Report
Share
Download to read offline
Recommended
JEL 2012 - Thierry Merlin - "Les mondes virtuel à L'Université Lyon3"

JEL 2012 - Thierry Merlin - "Les mondes virtuel à L'Université Lyon3"PAPN (Pôle d'Accompagnement à la Pédagogie Numérique)
Livre blanc mobile-learning by IL&DI http://il-di.com

Livre blanc mobile-learning by IL&DI http://il-di.comIL-DI - International Learning and Development Institute
E-learning pour la formation des formateurs. De la conception à l’implémentat...

E-learning pour la formation des formateurs. De la conception à l’implémentat...eraser Juan José Calderón
Recommended
JEL 2012 - Thierry Merlin - "Les mondes virtuel à L'Université Lyon3"

JEL 2012 - Thierry Merlin - "Les mondes virtuel à L'Université Lyon3"PAPN (Pôle d'Accompagnement à la Pédagogie Numérique)
Livre blanc mobile-learning by IL&DI http://il-di.com

Livre blanc mobile-learning by IL&DI http://il-di.comIL-DI - International Learning and Development Institute
E-learning pour la formation des formateurs. De la conception à l’implémentat...

E-learning pour la formation des formateurs. De la conception à l’implémentat...eraser Juan José Calderón
State of-the-internet-web-security-threat-advisory-blackshades-rat-presentation

State of-the-internet-web-security-threat-advisory-blackshades-rat-presentationState of the Internet
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
More Related Content
More from State of the Internet
State of-the-internet-web-security-threat-advisory-blackshades-rat-presentation

State of-the-internet-web-security-threat-advisory-blackshades-rat-presentationState of the Internet
More from State of the Internet (8)
State of-the-internet-web-security-threat-advisory-blackshades-rat-presentation

State of-the-internet-web-security-threat-advisory-blackshades-rat-presentation
Q3 2013 Global DDoS Attacks | DDoS Attack Statistics

Q3 2013 Global DDoS Attacks | DDoS Attack Statistics
Recently uploaded
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...?#DUbAI#??##{{(☎️+971_581248768%)**%*]'#abortion pills for sale in dubai@
Recently uploaded (20)
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...

Navigating the Deluge_ Dubai Floods and the Resilience of Dubai International...
Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood

Polkadot JAM Slides - Token2049 - By Dr. Gavin Wood
Mcleodganj Call Girls 🥰 8617370543 Service Offer VIP Hot Model

Mcleodganj Call Girls 🥰 8617370543 Service Offer VIP Hot Model
Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...

Apidays New York 2024 - APIs in 2030: The Risk of Technological Sleepwalk by ...
EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER

EMPOWERMENT TECHNOLOGY GRADE 11 QUARTER 2 REVIEWER
AWS Community Day CPH - Three problems of Terraform

AWS Community Day CPH - Three problems of Terraform
+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...

+971581248768>> SAFE AND ORIGINAL ABORTION PILLS FOR SALE IN DUBAI AND ABUDHA...
Why Teams call analytics are critical to your entire business

Why Teams call analytics are critical to your entire business
Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...

Apidays New York 2024 - Passkeys: Developing APIs to enable passwordless auth...
ICT role in 21st century education and its challenges

ICT role in 21st century education and its challenges
Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME

Cloud Frontiers: A Deep Dive into Serverless Spatial Data and FME
Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe

Apidays New York 2024 - Scaling API-first by Ian Reasor and Radu Cotescu, Adobe
Connector Corner: Accelerate revenue generation using UiPath API-centric busi...

Connector Corner: Accelerate revenue generation using UiPath API-centric busi...
Strategies for Landing an Oracle DBA Job as a Fresher

Strategies for Landing an Oracle DBA Job as a Fresher
Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...

Apidays New York 2024 - Accelerating FinTech Innovation by Vasa Krishnan, Fin...
Fingerprinting a DDoS Attack
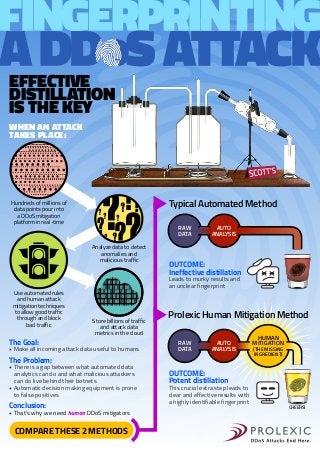
- 1. EFFECTIVE DISTILLATION IS THE KEY WHEN AN ATTACK TAKES PLACE: Hundreds of millions of data points pour into a DDoS mitigation platform in real-time ?? ??? ? ?? ? ? ? ? Analyze data to detect anomalies and malicious traffic Use automated rules and human attack mitigation techniques to allow good traffic through and block bad traffic The Goal: 101101010001010100011 010100110101001110011 101010011010101001100 101010100110010100101 101010010101010100101 010100101010011100010 101010100101001110101 Store billions of traffic and attack data metrics in the cloud • Make all incoming attack data useful to humans Typical Automated Method RAW DATA AUTO ANALYSIS OUTCOME: Ineffective distillation Leads to murky results and an unclear fingerprint Prolexic Human Mitigation Method RAW DATA AUTO ANALYSIS The Problem: • There is a gap between what automated data analytics can do and what malicious attackers can do live behind their botnets • Automatic decision making equipment is prone to false positives Conclusion: • That’s why we need human DDoS mitigators COMPARE THESE 2 METHODS HUMAN MITIGATION (THE MISSING INGREDIENT) OUTCOME: Potent distillation This crucial extra step leads to clear and effective results with a highly identifiable fingerprint CHEERS!