d t h e T FT P se rv e r. T o co nf ig ure Cisco IO S IP S 5.x , th e IO S IP S sig nature pack ag e f il e and pub l ic cry pto k ey f il es m ust b e av ail ab l e o n th e P C w ith th e T F T P serv er instal l ed (R1 uses P C-A as th e T F T P serv er and R3 uses P C-C). Ch eck w ith y o ur instructo r if th ese f il es are no t o n th e P C. a. V erif y th at th e I O S-Sx x x -C L I .p k g sig nature pack ag e f il e is in th e def aul t T F T P f o l der. T h e xxx is th e v ersio n num b er and v aries depending o n w h ich f il e w as do w nl o aded f ro m CCO . b . V erif y th at th e r e al m -ci sco.p u b .k e y .t x t f il e is av ail ab l e and no te its l o catio n o n P C-A o r P C-C. T h is is th e pub l ic cry pto k ey used b y Cisco IO S IP S . c. V erif y o r create th e IP S directo ry , i p sd i r , in ro uter f l ash o n R1. F ro m th e R1 CLI, displ ay th e co ntent o f f l ash m em o ry and ch eck to see if th e ipsdir directo ry ex ists. Not e : F o r ro uters R1 and R3, th e IP S sig nature (.x m l ) f il es in th e f l ash : /i p sd i r / directo ry sh o ul d h av e b een del eted and th e directo ry rem o v ed prio r to starting th e S BA. T h e f il es m ust b e del eted f ro m th e directo ry in o rder to rem o v e it. d. If th e i p sd i r directo ry is no t l isted, create it in priv il eg ed E X E C m o de, using th e m k d i r co m m and. Not e : If th e i p sd i r directo ry is l isted and th ere are f il es in it, co ntact y o ur instructo r. T h is directo ry m ust b e em pty b ef o re co nf ig uring IP S . If th ere are no f il es in it y o u m ay pro ceed to co nf ig ure IP S . S t e p 2: Ve ri f y t h e I O S I PS si g n at u re p ac k ag e l o c at i o n an d T FT P se rv e r se t u p . a. V erif y co nnectiv ity b etw een R1 and P C-A, th e T F T P serv er, using th e p in g co m m and. b . S tart T f tpd32 o r o th er T F T P serv er and set th e def aul t directo ry to th e o ne w ith th e IP S sig nature pack ag e in it. T ak e no te o f th e f il enam e f o r use in th e nex t step. S t e p 3: A c c e ss S D M o n R 1. a. Run th e S DM appl icatio n, o r o pen a b ro w ser o n P C-A and start S DM b y entering th e R1 IP address 17 2.16 .1.1 in th e address f iel d. b . Lo g in as A d m i n 01 w ith a passw o rd o f A d m i n 01p a5 5 . E nter th e sam e usernam e and passw o rd f o r sub seq uent l o g in dial o g b o x es, if pro m pted. S t e p 4: U se t h e S D M I PS w i z ard t o c o n f i g u re I PS . Ne t L ab Use r s: It m ay b e necessary to co py th e tex t f ro m th e pub l ic k ey f il e b ef o re starting th e IP S co nf ig uratio n pro cess w ith S DM . If y o u are no t using Ne t L ab to perf o rm th e S BA g o to S tep 4a. O pen th e pub l ic k ey f il e and co py [ Ctrl + C] th e tex t th at is b etw een th e ph rase “k ey -string ” and th e w o rd “q uit.” T h is co ntent is g o ing to b e used in S tep 4e. T o k eep th e co ntent o n th e cl ipb o ard, do no t co py any th ing el se. W h en y o u reach S tep 4e, j ust paste th e co ntents o f th e f il e into S DM as instructed. a. Cl ick th e C on f i g u r e b utto n at th e to p o f th e S DM screen and th en sel ect I n t r u si on Pr e v e n t i on > C r e at e I PS. Cl ick th e L au n ch I PS Ru l e W i z ar d b utto n to b eg in th e IP S co nf ig uratio n. If pro m pted reg arding S DE E , cl ick O K . Cl ick Ne x t at th e w el co m e screen. b . Appl y th e IP S rul e in th e inb o und directio n f o r F astE th ernet0/1 and S erial 0/0/0. Cl ick Ne x t . c. In th e S ig nature F il e and P ub l ic K ey w indo w , specif y th e sig nature f il e w ith a URL and use T F T P to retriev e th e f il e f ro m P C-A. E nter th e IP address o f th e P C-A T F T P serv er and th e f il enam e. Cl ick O K . All contents are Copyright © 1992–20 0 9 Cisco S ystem s, I nc. All rights reserv ed . T his d ocu m ent is Cisco P u b lic I nf orm ation. P age 7 of 12
- 8. C C NA Se cu r i t y d. In th e S ig nature F il e and P ub l ic K ey w indo w , enter th e nam e o f th e pub l ic k ey f il e r e al m -ci sco.p u b . e. O pen th e pub l ic k ey f il e and co py [ Ctrl + C] th e tex t th at is b etw een th e ph rase “k ey -string ” and th e w o rd “q uit.” P aste [ Ctrl + V ] th e tex t into th e K e y f iel d in th e Co nf ig ure P ub l ic K ey sectio n. Cl ick Ne x t . f. In th e Co nf ig Lo catio n and Categ o ry w indo w , specif y f l ash : /i p sd i r / as th e l o catio n to sto re th e sig nature inf o rm atio n. Cl ick O K . g . In th e C h oose C at e g or y f iel d o f th e Co nf ig Lo catio n and Categ o ry w indo w , ch o o se b asi c. h . Cl ick Ne x t to displ ay th e S um m ary w indo w , and cl ick F i n i sh to del iv er th e co m m ands to th e ro uter. Cl ick O K . Not e : Al l o w th e sig nature co nf ig uratio n pro cess to co m pl ete. T h is can tak e sev eral m inutes. S t e p 5: S av e t h e ru n n i n g c o n f i g u rat i o n t o t h e st art u p c o n f i g u rat i o n . S t e p 6: R e p e at S t e p s 1 t h ro u g h 5 t o c o n f i g u re I PS o n R 3. B e su re t o ac c o u n t f o r di f f e re n c e s i n i n t e rf ac e s an d o t h e r v ari ab l e s. Part 3: Co n f i g u re a S i te -to -S i te I Ps e c V PN b e tw e e n R 1 an d R 3 w i th S D M In P art 3 o f th is l ab , y o u co nf ig ure an IP sec V P N tunnel b etw een R1 and R3 th at passes th ro ug h R2. Task 1: Configure t h e sit e-t o-sit e V PN on R 1 and R 3. S t e p 1: A c c e ss S D M o n R 1. a. Run th e S DM appl icatio n, o r o pen a b ro w ser o n P C-A and start S DM b y entering th e R1 IP address 17 2.16 .1.1 in th e address f iel d. b . Lo g in as A d m i n 01 w ith a passw o rd o f A d m i n 01p a5 5 . E nter th e sam e usernam e and passw o rd f o r sub seq uent l o g in dial o g b o x es, if pro m pted. S t e p 2: S t art t h e S D M VPN w i z ard t o c o n f i g u re R 1. a. Cl ick th e C on f i g u r e b utto n at th e to p o f th e S DM screen, and th en cl ick th e V PN b utto n. S el ect Si t e - t o-Si t e V PN f ro m th e l ist o f o ptio ns. T h e def aul t o ptio n is Create Si t e -t o-Si t e V PN. b . Cl ick th e L au n ch t h e se l e ct e d t ask b utto n to b eg in th e S DM S ite-to -S ite V P N w iz ard. c. O n th e initial S ite-to -S ite V P N w iz ard w indo w , th e Q u i ck Se t u p o ptio n is sel ected b y def aul t. Use th is o ptio n to co nf ig ure th e R1 side o f th e site-to -site V P N . S t e p 3: Co n f i g u re b asi c VPN c o n n e c t i o n i n f o rm at i o n se t t i n g s. a. F ro m th e V P N Co nnectio n Inf o rm atio n w indo w , sel ect th e interf ace f o r th e co nnectio n, w h ich sh o ul d b e R1 S erial 0/0/0. b . In th e P eer Identity sectio n, sel ect Pe e r w i t h st at i c ad d r e ss and enter th e IP address o f rem o te peer R3 S 0/0/1 (10.20.20.1). c. In th e Auth enticatio n sectio n, cl ick Pr e -sh ar e d k e y s, and enter th e pre-sh ared V P N k ey ci scov p n p a5 5 . Re-enter th e k ey f o r co nf irm atio n. d. In th e T r af f i c t o e n cr y p t po rtio n o f th e screen, specif y F astE th ernet 0/1 o f R1 as th e so urce interf ace. S pecif y th e IP address and sub net m ask o f th e R3 F astE th ernet 0/1 interf ace as th e destinatio n. T h ese setting s w il l b e m irro red w h en co nf ig uring R3. W h en f inish ed, cl ick Ne x t . S t e p 4: R e v i e w t h e su m m ary c o n f i g u rat i o n an d de l i v e r c o m m an ds t o t h e ro u t e r. a. Rev iew th e sum m ary o f th e Co nf ig uratio n w indo w . Do no t sel ect th e ch eck b o x f o r T est V P N co nnectiv ity af ter co nf ig uring . T h is is do ne af ter co nf ig uring R3. All contents are Copyright © 1992–20 0 9 Cisco S ystem s, I nc. All rights reserv ed . T his d ocu m ent is Cisco P u b lic I nf orm ation. P age 8 of 12
- 9. C C NA Se cu r i t y b . In th e Del iv er Co nf ig uratio n to ro uter w indo w , sel ect Sav e r u n n i n g con f i g t o r ou t e r ’s st ar t u p con f i g and cl ick th e D e l i v e r b utto n. S t e p 5: S av e t h e ru n n i n g -c o n f i g t o t h e st art u p -c o n f i g . S t e p 6: R e p e at S t e p s 1 t h ro u g h 5 t o c o n f i g u re t h e si t e -t o -si t e VPN o n R 3. B e su re t o ac c o u n t f o r di f f e re n c e s i n i n t e rf ac e s an d o t h e r v ari ab l e s. Ta s k 2 : Te s t t h e V P N b e t w e e n R1 a n d R3 U s i n g S D M . a. O n R1, use S DM to test th e IP sec V P N tunnel b etw een th e tw o ro uters. S el ect V PN > Si t e -t o-Si t e V PN and cl ick th e E d i t Si t e -t o-Si t e V PN tab . b . F ro m th e E d i t Si t e t o Si t e V PN tab , sel ect th e V P N and cl ick T e st T u n n e l . c. W h en th e V P N T ro ub l esh o o ting w indo w displ ay s, cl ick th e St ar t b utto n to h av e S DM start tro ub l esh o o ting th e tunnel . d. Initial peer co nnectiv ity m ay indicate f ail ure. W h en th e S DM W arning w indo w displ ay s indicating th at S DM w il l enab l e ro uter deb ug s and g enerate so m e tunnel traf f ic, cl ick Y e s to co ntinue. e. In th e nex t V P N T ro ub l esh o o ting w indo w , th e IP address o f th e R1 F a0/1 interf ace in th e so urce netw o rk is displ ay ed b y def aul t (17 2.16 .1.1). E nter th e IP address o f th e R3 F a0/1 interf ace in th e destinatio n netw o rk f iel d (17 2.16 .3.1) and cl ick C on t i n u e to b eg in th e deb ug g ing pro cess. f. If th e deb ug is successf ul , y o u sh o ul d see an Inf o rm atio n w indo w indicating th at tro ub l esh o o ting w as successf ul and th e tunnel is up. Cl ick O K to rem o v e th e w indo w . Not e : If y o u w ant to reset th e tunnel and test ag ain, y o u can cl ick th e C l e ar C on n e ct i on b utto n f ro m th e E dit S ite-to -S ite V P N w indo w . T h is can al so b e acco m pl ish ed at th e CLI using th e c l e a r c r y p t o s e s s io n co m m and. g . Displ ay th e running co nf ig f o r R3 b eg inning w ith th e f irst l ine th at co ntains th e string 0/0/1 to v erif y th at th e cry pto m ap is appl ied to S 0/0/1. h . Issue th e s h o w c r y p t o is a k m p s a co m m and o n R3 to v iew th e security asso ciatio n created. i. Issue th e s h o w c r y p t o ip s e c s a co m m and. H o w m any pack ets h av e b een receiv ed f ro m R1 and decry pted b y R3? _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ Part 4: S e c u re N e tw o rk S w i tc h e s Task 1: Configure Passwords and a Login Banner on S wit c h es S 1, S 2 and S 3. S t e p 1: Co n f i g u re t h e e n ab l e se c re t p assw o rd. Use an enab l e secret passw o rd o f cisco enapa55. S t e p 2: En c ry p t p l ai n t e xt p assw o rds. S t e p 3: Co n f i g u re t h e c o n so l e an d VT Y l i n e s. a. Co nf ig ure a co nso l e passw o rd o f cisco co npa55 and enab l e l o g in. S et th e ex ec-tim eo ut to l o g o ut af ter 5 m inutes o f inactiv ity . P rev ent co nso l e m essag es f ro m interrupting co m m and entry . b . Co nf ig ure a v ty l ines passw o rd o f ci scov t y p a5 5 and enab l e l o g in. S et th e ex ec-tim eo ut to l o g o ut af ter 5 m inutes o f inactiv ity . All contents are Copyright © 1992–20 0 9 Cisco S ystem s, I nc. All rights reserv ed . T his d ocu m ent is Cisco P u b lic I nf orm ation. P age 9 of 12
- 10. C C NA Se cu r i t y S t e p 4: Co n f i g u re a l o g i n w arn i n g b an n e r. Co nf ig ure a w arning to unauth o riz ed users w ith a m essag e-o f -th e-day (M O T D) b anner th at say s “Unauth o riz ed access strictl y pro h ib ited and pro secuted to th e f ul l ex tent o f th e l aw !” . S t e p 5: D i sab l e H T T P ac c e ss. H T T P access to th e sw itch is enab l ed b y def aul t. T o prev ent H T T P access, disab l e th e H T T P serv er and H T T P secure serv er. S t e p 6: R e p e at S t e p s 1 t h ro u g h 5 t o c o n f i g u re b asi c se t t i n g s o n sw i t c h e s S 2 an d S 3. Task 2 : S ec ure Trunk Port s S t e p 1: Co n f i g u re t ru n k p o rt s o n S 1 an d S 2. a. Co nf ig ure po rt F a0/1 o n S 1 as a trunk po rt. b . Co nf ig ure po rt F a0/1 o n S 2 as a trunk po rt. c. V erif y th at S 1 po rt F a0/1 is in trunk ing m o de. S t e p 2: Ch an g e t h e n at i v e VL A N f o r t h e t ru n k p o rt s o n S 1 an d S 2. Ch ang ing th e nativ e V LAN f o r trunk po rts to an unused V LAN h el ps prev ent V LAN h o pping attack s. a. S et th e nativ e V LAN o n th e S 1 F a0/1 trunk interf ace to an unused V LAN 9 9 . b . S et th e nativ e V LAN o n th e S 2 F a0/1 trunk interf ace to V LAN 9 9 . S t e p 3: Pre v e n t t h e u se o f D T P o n S 1 an d S 2. S et th e trunk po rts o n S 1 and S 2 so th at th ey do no t neg o tiate b y turning o f f th e g eneratio n o f DT P f ram es. S t e p 4: Ve ri f y t h e t ru n k i n g c o n f i g u rat i o n o n p o rt Fa0 / 1. S t e p 5: En ab l e st o rm c o n t ro l f o r b ro adc ast s. E nab l e sto rm co ntro l f o r b ro adcasts o n th e S 1 and S 2 trunk po rts w ith a 50 percent rising suppressio n l ev el . S t e p 6: Ve ri f y t h e c o n f i g u rat i o n o f Fa0 / 1 w i t h t h e sh o w ru n c o m m an d. Task 3: S ec ure Ac c ess Port s S t e p 1: D i sab l e t ru n k i n g o n S 1, S 2 an d S 3 ac c e ss p o rt s. a. O n S 1, co nf ig ure po rts F a0/5 and F 0/6 as access m o de o nl y . b . O n S 2, co nf ig ure F a0/18 as access m o de o nl y . c. O n S 3, co nf ig ure po rts F a0/5 and F a0/18 as access m o de o nl y . Task 4: Prot ec t Against S TP At t ac ks S t e p 1: En ab l e Po rt Fast o n S 1, S 2, an d S 3 ac c e ss p o rt s. P o rtF ast is co nf ig ured o n access po rts th at co nnect to a sing l e w o rk statio n o r serv er to enab l e th em to b eco m e activ e m o re q uick l y . All contents are Copyright © 1992–20 0 9 Cisco S ystem s, I nc. All rights reserv ed . T his d ocu m ent is Cisco P u b lic I nf orm ation. P age 10 of 12
- 11. C C NA Se cu r i t y a. E nab l e P o rtF ast o n th e S 1 F a0/5 and F a0/6 access po rts. b . E nab l e P o rtF ast o n th e S 2 F a0/18 access po rt. c. E nab l e P o rtF ast o n th e S 3 F a0/5 and F a0/18 access po rts. S t e p 2: En ab l e B PD U g u ard o n S 1, S 2, an d S 3 ac c e ss p o rt s. E nab l e BP DU g uard o n th e sw itch po rts prev io usl y co nf ig ured as access o nl y . Task 5: Configure Port S ec urit y and Disab l e Unused Port s S t e p 1: Co n f i g u re b asi c p o rt se c u ri t y t h e S 1, S 2, an d S 3 ac c e ss p o rt s. S h ut do w n al l end-user access po rts th at are in use and enab l e b asic def aul t po rt security . T h is sets th e m ax im um M AC addresses to 1 and th e v io l atio n actio n to sh utdo w n. Use th e s t ic k y o ptio n to al l o w th e secure M AC address th at is dy nam ical l y l earned o n a po rt to th e sw itch running co nf ig uratio n. Re-enab l e each access po rt to w h ich po rt security w as appl ied. S t e p 2: D i sab l e u n u se d p o rt s o n S 1, S 2 an d S 3. As a f urth er security m easure, disab l e any po rts no t b eing used o n th e sw itch . a. P o rts F a0/1, F a0/5, and F a0/6 are used o n sw itch S 1. S h ut do w n th e rem aining F ast E th ernet po rts and th e tw o G ig ab it E th ernet po rts. b . P o rts F a0/1 and F a0/18 are used o n sw itch S 2. S h ut do w n th e rem aining F ast E th ernet po rts and th e tw o G ig ab it E th ernet po rts. c. P o rts F a0/5 and F a0/18 are used o n sw itch S 3. S h ut do w n th e rem aining F ast E th ernet po rts and th e tw o G ig ab it E th ernet po rts. S t e p 3: S av e t h e ru n n i n g -c o n f i g t o t h e st art u p -c o n f i g f o r e ac h sw i t c h . All contents are Copyright © 1992–20 0 9 Cisco S ystem s, I nc. All rights reserv ed . T his d ocu m ent is Cisco P u b lic I nf orm ation. P age 11 of 12
- 12. C C NA Se cu r i t y Rou t e r I n t e r f a c e S u m m a r y Ta b le Rou t e r I n t e r f ace Su m m ar y Ro uter M o del E th ernet Interf ace E th ernet Interf ace S erial Interf ace S erial Interf ace # 1 # 2 # 1 # 2 17 00 F ast E th ernet 0 F ast E th ernet 1 S erial 0 (S 0) S erial 1 (S 1) (F A0) (F A1) 1800 F ast E th ernet 0/0 F ast E th ernet 0/1 S erial 0/0/0 S erial 0/0/1 (F A0/0) (F A0/1) (S 0/0/0) (S 0/0/1) 26 00 F ast E th ernet 0/0 F ast E th ernet 0/1 S erial 0/0 (S 0/0) S erial 0/1 (S 0/1) (F A0/0) (F A0/1) 2800 F ast E th ernet 0/0 F ast E th ernet 0/1 S erial 0/0/0 S erial 0/0/1 (F A0/0) (F A0/1) (S 0/0/0) (S 0/0/1) Not e : T o f ind o ut h o w th e ro uter is co nf ig ured, l o o k at th e interf aces to identif y th e ty pe o f ro uter and h o w m any interf aces th e ro uter h as. T h ere is no w ay to ef f ectiv el y l ist al l th e co m b inatio ns o f co nf ig uratio ns f o r each ro uter cl ass. T h is tab l e incl udes identif iers f o r th e po ssib l e co m b inatio ns o f E th ernet and S erial interf aces in th e dev ice. T h e tab l e do es no t incl ude any o th er ty pe o f interf ace, ev en th o ug h a specif ic ro uter m ay co ntain o ne. An ex am pl e o f th is m ig h t b e an IS DN BRI interf ace. T h e string in parenth esis is th e l eg al ab b rev iatio n th at can b e used in Cisco IO S co m m ands to represent th e interf ace. All contents are Copyright © 1992–20 0 9 Cisco S ystem s, I nc. All rights reserv ed . T his d ocu m ent is Cisco P u b lic I nf orm ation. P age 12 of 12