Chapter 5
•Als PPTX, PDF herunterladen•
0 gefällt mir•190 views
Melden
Teilen
Melden
Teilen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Andere mochten auch
Andere mochten auch (17)
Zermatt and the Matterhorn - A Wintery Destination in Switzerland

Zermatt and the Matterhorn - A Wintery Destination in Switzerland
обзор технических решений в области энергосбережения

обзор технических решений в области энергосбережения
Ähnlich wie Chapter 5
Ähnlich wie Chapter 5 (20)
ANALYSIS AND COMPARISON OF SYMMETRIC KEY CRYPTOGRAPHIC ALGORITHMS BASED ON VA...

ANALYSIS AND COMPARISON OF SYMMETRIC KEY CRYPTOGRAPHIC ALGORITHMS BASED ON VA...
Encryption and Compression of Audio-Video Data Using Enhanced AES and J-Bit A...

Encryption and Compression of Audio-Video Data Using Enhanced AES and J-Bit A...
AES-BASED IMAGE ENCRYPTION AND DECRYPTION FOR ROBUST DATA SECURITY AND DEFENS...

AES-BASED IMAGE ENCRYPTION AND DECRYPTION FOR ROBUST DATA SECURITY AND DEFENS...
Dynamic selection of symmetric key cryptographic algorithms for securing data...

Dynamic selection of symmetric key cryptographic algorithms for securing data...
Dynamic selection of symmetric key cryptographic algorithms for securing data...

Dynamic selection of symmetric key cryptographic algorithms for securing data...
Kürzlich hochgeladen
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Enterprise Knowledge’s Urmi Majumder, Principal Data Architecture Consultant, and Fernando Aguilar Islas, Senior Data Science Consultant, presented "Driving Behavioral Change for Information Management through Data-Driven Green Strategy" on March 27, 2024 at Enterprise Data World (EDW) in Orlando, Florida.
In this presentation, Urmi and Fernando discussed a case study describing how the information management division in a large supply chain organization drove user behavior change through awareness of the carbon footprint of their duplicated and near-duplicated content, identified via advanced data analytics. Check out their presentation to gain valuable perspectives on utilizing data-driven strategies to influence positive behavioral shifts and support sustainability initiatives within your organization.
In this session, participants gained answers to the following questions:
- What is a Green Information Management (IM) Strategy, and why should you have one?
- How can Artificial Intelligence (AI) and Machine Learning (ML) support your Green IM Strategy through content deduplication?
- How can an organization use insights into their data to influence employee behavior for IM?
- How can you reap additional benefits from content reduction that go beyond Green IM?
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Kürzlich hochgeladen (20)
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Boost PC performance: How more available memory can improve productivity

Boost PC performance: How more available memory can improve productivity
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
[2024]Digital Global Overview Report 2024 Meltwater.pdf![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![[2024]Digital Global Overview Report 2024 Meltwater.pdf](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
[2024]Digital Global Overview Report 2024 Meltwater.pdf
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
From Event to Action: Accelerate Your Decision Making with Real-Time Automation

From Event to Action: Accelerate Your Decision Making with Real-Time Automation
Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024

Bajaj Allianz Life Insurance Company - Insurer Innovation Award 2024
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff

Strategize a Smooth Tenant-to-tenant Migration and Copilot Takeoff
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Chapter 5
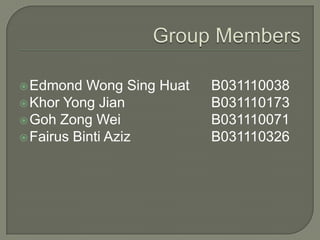
- 1. Edmond Wong Sing Huat B031110038 Khor Yong Jian B031110173 Goh Zong Wei B031110071 Fairus Binti Aziz B031110326
- 3. Abstract Syntax Notation (ASN.1) is an ISO standard that addresses the issue of representing, encoding, transmitting, and decoding data structures. It consists of two parts: 1. An abstract syntax that describes data structures in an unambiguous way. Use “ integers”, “character strings”, and “structures” rather than bits and bytes. 2. A transfer syntax that describes the bit stream encoding of ASN.1 data objects.
- 4. The main reasons for the success of ASN.1 is that it is associated with several standardized encoding rules such as: ◦ Basic Encoding Rules (BER) - X.209 ◦ Canonical Encoding Rules (CER) ◦ Distinguished Encoding Rules (DER) ◦ Packed Encoding Rules (PER) and ◦ XER Encoding Rules (XER). These encoding rules describe how the values defined in ASN.1 should be encoded for transmission, regardless of machine, programming language, or how it is represented in an application program.
- 5. Example of ASN.1’S abstract syntax: Student ::= SEQUENCE { name [0] IMPLICIT OCTET STRING OPTIONAL, grad [1] IMPLICIT BOOLEAN OPTIONAL DEFAULT FALSE, gpa [2] IMPLICIT REAL OPTIONAL, id [3] IMPLICIT INTEGER, bday [4] IMPLICIT OCTET STRING OPTIONAL }
- 6. Though initially used for specifying the email protocol within the Open Systems Interconnection environment, ASN.1 has since then been adopted for a wide range of other applications, as in network management, secure email, cellular telephony, air traffic control, and voice and video over the Internet.
- 7. Though initially used for specifying the email protocol within the Open Systems Interconnection environment, ASN.1 has since then been adopted for a wide range of other applications, as in network management, secure email, cellular telephony, air traffic control, and voice and video over the Internet.
- 8. Sun Microsystems's External Data Representation (XDR) is much simpler than ASN.1, but less powerful. For instance: 1. XDR uses implicit typing. Communicating peers must know the type of any exchanged data. In contrast, ASN.1 uses explicit typing; it includes type information as part of the transfer syntax. 2. In XDR, all data is transferred in units of 4 bytes. Numbers are transferred in network order, most significant byte first.
- 9. 4 bytes of XDR message:
- 10. 3. Strings consist of a 4 byte length, followed by the data (and perhaps padding in the last byte). 4. Defined types include: integer, enumeration, Boolean, floating point, fixed length array, structures, plus others. One advantage that XDR has over ASN.1 is that current implementations of ASN.1 execute significantly slower than XDR.
- 11. " The message “£100 is about !150” could become Content-Transfer-Encoding: quoted-printable Content-Type: text/plain; charset=ISO-8859- 15 MIME-Version: 1.0 =A3100 is about =A4150
- 12. or Content-Transfer-Encoding: base64 Content-Type: text/plain; charset=ISO-8859- 15 MIME-Version: 1.0 ozEwMCBpcyBhYm91dCCkMTUwCg=49
- 14. Reduces the number of bits contained in the information. Sometimes programs need to send more data in a timely fashion than the bandwidth of the network supports. Need to compress the data at the sender and decompress it at the receiver.
- 15. In terms of storage, the capacity of a storage device can be effectively increased with methods that compresses a body of data. The bandwidth of a digital communication link can be effectively increased by compressing data at the sending end and decompressing data at the receiving end.
- 16. Lossless Compression – data is compressed and can be uncompressed without loss of information. These are referred to as bit-preserving or reversible compression systems. Lossy Compression – aim to obtain the best possible fidelity for a given bit-rate or minimizing the bit-rate to achieve a given fidelity measure. Most suited to video and audio compression techniques
- 17. Lossless - Image quality is not reduced. Use in: artificial images that contain sharp- edged lines such as technical drawings, textual graphics, comics, maps or logos.
- 18. Lossy - reduces image quality. Cannot get the original image back & lose some information. Use in: natural images such as photos of landscapes
- 19. Lossless - allows one to preserve an exact copy of one's audio files Usage: For archival purposes, editing, audio quality.
- 20. Lossy - irreversible changes , achieves far greater compression, use psychoacoustics to recognize that not all data in an audio stream can be perceived by the human auditory system. Usage: distribution of streaming audio, or interactive applications
- 21. • Start by encoding the first frame using a still image compression method. • It should then encode each successive frame by identifying the differences between the frame and its predecessor, and encoding these differences. If the frame is very different from its predecessor it should be coded independently of any other frame.
- 22. In the video compression literature, a frame that is coded using its predecessor is called inter frame (or just inter), while a frame that is coded independently is called intra frame (or just intra).
- 24. • To carry sensitive information, a system must be able to assure privacy. • One way to safeguard data from attacks is encrypting the data.
- 25. • Encryption – sender transform original information (plaintext) to another form (ciphertext) by a function that is parameterized by a key. • Decryption – reverses the original process to transform the message (ciphertext) back to its original form (plaintext).
- 27. Symmetric Keys – use same key to encrypt and decrypt a message.
- 28. Asymmetric Keys -2 keys are needed (public key and private key); 1 key to encrypt, another key to decrypt and vice versa.
- 29. Protection Description Confidentiality Allow only authorized users to access information. Authentication Verify who the sender was and trust the sender is who they claim to be. Integrity Trust the information has not been altered No repudiation Ensure that the sender or receiver cannot deny that a message was sent or received. Access Control Restrict availability to information.