Q3 2013 Global DDoS Attacks | DDoS Attack Statistics
•
0 gefällt mir•445 views
In Q3 2013, malicious actors shifted to reflection and amplification (DrDoS) attacks to launch more powerful DDoS attacks with fewer resources. This graphical analysis of attacks against Prolexic’s global client base showed an increase in reflection attacks and UDP floods and a decline in the use of SYN floods.
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Ähnlich wie Q3 2013 Global DDoS Attacks | DDoS Attack Statistics
Ähnlich wie Q3 2013 Global DDoS Attacks | DDoS Attack Statistics (14)
Industry Insights & Cloud Skeptics - How Enterprises Use The Cloud And What S...

Industry Insights & Cloud Skeptics - How Enterprises Use The Cloud And What S...
SecurityGen-whitepaper-gtp-firewall- security 5G.pdf

SecurityGen-whitepaper-gtp-firewall- security 5G.pdf
SecurityGen whitepaper GTP vulnerabilities - A cause for concern in 5G and LT...

SecurityGen whitepaper GTP vulnerabilities - A cause for concern in 5G and LT...
SecurityGen Sentinel - Your User-Friendly Guardian in Telecom Security.pdf

SecurityGen Sentinel - Your User-Friendly Guardian in Telecom Security.pdf
Secure Your Network with Confidence Understanding - GTP Protocols by Security...

Secure Your Network with Confidence Understanding - GTP Protocols by Security...
FLOODING ATTACK DETECTION AND MITIGATION IN SDN WITH MODIFIED ADAPTIVE THRESH...

FLOODING ATTACK DETECTION AND MITIGATION IN SDN WITH MODIFIED ADAPTIVE THRESH...
Scaling service provider business with DDoS-mitigation-as-a-service

Scaling service provider business with DDoS-mitigation-as-a-service
DDoS Threats Landscape : Countering Large-scale DDoS attacks

DDoS Threats Landscape : Countering Large-scale DDoS attacks
DDoS Threat Landscape - Challenges faced by Network Operators

DDoS Threat Landscape - Challenges faced by Network Operators
Cloud service providers survey breaking through the cloud adoption barriers- ...

Cloud service providers survey breaking through the cloud adoption barriers- ...
Kürzlich hochgeladen
💉💊+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHABI}}+971581248768
+971581248768 Mtp-Kit (500MG) Prices » Dubai [(+971581248768**)] Abortion Pills For Sale In Dubai, UAE, Mifepristone and Misoprostol Tablets Available In Dubai, UAE CONTACT DR.Maya Whatsapp +971581248768 We Have Abortion Pills / Cytotec Tablets /Mifegest Kit Available in Dubai, Sharjah, Abudhabi, Ajman, Alain, Fujairah, Ras Al Khaimah, Umm Al Quwain, UAE, Buy cytotec in Dubai +971581248768''''Abortion Pills near me DUBAI | ABU DHABI|UAE. Price of Misoprostol, Cytotec” +971581248768' Dr.DEEM ''BUY ABORTION PILLS MIFEGEST KIT, MISOPROTONE, CYTOTEC PILLS IN DUBAI, ABU DHABI,UAE'' Contact me now via What's App…… abortion Pills Cytotec also available Oman Qatar Doha Saudi Arabia Bahrain Above all, Cytotec Abortion Pills are Available In Dubai / UAE, you will be very happy to do abortion in Dubai we are providing cytotec 200mg abortion pill in Dubai, UAE. Medication abortion offers an alternative to Surgical Abortion for women in the early weeks of pregnancy. We only offer abortion pills from 1 week-6 Months. We then advise you to use surgery if its beyond 6 months. Our Abu Dhabi, Ajman, Al Ain, Dubai, Fujairah, Ras Al Khaimah (RAK), Sharjah, Umm Al Quwain (UAQ) United Arab Emirates Abortion Clinic provides the safest and most advanced techniques for providing non-surgical, medical and surgical abortion methods for early through late second trimester, including the Abortion By Pill Procedure (RU 486, Mifeprex, Mifepristone, early options French Abortion Pill), Tamoxifen, Methotrexate and Cytotec (Misoprostol). The Abu Dhabi, United Arab Emirates Abortion Clinic performs Same Day Abortion Procedure using medications that are taken on the first day of the office visit and will cause the abortion to occur generally within 4 to 6 hours (as early as 30 minutes) for patients who are 3 to 12 weeks pregnant. When Mifepristone and Misoprostol are used, 50% of patients complete in 4 to 6 hours; 75% to 80% in 12 hours; and 90% in 24 hours. We use a regimen that allows for completion without the need for surgery 99% of the time. All advanced second trimester and late term pregnancies at our Tampa clinic (17 to 24 weeks or greater) can be completed within 24 hours or less 99% of the time without the need surgery. The procedure is completed with minimal to no complications. Our Women's Health Center located in Abu Dhabi, United Arab Emirates, uses the latest medications for medical abortions (RU-486, Mifeprex, Mifegyne, Mifepristone, early options French abortion pill), Methotrexate and Cytotec (Misoprostol). The safety standards of our Abu Dhabi, United Arab Emirates Abortion Doctors remain unparalleled. They consistently maintain the lowest complication rates throughout the nation. Our Physicians and staff are always available to answer questions and care for women in one of the most difficult times in their lives. The decision to have an abortion at the Abortion Cl+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Kürzlich hochgeladen (20)
2024: Domino Containers - The Next Step. News from the Domino Container commu...

2024: Domino Containers - The Next Step. News from the Domino Container commu...
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...

Mastering MySQL Database Architecture: Deep Dive into MySQL Shell and MySQL R...
Apidays Singapore 2024 - Scalable LLM APIs for AI and Generative AI Applicati...

Apidays Singapore 2024 - Scalable LLM APIs for AI and Generative AI Applicati...
A Beginners Guide to Building a RAG App Using Open Source Milvus

A Beginners Guide to Building a RAG App Using Open Source Milvus
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery

TrustArc Webinar - Unlock the Power of AI-Driven Data Discovery
Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...

Emergent Methods: Multi-lingual narrative tracking in the news - real-time ex...
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...

Apidays New York 2024 - The Good, the Bad and the Governed by David O'Neill, ...
How to Troubleshoot Apps for the Modern Connected Worker

How to Troubleshoot Apps for the Modern Connected Worker
Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...

Web Form Automation for Bonterra Impact Management (fka Social Solutions Apri...
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
Q3 2013 Global DDoS Attacks | DDoS Attack Statistics
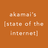
- 1. Q3 2013 Global DDoS Attack Report DDoS perpetrators changed tactics to amplify attack sizes and hide identities Use of the CHARGEN protocol increased 3.37% when compared to other infrastructure attack methods. Adoption of the UDP-based CHARGEN protocol has been rapid as it is widely available on the DDoS-as-a-Service market. Application attacks declined slightly to 23.48%, down from 25.29% in Q2 2013. Compared to Q3 2012, application attacks have increased by almost 6% (from 17% to 23%). SSL POST: 0.26% SSL GET: 0.78% PUSH: 0.91% HTTP POST: 3.37% ACK: 1.69% CHARGEN: 3.37% FIN PUSH: 0.39% HEAD: 0.13% N IO DNS: 8.94% ER LAY ICMP: 11.41% Traditional attack methods, such as ICMP floods, dropped this quarter. The movement away from ICMP floods toward reflected amplification attacks is due to a shift in attack offerings among DDoS-as-a-Service stressor services. 23.48% R APP LIC AT HTTP GET: 18.03% 8.9% of infrastructure attacks were based on the DNS attack protocol, a 4% increase compared to Q3 2012 (5%). L AY E 76.52% TU RE UDP Fragment: 14.66% IN F R A U ST R C RESET: 1.94% RIP: 0.13% RP: 0.39% SYN: 18.16% UDP Floods: 14.66% SYN PUSH: 0.13% TCP Fragment: 0.65% The UDP attack vector totaled 29.32% of all attacks – a 10% increase compared to the previous quarter, returning to levels seen in Q2 2012. A significant portion of UDP floods were reflected amplification attacks using DNS and CHARGEN. Infrastructure attacks increased 2% compared to Q2 2013. Compared to Q3 2012, infrastructure attacks fell by almost 6% (81.40 to 76.52&) THE BOTTOM LINE: At 18.16%, the percentage of SYN floods has decreased this quarter compared to Q2 2013 and Q3 2012, but SYN floods still remain the most popular of all infrastructure attacks, most likely due to the proliferation of easy-to-use stress-testing tools that are freely available. There was a significant shift to reflection-based attack vectors in Q3 2013, rising 69% compared to the previous quarter, and 265% when compared to the same quarter a year ago. www.prolexic.com