Bit Oriented Protocols in Data Communication DC23
•Als PPT, PDF herunterladen•
3 gefällt mir•3,755 views
The document contains descriptions and figures related to HDLC (High-Level Data Link Control) configuration, modes, frame types, fields, bit stuffing, addressing, control, polling, and examples of use in different network configurations. There are over 20 figures from a McGraw-Hill textbook covering technical aspects of HDLC for network communication.
Melden
Teilen
Melden
Teilen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
Andere mochten auch
Andere mochten auch (20)
Character, behavior and protocol of pso final copy

Character, behavior and protocol of pso final copy
Analog to Digital Encoding in Data Communication DC9

Analog to Digital Encoding in Data Communication DC9
Multiplexing and switching(TDM ,FDM, Data gram, circuit switching)

Multiplexing and switching(TDM ,FDM, Data gram, circuit switching)
Ähnlich wie Bit Oriented Protocols in Data Communication DC23
Ähnlich wie Bit Oriented Protocols in Data Communication DC23 (20)
Mehr von koolkampus
Mehr von koolkampus (20)
Error Detection and Correction in Data Communication DC18

Error Detection and Correction in Data Communication DC18
Transmission of Digital Data(Data Communication) DC11

Transmission of Digital Data(Data Communication) DC11
Analog to Analog Modulation in Data Communication DC10

Analog to Analog Modulation in Data Communication DC10
Authentication Application in Network Security NS4

Authentication Application in Network Security NS4
Kürzlich hochgeladen
Kürzlich hochgeladen (20)
Human Factors of XR: Using Human Factors to Design XR Systems

Human Factors of XR: Using Human Factors to Design XR Systems
Handwritten Text Recognition for manuscripts and early printed texts

Handwritten Text Recognition for manuscripts and early printed texts
Azure Monitor & Application Insight to monitor Infrastructure & Application

Azure Monitor & Application Insight to monitor Infrastructure & Application
Factors to Consider When Choosing Accounts Payable Services Providers.pptx

Factors to Consider When Choosing Accounts Payable Services Providers.pptx
Integration and Automation in Practice: CI/CD in Mule Integration and Automat...

Integration and Automation in Practice: CI/CD in Mule Integration and Automat...
SQL Database Design For Developers at php[tek] 2024![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![SQL Database Design For Developers at php[tek] 2024](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
SQL Database Design For Developers at php[tek] 2024
Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

Transcript: #StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024

#StandardsGoals for 2024: What’s new for BISAC - Tech Forum 2024
How to Remove Document Management Hurdles with X-Docs?

How to Remove Document Management Hurdles with X-Docs?
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...

Transforming Data Streams with Kafka Connect: An Introduction to Single Messa...
Swan(sea) Song – personal research during my six years at Swansea ... and bey...

Swan(sea) Song – personal research during my six years at Swansea ... and bey...
Bit Oriented Protocols in Data Communication DC23
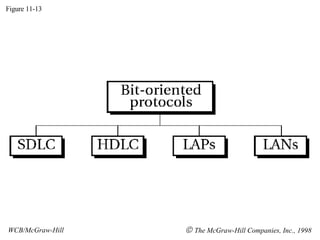
- 1. Figure 11-13 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 2. Figure 11-14 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 HDLC Configuration
- 3. Figure 11-14-continued WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 HDLC Configuration
- 4. Figure 11-14-continued WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 HDLC Configuration
- 5. Figure 11-15 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 HDLC Modes
- 6. Figure 11-16 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 HDLC Frame Types
- 7. Figure 11-16-continued WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 HDLC Frame Types
- 8. Figure 11-16-continued WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 HDLC Frame Types
- 9. Figure 11-17 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 HDLC Flag Field
- 10. Figure 11-18 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Bit Stuffing
- 11. Figure 11-19 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 HDLC Address Field
- 12. Figure 11-20 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 HDLC Control Field
- 13. Figure 11-21 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Poll/Final
- 14. Figure 11-22 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 HDLC Information Field
- 15. Figure 11-23 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 HDLC FCS Field
- 16. Figure 11-24 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 17. Figure 11-25 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Use of P/F Field
- 18. Figure 11-25-continued WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Use of P/F Field
- 19. Figure 11-25-continued WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Use of P/F Field
- 20. Figure 11-25-continued WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Use of P/F Field
- 21. Figure 11-25-continued WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Use of P/F Field
- 22. Figure 11-26 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 U-Frame Control Field
- 23. Figure 11-26-continued WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 U-Frame Control Field
- 24. Figure 11-27 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Polling Example
- 25. Figure 11-28 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Selecting Example
- 26. Figure 11-29 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Peer-to-Peer Example
- 27. Figure 11-29-continued WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Peer-to-Peer Example