Dataveillance
•Download as PPTX, PDF•
1 like•523 views
The following presentation took place at the 2012 World Game Protection Conference in Las Vegas http://www.worldgameprotection.com/conference/speakers/
Report
Share
Report
Share
Recommended
More Related Content
Similar to Dataveillance
Similar to Dataveillance (20)
The Benefits of Having Nerds On Site Monitoring Your Technology

The Benefits of Having Nerds On Site Monitoring Your Technology
The Benefits of Having Nerds On Site Monitoring Your Technology

The Benefits of Having Nerds On Site Monitoring Your Technology
Threat Hunting by Falgun Rathod - Cyber Octet Private Limited

Threat Hunting by Falgun Rathod - Cyber Octet Private Limited
Social Distance Your IBM i from Cybersecurity Risk

Social Distance Your IBM i from Cybersecurity Risk
Recently uploaded
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Recently uploaded (20)
Apidays Singapore 2024 - Scalable LLM APIs for AI and Generative AI Applicati...

Apidays Singapore 2024 - Scalable LLM APIs for AI and Generative AI Applicati...
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
Powerful Google developer tools for immediate impact! (2023-24 C)

Powerful Google developer tools for immediate impact! (2023-24 C)
Apidays Singapore 2024 - Modernizing Securities Finance by Madhu Subbu

Apidays Singapore 2024 - Modernizing Securities Finance by Madhu Subbu
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...

Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
A Beginners Guide to Building a RAG App Using Open Source Milvus

A Beginners Guide to Building a RAG App Using Open Source Milvus
EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER

EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER
Navi Mumbai Call Girls 🥰 8617370543 Service Offer VIP Hot Model

Navi Mumbai Call Girls 🥰 8617370543 Service Offer VIP Hot Model
Dataveillance
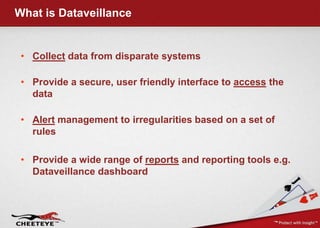
- 1. What is Dataveillance • Collect data from disparate systems • Provide a secure, user friendly interface to access the data • Alert management to irregularities based on a set of rules • Provide a wide range of reports and reporting tools e.g. Dataveillance dashboard
- 2. Collect Occurrence Book
- 3. Collect & Access Collusion Overview Collusion Report Break List
- 4. Access Collusion Detail Transaction List Tips Detailed Player Profile Video Click through
- 5. Access Debarments
- 6. Alert Biggest Winner Alerts
- 7. Alert Biggest Winner Detail Title 31 Inputs Big Winning Patterns
- 8. Alert Standard Deviation • The objective is to identify players with a history of consistently beating the casino. If a player wins over a long period of time while playing at a disadvantage to the house, something is usually up. Analysis is typically on a player with more than 300 hours’ worth of playing time • Standard deviations are calculated by using the underlying odds of the type of bet being placed and the type of game being played
- 9. Report Compliance Dashboard
- 10. Report Card Control Dashboard
- 11. Report Card Control
- 12. Report Slots Review
- 13. Report Slots Graphical Review
- 14. Report Fills & Credits Audit
