CRC in Data Communication DC19
•Als PPT, PDF herunterladen•
3 gefällt mir•1,917 views
Melden
Teilen
Melden
Teilen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (16)
Ähnlich wie CRC in Data Communication DC19
Ähnlich wie CRC in Data Communication DC19 (20)
Mehr von koolkampus
Mehr von koolkampus (17)
Transmission of Digital Data(Data Communication) DC11

Transmission of Digital Data(Data Communication) DC11
Analog to Digital Encoding in Data Communication DC9

Analog to Digital Encoding in Data Communication DC9
Analog to Analog Modulation in Data Communication DC10

Analog to Analog Modulation in Data Communication DC10
Authentication Application in Network Security NS4

Authentication Application in Network Security NS4
Kürzlich hochgeladen
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Kürzlich hochgeladen (20)
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Understanding Discord NSFW Servers A Guide for Responsible Users.pdf

Understanding Discord NSFW Servers A Guide for Responsible Users.pdf
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
HTML Injection Attacks: Impact and Mitigation Strategies

HTML Injection Attacks: Impact and Mitigation Strategies
Advantages of Hiring UIUX Design Service Providers for Your Business

Advantages of Hiring UIUX Design Service Providers for Your Business
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
CRC in Data Communication DC19
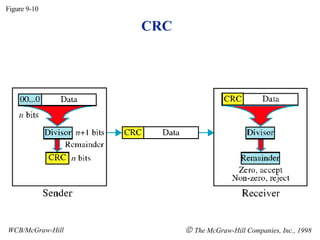
- 1. CRC Figure 9-10 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 2. Binary Division Figure 9-11 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 3. Polynomial Figure 9-12 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 4. Figure 9-13 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Polynomial and Divisor
- 5. Standard Polynomials Figure 9-14 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 6. Checksum Figure 9-15 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 7. Figure 9-16 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Data Unit and Checksum
- 8. Error Correction Figure 9-17 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 9. Hamming Code Figure 9-18 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 10. Figure 9-19 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Hamming Code
- 11. Figure 9-19-continued WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Hamming Code
- 12. Figure 9-20 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Example of Hamming Code
- 13. Single-bit error Figure 9-21 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998
- 14. Figure 9-22 WCB/McGraw-Hill The McGraw-Hill Companies, Inc., 1998 Error Detection