Dual Persona example
•Als PPTX, PDF herunterladen•
0 gefällt mir•124 views
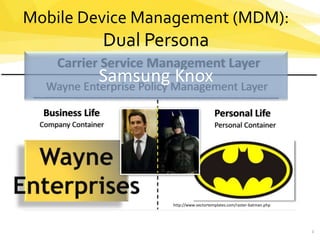
Mobile Device Management uses a dual persona approach to separate corporate and personal data and usage on mobile devices through separate containers. It provides policy management controls over business data and access through the Knox Enterprise Mobility Management software and carrier service layers. This allows companies to securely manage mobile business usage and data while separating it from personal activities on devices.
Melden
Teilen
Melden
Teilen
Empfohlen
Weitere ähnliche Inhalte
Ähnlich wie Dual Persona example
Ähnlich wie Dual Persona example (20)
Symantec Enterprise Mobility - Mobile World Congress February 2012

Symantec Enterprise Mobility - Mobile World Congress February 2012
Magic quadrant for enterprise mobility management suites

Magic quadrant for enterprise mobility management suites
Mobile Device Management: Taking Conainerisation to the Next Level

Mobile Device Management: Taking Conainerisation to the Next Level
Enterprise Mobility Management and its challenges - Phdassistance.com

Enterprise Mobility Management and its challenges - Phdassistance.com
Future proof and extend your IAM to Mobile Platforms and any connected device

Future proof and extend your IAM to Mobile Platforms and any connected device
MobileIron's Enterprise Solution for App Security and Management

MobileIron's Enterprise Solution for App Security and Management
Reference Security Architecture for Mobility- Insurance

Reference Security Architecture for Mobility- Insurance
Friendly Technologies - TR-069, IoT Management, Smart Home Service Delivery

Friendly Technologies - TR-069, IoT Management, Smart Home Service Delivery
Telus Analyst Briefing mobile security and managed mobility sept 2012 v6 gc ss

Telus Analyst Briefing mobile security and managed mobility sept 2012 v6 gc ss
G05.2012 magic quadrant for mobile device management software

G05.2012 magic quadrant for mobile device management software
how_to_balance_security_and_productivity_with_famoc_and_samsung_knox

how_to_balance_security_and_productivity_with_famoc_and_samsung_knox
Net motion wireless-and_frost-sullivan_a-new-mobilty_ps

Net motion wireless-and_frost-sullivan_a-new-mobilty_ps
Moving Beyond MDM: Why Legacy Mobile Security Products Don't Work

Moving Beyond MDM: Why Legacy Mobile Security Products Don't Work
Dual Persona example
- 1. Mobile Device Management (MDM): Dual Persona 1 Business Life Company Container http://www.vectortemplates.com/raster-batman.php Personal Life Personal Container Wayne Enterprise Policy Management Layer Carrier Service Management Layer Samsung Knox
- 2. Mobile Device Management (MDM): Dual Persona What : o Dual persona enabler o Separates: Usage into Corporate and Individual billing categories o Containers: Device security for mobile business data / mobile access o Policy control management o Roaming policy o Video blocking o Lock out device from enterprise if compromised How : o Knox Enterprise Mobility Management (EMM) and handset software client o MVNO partner for proof of concept testing and business trial Differentiators : o Grab share of market – Expand to Business offerings o Grow Revenue – Incremental Enterprise Revenue Streams on top of personal plans 2
