From hybernation file to malware analysis with volatility
•
1 gefällt mir•2,661 views
Howto on creating a memdump file from a hybernationfile, followed by
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Empfohlen
Advanced malware analysis training session 7 malware memory forensicsAdvanced malware analysis training session 7 malware memory forensics

Advanced malware analysis training session 7 malware memory forensicsCysinfo Cyber Security Community
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (11)
Avg Technologies Vawtrak Banking Trojan White Paper

Avg Technologies Vawtrak Banking Trojan White Paper
Ähnlich wie From hybernation file to malware analysis with volatility
Advanced malware analysis training session 7 malware memory forensicsAdvanced malware analysis training session 7 malware memory forensics

Advanced malware analysis training session 7 malware memory forensicsCysinfo Cyber Security Community
Ähnlich wie From hybernation file to malware analysis with volatility (20)
Cyber Defense Forensic Analyst - Real World Hands-on Examples

Cyber Defense Forensic Analyst - Real World Hands-on Examples
Windows Registry Forensics with Volatility Framework

Windows Registry Forensics with Volatility Framework
How to Avoid the Spying of EEUU & other Practical Solutions Computing: Protec...

How to Avoid the Spying of EEUU & other Practical Solutions Computing: Protec...
Advanced malware analysis training session 7 malware memory forensics

Advanced malware analysis training session 7 malware memory forensics
SANS Digital Forensics and Incident Response Poster 2012

SANS Digital Forensics and Incident Response Poster 2012
841- Advanced Computer ForensicsUnix Forensics LabDue Date.docx

841- Advanced Computer ForensicsUnix Forensics LabDue Date.docx
Advanced Malware Analysis Training Session 7 - Malware Memory Forensics

Advanced Malware Analysis Training Session 7 - Malware Memory Forensics
Reversing & malware analysis training part 9 advanced malware analysis

Reversing & malware analysis training part 9 advanced malware analysis
Mehr von Christiaan Beek
Mehr von Christiaan Beek (7)
We-built-a-honeypot-and-p4wned-ransomware-developers-too

We-built-a-honeypot-and-p4wned-ransomware-developers-too
"There's a pot of Bitcoins behind the ransomware rainbow"

"There's a pot of Bitcoins behind the ransomware rainbow"
Kürzlich hochgeladen
A Principled Technologies deployment guide
Conclusion
Deploying VMware Cloud Foundation 5.1 on next gen Dell PowerEdge servers brings together critical virtualization capabilities and high-performing hardware infrastructure. Relying on our hands-on experience, this deployment guide offers a comprehensive roadmap that can guide your organization through the seamless integration of advanced VMware cloud solutions with the performance and reliability of Dell PowerEdge servers. In addition to the deployment efficiency, the Cloud Foundation 5.1 and PowerEdge solution delivered strong performance while running a MySQL database workload. By leveraging VMware Cloud Foundation 5.1 and PowerEdge servers, you could help your organization embrace cloud computing with confidence, potentially unlocking a new level of agility, scalability, and efficiency in your data center operations.Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...

Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...Principled Technologies
Kürzlich hochgeladen (20)
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving

Repurposing LNG terminals for Hydrogen Ammonia: Feasibility and Cost Saving
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...

Apidays Singapore 2024 - Building Digital Trust in a Digital Economy by Veron...
ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke

ProductAnonymous-April2024-WinProductDiscovery-MelissaKlemke
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Scaling API-first – The story of a global engineering organization

Scaling API-first – The story of a global engineering organization
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...

Workshop - Best of Both Worlds_ Combine KG and Vector search for enhanced R...
Exploring the Future Potential of AI-Enabled Smartphone Processors

Exploring the Future Potential of AI-Enabled Smartphone Processors
Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...

Deploy with confidence: VMware Cloud Foundation 5.1 on next gen Dell PowerEdg...
From hybernation file to malware analysis with volatility
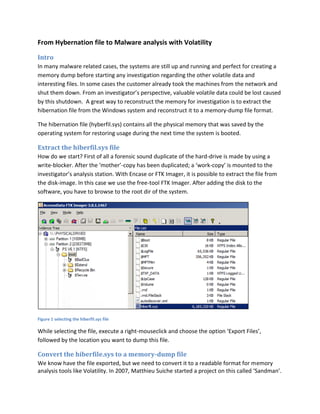
- 1. From Hybernation file to Malware analysis with Volatility Intro In many malware related cases, the systems are still up and running and perfect for creating a memory dump before starting any investigation regarding the other volatile data and interesting files. In some cases the customer already took the machines from the network and shut them down. From an investigator’s perspective, valuable volatile data could be lost caused by this shutdown. A great way to reconstruct the memory for investigation is to extract the hibernation file from the Windows system and reconstruct it to a memory-dump file format. The hibernation file (hyberfil.sys) contains all the physical memory that was saved by the operating system for restoring usage during the next time the system is booted. Extract the hiberfil.sys file How do we start? First of all a forensic sound duplicate of the hard-drive is made by using a write-blocker. After the ‘mother’-copy has been duplicated; a ‘work-copy’ is mounted to the investigator’s analysis station. With Encase or FTK Imager, it is possible to extract the file from the disk-image. In this case we use the free-tool FTK Imager. After adding the disk to the software, you have to browse to the root dir of the system. Figure 1 selecting the hiberfil.sys file While selecting the file, execute a right-mouseclick and choose the option ‘Export Files’, followed by the location you want to dump this file. Convert the hiberfile.sys to a memory-dump file We know have the file exported, but we need to convert it to a readable format for memory analysis tools like Volatility. In 2007, Matthieu Suiche started a project on this called ‘Sandman’.
- 2. This project was started to better investigate the hiberfil.sys file and what data could be extracted. One of the scripts Matthieu wrote was able to convert the hiberfil.sys file into a memory-dump format. This script and more was later adopted into Moonsols memory dump/converting toolkit. Moonsol is offering a community and enterprise edition of this toolkit. The community edition has the tool hibr2bin that is compatible with 32bit hibernation files of XP/2003/2008 & Vista. After downloading the tool we are going to convert our extracted hiberfil.sys file towards a bin file that can be used for analysis with volatility. The usage of the tool is pretty straight forward: Hibr2bin.exe <input file> <output file>: After this has been completed we have a file that can be imported to Volatility. Volatility When using Volatility, I prefer to use a ‘forensic order’ of using the plugins: Identify Image: plugin: imageinfo Identify suspicious processes: plugin: pslist & psscan Identify active/closed/hidden cons plugin: connections & connscan2, socks & sockscan2 Identify suspicious dll’s, open/hidden/closed files: plugin: dlllist , files & fileobjscan These plugins are followed by the plugin ‘malfind’ and others related to the case.
