Configure, Monitor and Troubleshoot SIP
- 1. SIP (Session Initiation Protocol) Configuring - Monitoring - Troubleshooting Study Notes +W - Technology Skills For Women Series1 http://SlideShare.net/OxfordCambridge 1 Men are allowed to read too, if they wish, as the language style and the document format are universal.
- 2. Study Notes http://SlideShare.net/OxfordCambridge 2 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Table of Contents About “+W - Technology Skills For Women” series ................................................................................ 4 Course Objectives.................................................................................................................................... 6 References............................................................................................................................................... 7 A. Introducing SIP......................................................................................................................................... 8 1. SIP and associated standards .............................................................................................................. 8 Question ................................................................................................................................................ 12 Question ................................................................................................................................................ 12 B. 2. SIP components................................................................................................................................. 12 Question ................................................................................................................................................ 15 Question ................................................................................................................................................ 16 Summary................................................................................................................................................ 16 C. SIP Messages and Addressing................................................................................................................ 18 1. SIP messages...................................................................................................................................... 18 Question ................................................................................................................................................ 22 Question ................................................................................................................................................ 22 2. SIP addressing.................................................................................................................................... 23 Question ................................................................................................................................................ 26 Question ................................................................................................................................................ 26 Summary................................................................................................................................................ 26 D. SIP Call Setup Models and Fault Tolerance ........................................................................................... 28 1. Call setup models............................................................................................................................... 28 Note....................................................................................................................................................... 30 Question ................................................................................................................................................ 34 Question ................................................................................................................................................ 34 2. Robust SIP design............................................................................................................................... 35 Question ................................................................................................................................................ 36 Question ................................................................................................................................................ 37 3. Cisco implementation of SIP.............................................................................................................. 37 Summary................................................................................................................................................ 38 E. Configuring and Monitoring SIP ............................................................................................................ 39 1. Configuring SIP on a Cisco router ...................................................................................................... 39 Question ................................................................................................................................................ 41
- 3. Study Notes http://SlideShare.net/OxfordCambridge 3 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) 2. Monitoring and troubleshooting SIP ................................................................................................. 42 Question ................................................................................................................................................ 44 Question ................................................................................................................................................ 45 Question ................................................................................................................................................ 45 Summary................................................................................................................................................ 45 F. Words and Definitions........................................................................................................................... 47 G. Answers to Quizzes................................................................................................................................ 83
- 4. Study Notes http://SlideShare.net/OxfordCambridge 4 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) About “+W - Technology Skills For Women” series Study Notes in the field of technology will be put together under this category for the following reasons: to encourage ladies, who wish to do so, to stand up and look over the fence into technology related topics; with apprehension or fear; and perhaps consider embracing a career move into this technological path; or simply as to broaden their general knowledge; after all ICT is in most aspects of everyday life; no matter the decision, their skills, professional strengths, and contribution can only be something positive for technical and technological fields.
- 5. Study Notes http://SlideShare.net/OxfordCambridge 5 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) SIP: Session Initiation Protocol A. Introducing SIP B. SIP Messages and Addressing C. SIP Call Setup Models and Fault Tolerance D. Configuring and Monitoring SIP
- 6. Study Notes http://SlideShare.net/OxfordCambridge 6 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Course Objectives Topic When you have completed this topic, you should be able to Checked? Yes/No Introducing SIP recognize the functionality of SIP, and identify the types of user agents and servers used by SIP. SIP Messages and Addressing distinguish between the types, use, and structure of SIP messages, identify SIP address formats, and recognize how SIP addresses are registered and resolved. SIP Call Setup Models and Fault Tolerance distinguish between SIP interworking models for call setup, recognize strategies for maintaining VoIP service, and identify SIP components supported by Cisco. Configuring and Monitoring SIP identify the configuration commands used to implement SIP call setup models, and the commands used to provide support for monitoring and troubleshooting SIP.
- 7. Study Notes http://SlideShare.net/OxfordCambridge 7 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) References SIP - An Introduction (PDF) 2011-01-11? James Wright. Konnetic Integrating Voice and Data Networks 2000, Scott Keagy, Cisco Press, 1578701961 Troubleshooting Cisco IP Telephony 2002, Paul Giralt, Addis Hallmark, Anne Smith, Cisco Press, 1587050757 Voice over IP First-Step 2005, Kevin Wallace, Cisco Press, 1587201569 http://en.wikipedia.org/wiki/Media_Gateway_Control_Protocol 3 September 2013 http://en.wikipedia.org/wiki/Session_Initiation_Protocol 5 March 2014
- 8. Study Notes http://SlideShare.net/OxfordCambridge 8 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) A. Introducing SIP After completing this topic, you should be able to recognize the functionality of SIP, and identify the types of user agents and servers used by SIP. 1. SIP and associated standards 2. SIP components Summary 1. SIP and associated standards Session Initiation Protocol (SIP) provides a framework for establishing and maintaining Voice over IP (VoIP) calls. SIP is a signaling and control protocol for the establishment, maintenance, and termination of multimedia sessions with one or more participants. SIP multimedia sessions include Internet telephone calls, multimedia conferences, and multimedia distribution. Session communications may be based on multicast, unicast, or both. SIP operates on the principle of session invitations. Through invitations, SIP initiates sessions or invites participants into established sessions. Descriptions of these sessions are advertised by any one of several means, including the Session Announcement Protocol (SAP) defined in RFC 2974, which incorporates a session description according to the Session Description Protocol (SDP) defined in RFC 2327.
- 9. Study Notes http://SlideShare.net/OxfordCambridge 9 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) SIP uses other Internet Engineering Task Force (IETF) protocols to define other aspects of VoIP and multimedia sessions; for example, URLs for addressing, Domain Name System (DNS) for service location, and Telephony Routing over IP (TRIP) for call routing. SIP supports personal mobility and other Intelligent Network (IN) telephony subscriber services through name mapping and redirection services. Personal mobility allows a potential participant in a session to be identified by a unique personal number or name. IN provides carriers with the ability to rapidly deploy new user services on platforms that are external to the switching fabric. Access to the external platforms is by way of an independent vendor and standard user interface. Calling-card services, toll-free number services, and local number portability are just three of these services. Multimedia sessions are established and terminated by these services: user location services user capabilities services user availability services call setup services call handling services user location services User location services are employed to locate an end system. user capabilities services User capabilities services are used to select the media type and parameters for multimedia sessions. user availability services User availability services are employed to determine the availability and desire for a party to participate in a session. call setup services
- 10. Study Notes http://SlideShare.net/OxfordCambridge 10 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Call setup services are used to establish a session relationship between parties and to manage call progress. call handling services Call handling services are used to transfer and terminate calls. Although the IETF has made great progress in defining extensions that allow SIP to work with legacy voice networks, the primary motivation behind the protocol is to create an environment that supports next- generation communication models that use the Internet and Internet applications. SIP is described in IETF RFC 3261 (published in June 2002), which renders RFC 2543 (published in March 1999) obsolete. The Cisco SIP-enabled product portfolio encompasses all components of a SIP network infrastructure, from IP Phones and access devices to call control and public switched telephone network (PSTN) interworking. The first Cisco SIP products were deployed with live traffic several years ago. All of these Cisco SIP products are deployed in live networks spanning a variety of applications and continents. The first four products are Cisco IP Phones Cisco Analog Telephone Adaptor (Cisco ATA 186) Cisco packet voice gateways Cisco SIP Proxy Server Cisco IP Phones The Cisco IP Phone series, including the Cisco IP Phone 7970, Cisco IP Phone 7960 and Cisco IP Phone 7940, support SIP user agent (UA) functionality. These IP Phones deliver functionality such as inline power support and dual Ethernet ports, and deliver traditional desktop functionality such as call hold, transfer, conferencing, caller ID, call waiting, and a lighted message waiting indicator. Cisco Analog Telephone Adaptor (Cisco ATA 186)
- 11. Study Notes http://SlideShare.net/OxfordCambridge 11 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) The Cisco ATA 186 supports SIP UA functionality. With two Foreign Exchange Station (FXS) ports and a single Ethernet port, the ATA 186 provides a low-cost means to connect analog phones to a SIP network. The ATA 186 also delivers traditional desktop functionality such as call hold, transfer, conferencing, caller ID, and lighted call-waiting and message waiting indicators. Cisco packet voice gateways The Cisco Series 1700 Modular Access Routers that are voice-capable, Cisco 2600 Series multiservice platforms, Cisco 3800 Series Integrated Services Routers, 3700 Series Integrated Services Routers, Cisco AS5000 Series Universal Gateways, and Cisco 7200 Series voice gateways all support SIP UA functionality. These products provide a means of connecting SIP networks to traditional time-division multiplexing (TDM) networks via T1, E1, digital service level 3 (DS3), channel associated signaling (CAS), PRI or BRI, R2 signaling, FXS, Foreign Exchange Office (FXO), or ear and mouth (E&M) interfaces. Cisco packet voice gateways are used to build the largest packet telephony networks in the world. Cisco SIP Proxy Server The Cisco SIP Proxy Server provides the functionality of a SIP proxy, SIP redirect, SIP registrar, and SIP location services server. The Cisco SIP Proxy Server provides the foundation for call routing within SIP networks; it can interwork with traditional SIP location services, such as DNS or telephone number mapping (E.164 number [ENUM]), with feature servers via a SIP redirect message, and with H.323 location services using standard location request (LRQ) messages. The Cisco SIP Proxy Server runs on either Solaris or Linux operating systems. The last three Cisco SIP products deployed in live networks spanning a variety of applications and continents are Cisco BTS 10200 Softswitch Cisco PGW 2200 PSTN Gateway Cisco PIX Security Appliance and Cisco Adaptive Security Appliance (ASA) Cisco BTS 10200 Softswitch The Cisco BTS 10200 Softswitch provides softswitch functionality to Class 4 and Class 5 networks, and provides SIP-to-Signaling System 7 (SS7) gateway functionality for American National Standards Institute (ANSI) standardized networks. The BTS 10200 Softswitch supports SIP UA functionality in conjunction with a Cisco packet voice media gateway, such as a Cisco AS5000 Series Universal Gateway or a Cisco MGX 8000 Series Voice Gateway. Cisco PGW 2200 PSTN Gateway The Cisco PGW 2200 PSTN Gateway provides softswitch functionality for Class 4 networks, as well as Internet offload and SIP-to-SS7 gateway functionality for international networks. The PGW 2200 PSTN Gateway supports ISDN User Part (ISUP) certification in over 130 countries. The PGW 2200 PSTN Gateway supports SIP UA functionality in conjunction with a Cisco packet voice media gateway such as an AS5000 Series Universal Gateway or MGX 8000 Series Voice Gateway. Cisco PIX Security Appliance and Cisco Adaptive Security Appliance (ASA)
- 12. Study Notes http://SlideShare.net/OxfordCambridge 12 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) The Cisco PIX Security Appliance and the Cisco ASA are SIP-aware networking devices that provide firewall and Network Address Translation (NAT) functionality. Because these devices are SIP-aware, they are able to dynamically allow SIP signaling to traverse network and addressing boundaries without compromising overall network security. When functioning in this capacity, the Cisco PIX Security Appliance and the Cisco ASA are called application layer gateways (ALGs). Questioni Identify the Internet Engineering Task Force (IETF) protocol used by SIP for call routing. Options: 1. Border Gateway Protocol (BGP) 2. Open Shortest Path First (OSPF) 3. Routing Information Protocol (RIP) 4. Telephony Routing over IP (TRIP) Questionii Identify the SIP services that select the media type and parameters. Options: 1. Call handling services 2. Call setup services 3. User availability services 4. User capabilities services 5. User location services B. 2. SIP components SIP is a peer-to-peer protocol. The peers in a session are called User Agents (UAs). SIP is modeled on the interworking of UAs and network servers. A UA consists of two functional components:
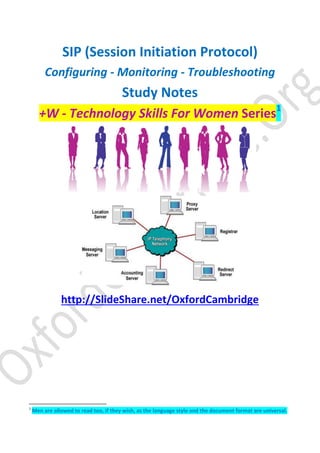
- 13. Study Notes http://SlideShare.net/OxfordCambridge 13 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) user agent client (UAC) user agent server (UAS) user agent client (UAC) A UAC is a client application that initiates a SIP request. user agent server (UAS) A UAS is a server application that contacts the user when a SIP invitation is received and then returns a response on behalf of the user to the invitation originator. Typically, a SIP UA can function as a UAC or a UAS during a session, but not both in the same session. Whether the endpoint functions as a UAC or a UAS depends on the UA that initiated the request; the initiating UA uses a UAC and the terminating UA uses a UAS. From an architectural standpoint, the physical components of a SIP network are grouped into two categories: UAs and SIP servers. SIP UAs include these devices: IP telephone gateway IP telephone An IP telephone acts as a UAS or UAC on a session-by-session basis. Software telephones and Cisco SIP IP Phones initiate SIP requests and respond to requests. gateway A gateway acts as a UAS or UAC and provides call control support. Gateways provide many services, the most common being a translation function between SIP UAs and other terminal types. This function includes translation between transmission formats and between communications procedures. A gateway translates
- 14. Study Notes http://SlideShare.net/OxfordCambridge 14 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) between audio and video signals and performs call setup and clearing on both the IP side and the switched circuit network (SCN) side. SIP servers include these types: proxy server redirect server registrar server location server proxy server A proxy server is an intermediate component that receives SIP requests from a client, then forwards the requests on behalf of the client to the next SIP server in the network. The next server can be another proxy server or a UAS. Proxy servers can provide functions such as authentication, authorization, network access control, routing, reliable request transmissions, and security. redirect server A redirect server provides a UA with information about the next server that the UA should contact. The server can be another network server or a UA. The UA redirects the invitation to the server identified by the redirect server. registrar server A registrar server makes requests from UACs for registration of their current location. Registrar servers are often located near or even colocated with other network servers, most often a location server. location server A location server is an abstraction of a service providing address resolution services to SIP proxy or redirect servers. A location server embodies mechanisms to resolve addresses. These mechanisms can include a database of registrations or access to commonly used resolution tools such as Finger protocol, Referral Whois (RWhois), Lightweight Directory Access Protocol (LDAP), or operating system-dependent mechanisms. A registrar server can be modeled as one subcomponent of a location server; the registrar server is partly responsible for populating a database associated with the location server. Except for the voice register mode request, communication between SIP components and a location server is not standardized. Leaders in the communications industry are constantly developing new products and services that rely on SIP, and they are offering attractive new communications services to their customers.
- 15. Study Notes http://SlideShare.net/OxfordCambridge 15 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Microsoft added, in the past, support for SIP clients in core product offerings - a step that proliferates SIP clients on personal computers worldwide. SIP is gaining momentum in every market. Cisco has be enabling the advance of new communications services with a complete SIP-enabled portfolio, including proxy servers, packet voice gateways, call control and signalling, IP Phones, and firewalls. Cisco solutions support a variety of call control and standard protocols, including H.323, Media Gateway Control Protocol (MGCP), and SIP, which can coexist in the same customer network. Questioniii Identify which are SIP server types. Options: 1. Dynamic Host Configuration Protocol (DHCP) 2. Gateway 3. Location 4. Proxy 5. Redirect 6. Registrar
- 16. Study Notes http://SlideShare.net/OxfordCambridge 16 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Questioniv Which SIP server is often collocated with the location server? Options: 1. Gateway 2. Proxy 3. Redirect 4. Registrar Summary SIP is a signaling and control protocol for the establishment, maintenance, and termination of multimedia sessions with one or more participants. Such multimedia sessions are established and terminated by five services: user location, user capabilities, user availability, call setup, and call handling. The Cisco SIP-enabled product portfolio comprises all components of a SIP network infrastructure, from IP Phones and access devices to call control and PSTN interworking. SIP is modelled on the interworking of UAs and network servers. A UA consists of two functional components: the UAC and the UAS. From an architectural viewpoint, the physical components of a SIP network are grouped into two categories: UAs, including IP telephones and gateways, and SIP servers, which include proxy, redirect, registrar, and location servers.
- 17. Study Notes http://SlideShare.net/OxfordCambridge 17 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l )
- 18. Study Notes http://SlideShare.net/OxfordCambridge 18 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) C. SIP Messages and Addressing After completing this topic, you should be able to distinguish between the types, use, and structure of SIP messages, identify SIP address formats, and recognize how SIP addresses are registered and resolved. 1. SIP messages 2. SIP addressing Summary 1. SIP messages Communication between SIP components uses a request and response message model. INVITE sip:bob@biloxi.com SIP/2.0 Via: SIP/2.0/UDP
- 19. Study Notes http://SlideShare.net/OxfordCambridge 19 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) pc33.atlanta.com;branch=z9hG4bk776asdhds Max-Forwards: 70 To: Bob<sip:bob@biloxi.com> From: Alice<sip:alice@atlanta.com>;tag=1928301774 Call-ID: a84b4c76e66170@pc33.atlanta.com CSeq: 314159 INVITE Contac: <sip:alice@pc33.atlanta.com> Content-Type: application/sdp Content-Length: 142 SIP communication involves two messages: request from a client to a server response from a server request from a client to a server A request from a client to a server consists of a request line, header lines, and a message body. response from a server A response from a server to a client consists of a status line, header lines, and a message body. All SIP messages are text-based and modeled on RFC 822, Standard for the Format of ARPA Internet Text Messages, and RFC 2068, Hypertext Transfer Protocol - HTTP/1.1. SIP defines four types of headers: a general header, an entity header, a request header, and a response header. The first two types of headers appear on both message types. The latter two types of headers are specific to request and response, respectively.
- 20. Study Notes http://SlideShare.net/OxfordCambridge 20 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) INVITE sip:bob@biloxi.com SIP/2.0 Via: SIP/2.0/UDP pc33.atlanta.com;branch=z9hG4bk776asdhds Max-Forwards: 70 To: Bob<sip:bob@biloxi.com> From: Alice<sip:alice@atlanta.com>;tag=1928301774 Call-ID: a84b4c76e66170@pc33.atlanta.com CSeq: 314159 INVITE Contac: <sip:alice@pc33.atlanta.com> Content-Type: application/sdp Content-Length: 142 In the request line, SIP uses a message to indicate the action to be taken by the responding component (usually a server). These six request messages indicate the action that the responding component should take: INVITE acknowledgment (ACK) BYE CANCEL OPTIONS REGISTER INVITE
- 21. Study Notes http://SlideShare.net/OxfordCambridge 21 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) The INVITE message is originated by a client to indicate that the server is invited to participate in a session. An invitation includes a description of the session parameters. acknowledgment (ACK) The ACK message is originated by a client to indicate that the client has received a response to its earlier invitation. BYE The BYE message is originated by a client or server to initiate call termination. CANCEL The CANCEL message is originated by a client or server to interrupt any request currently in progress. CANCEL is not used to terminate active sessions. OPTIONS The OPTIONS message is used by a client to solicit capabilities information from a server. This method is used to confirm cached information about a UA or to check the ability of a UA to message accept an incoming call. REGISTER The REGISTER message is used by a UA to provide information to a network server. Registrations have a finite life and must be renewed periodically. This prevents the use of stale information when a UA moves. SIP response messages are sent in response to a request and indicate the outcome of request interpretation and execution. Responses take one of three basic positions: success, failure, or provisional. A status code reflects the outcome of the request. There are six response messages to indicate the status of a request. 1xx (informational) 2xx (successful) 3xx (redirection) 4xx (client error) 5xx (server error) 6xx (global failure)
- 22. Study Notes http://SlideShare.net/OxfordCambridge 22 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) 1xx (informational) The 1xx (informational) status code is a provisional response indicating that the request is still being processed. 2xx (successful) The 2xx (successful) status code indicates that the requested action is complete and successful. 3xx (redirection) The 3xx (redirection) status code indicates that the requestor requires further action; for example, when a redirect server responds with "moved" to advise the client to redirect its invitation. 4xx (client error) The 4xx (client error) status code is a fatal response indicating that the client request is flawed or impossible to complete. 5xx (server error) The 5xx (server error) status code is a fatal response indicating that the request is valid but the server failed to complete it. 6xx (global failure) The 6xx (global failure) status code is a fatal response indicating that the request cannot be fulfilled by any server. Questionv Identify the SIP message that is used to provide information to a network server. Options: 1. ACK 2. INVITE 3. OPTIONS 4. REGISTER Questionvi Identify the SIP response message that is provisional.
- 23. Study Notes http://SlideShare.net/OxfordCambridge 23 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Options: 1. 1xx (informational) 2. 2xx (successful) 3. 3xx (redirection) 4. 4xx (client error) 5. 5xx (server error) 6. 6xx (global failure) 2. SIP addressing To obtain the IP address of a SIP UAS or a network server, a UAC performs address resolution of a user identifier.
- 24. Study Notes http://SlideShare.net/OxfordCambridge 24 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Fully qualified domain names sip:jdoe@cisco.com E.164 addresses sip:14805551234@gateway.com: user=phone Mixed addresses sip:14805551234: password=changeme@10.1.1.1 sip:jdoe@10.1.1.1 An address in SIP is defined in the syntax for a URL with "sip:" or "sips:" (for secure SIP connections) as the URL type. SIP URLs are used in SIP messages to identify the originator, the current destination, the final recipient, and any contact party. When two UAs communicate directly with each other, the current destination and final recipient URLs are the same. However, the current destination and the final recipient are different if a proxy or redirect server is used. An address consists of an optional user ID, a host description, and optional parameters to qualify the address more precisely. The host description may be a domain name or an IP address. A password is associated with the user ID, and a port number is associated with the host description. This example shows instances of SIP addresses. In the example, "sip:14085551234@gateway.com; user=phone", the "user=phone" parameter is required to indicate that the user part of the address is a telephone number. Without the "user=phone" parameter, the user ID is taken literally as a numeric string. The "14085559876" in the URL "sip:14085559876@10.1.1.1" is an example of a numeric user ID. In the same example, the password "changem" is defined for the user.
- 25. Study Notes http://SlideShare.net/OxfordCambridge 25 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) A SIP address is acquired in several ways: by interacting with a user, by caching information from an earlier session, or by interacting with a network server. For a network server to assist, it must recognize the endpoints in the network. This knowledge is abstracted to reside in a location server and is dynamically acquired by its registrar server. To contribute to this dynamic knowledge, an endpoint registers its user addresses with a registrar server. This example shows a voice REGISTER mode request to a registrar server. To resolve an address, a UA uses a variety of internal mechanisms such as a local host table, DNS lookup, Finger protocol, rwhois, or LDAP, or it leaves that responsibility to a network server. A network server uses any of the tools available to a UA or interacts through a nonstandard interface with a location server. This example shows a SIP proxy server resolving the address by using the services of a location server.
- 26. Study Notes http://SlideShare.net/OxfordCambridge 26 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Questionvii Identify the ways in which a SIP UA can resolve an address. Options: 1. Dynamic Host Configuration Protocol(DHCP) 2. It lets the network server resolve it 3. It relies on WINS 4. It uses a local host table 5. It uses rwhois Questionviii Identify the type of SIP address that is represented by: "sip:12486593178@gateway.com;user=phone". Options: 1. An E.164 address 2. A fully qualified domain name 3. A mixed address Summary SIP employs a request/response messaging model for communication. All SIP messages are text-based and modeled on the HTTP syntax. SIP uses six response codes to indicate the status of a request: 1xx (informational), 2xx (successful), 3xx (redirection), 4xx (client error), 5xx (server error), and 6xx (global failure).
- 27. Study Notes http://SlideShare.net/OxfordCambridge 27 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) SIP addresses use the format and structure of a URL. Network components such as location and registrar servers record addresses and carry out address resolution.
- 28. Study Notes http://SlideShare.net/OxfordCambridge 28 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) D. SIP Call Setup Models and Fault Tolerance After completing this topic, you should be able to distinguish between SIP interworking models for call setup, recognize strategies for maintaining VoIP service, and identify SIP components supported by Cisco. 1. Call setup models 2. Robust SIP design 3. Cisco implementation of SIP Summary 1. Call setup models If a UAC recognizes the destination UAS, the client communicates directly with the server. In situations in which the client is unable to establish a direct relationship, the client solicits the assistance of a network server. There are three interworking models for call setup: direct, using a proxy server, and using a redirect server. When a UA recognizes the address of a terminating endpoint from cached information, or has the capacity to resolve it by some internal mechanism, the UAC may initiate direct (UAC-to-UAS) call setup procedures. Direct setup is the fastest and most efficient of the call setup procedures. However, direct setup has some disadvantages. It relies on cached information or internal mechanisms to resolve addresses, which can become outdated if the destination is mobile. In addition, if the UA must keep information on a large number of destinations, management of the data can become prohibitive. This makes the direct method nonscalable.
- 29. Study Notes http://SlideShare.net/OxfordCambridge 29 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Direct call setup is a three-step process: step 1 step 2 step 3 step 1 In step 1, the originating UAC sends an invitation (INVITE) to the UAS of the recipient. The message includes an endpoint description of the UAC and SDP. step 2 In step 2, if the UAS of the recipient determines that the call parameters are acceptable, it responds positively to the originator UAC. step 3 In step 3, the originating UAC issues an ACK. After the final step of the direct call setup process, the UAC and UAS have all the information that is required to establish Real-Time Transport Protocol (RTP) sessions between them. The proxy server procedure is transparent to a UA. The proxy server intercepts and forwards an invitation to the destination UA on behalf of the originator.
- 30. Study Notes http://SlideShare.net/OxfordCambridge 30 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) A proxy server responds to the issues of the direct method by centralizing control and management of call setup and providing a more dynamic and up-to-date address resolution capability. The benefit to the UA is that it does not need to learn the coordinates of the destination UA, yet can still communicate with the destination UA. The disadvantages of this method are that using a proxy server requires more messaging and creates a dependency on the proxy server. If the proxy server fails, the UA is incapable of establishing its own sessions. Note Although the proxy server acts on behalf of a UA for call setup, the UAs establish RTP sessions directly with each other. When a proxy server is used, call setup involves a seven-step procedure. These are the first four steps of the procedure. step 1 step 2 step 3 step 4
- 31. Study Notes http://SlideShare.net/OxfordCambridge 31 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) step 1 In step 1, the originating UAC sends an invitation (INVITE) to the proxy server. step 2 In step 2, the proxy server, if required, consults the location server to determine the path to the recipient and its IP address. step 3 In step 3, the proxy server sends the INVITE to the UAS of the recipient. step 4 In step 4, if the UAS of the recipient determines that the call parameters are acceptable, it responds positively to the proxy server. These are the last three steps of the call setup procedure for the proxy server method. step 5 step 6 step 7 step 5 In step 5, the proxy server responds to the originating UAC. step 6 In step 6, the originating UAC issues an ACK. step 7
- 32. Study Notes http://SlideShare.net/OxfordCambridge 32 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) In step 7, the proxy server forwards the ACK to the recipient UAS. After the final step of the proxy server call setup procedure, the UAC and UAS have all the information required to establish RTP sessions. A redirect server is programmed to discover a path to the destination. Instead of forwarding the INVITE to the destination, the redirect server reports back to a UA with the destination coordinates that the UA should try next. A redirect server offers many of the advantages of the proxy server. However, the number of messages involved in redirection is fewer than with the proxy server procedure. The UA has a heavier workload because it must initiate the subsequent invitation. When a redirect server is used, call setup involves a seven-step procedure. These are the first four steps of this process. step 1 step 2 step 3 step 4 step 1 In step 1, the originating UAC sends an invitation (INVITE) to the redirect server. step 2
- 33. Study Notes http://SlideShare.net/OxfordCambridge 33 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) In step 2, the redirect server, if required, consults the location server to determine the path to the recipient and its IP address. step 3 In step 3, the redirect server returns a "moved" response to the originating UAC with the IP address obtained from the location server. step 4 In step 4, the originating UAC acknowledges the redirection. These are the last three steps of the call setup procedure for the redirect server method. step 5 step 6 step 7 step 5 In step 5, the originating UAC sends an INVITE to the remote UAS. step 6 In step 6, if the UAS of the recipient determines that the call parameters are acceptable, it responds positively to the UAC. step 7 In step 7, the originating UAC issues an ACK. After the final step of the redirect server call setup procedure, the UAC and UAS have all the information that is required to establish RTP sessions between them.
- 34. Study Notes http://SlideShare.net/OxfordCambridge 34 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Questionix Identify the disadvantage of using the direct call setup method. Options: 1. It has to learn the coordinates of the destination UA 2. It needs the assistance of a network server 3. It relies on cached information that may be out of date 4. It uses more bandwidth Questionx Which of these describes call setup using a proxy server? Options: 1. If the proxy server fails, the UA cannot establish its own sessions 2. If the proxy server fails, the UA uses RTP to establish its sessions 3. The proxy server sends fewer redirection messages than a redirect server 4. The UAs establish RTP sessions through the proxy server
- 35. Study Notes http://SlideShare.net/OxfordCambridge 35 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) 2. Robust SIP design Maintaining high availability of a SIP environment requires a design that accommodates the failure of a network server. There are two strategies for maintaining VoIP service in such situations. In a SIP environment, the failure of a network server cripples UAs that are dependent on that server. In SIP, the network servers are the proxy server, the redirect server, and the location server. The most obvious way to preserve access to the critical components is to implement multiple instances of access. For replication of a proxy or redirect server to be effective, a UA must have the ability to locate an active server dynamically. You can achieve this using either of these methods: method 1 method 2
- 36. Study Notes http://SlideShare.net/OxfordCambridge 36 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) method 1 In method 1, you must preconfigure a UA with the address of at least two of the servers. If access to its first choice fails, it shifts to the second. method 2 In method 2, if all servers are configured with the same name, you must configure a UA to look up the name using DNS. The DNS query returns the addresses of all the servers matching the name, and the UA proceeds down the list until it finds one that works. In this example, SIP servers have been replicated to ensure survival of the SIP environment in the event of the failure of a network server. Questionxi Identify the SIP components that need to be replicated in order to provide fault tolerance. Options: 1. Gateway server 2. Location server 3. Proxy server 4. Redirect server 5. Registrar server
- 37. Study Notes http://SlideShare.net/OxfordCambridge 37 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Questionxii Identify the method that can be used to replicate a proxy server. Options: 1. Configuring a redirect server to act as a proxy server 2. Configuring two location servers on the network 3. Configuring two replication servers on the network 4. Enabling the UA to dynamically locate an active server 3. Cisco implementation of SIP Cisco implements SIP by providing support for SIP components. Therefore, Cisco provides support for these three SIP components: SIP UAs network servers other support SIP UAs Cisco provides support for SIP UAs in Cisco IP Phone. Cisco implements SIP UA (gateway) support in four devices: Cisco voice-enabled routers (first available in Cisco IOS Release 12.1), Cisco PGW 2200 PSTN Gateways, Voice- enabled Cisco AS5xx0 universal access servers, and Cisco BTS 10200 Softswitch. network servers
- 38. Study Notes http://SlideShare.net/OxfordCambridge 38 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Cisco implements SIP proxy and redirect server support in the Cisco SIP Proxy Server. The server is an application designed for a Red Hat Linux 7.3 or Solaris 8 operating environment. other support Other support refers to Cisco PIX Security Appliance and Cisco ASA monitoring the SIP handshaking to dynamically open conduits for the RTP sessions. Summary Although call setup between UAs is possible, a proxy or redirect server may be employed for scalability or to simplify UA configuration. Maintaining high availability of a SIP environment requires a design that accommodates the failure of a network server. Using multiple SIP proxy or redirect servers enhances survivability in such a situation. Cisco supports standalone and gateway clients. The Cisco SIP Proxy Server supports SIP proxy or redirect services.
- 39. Study Notes http://SlideShare.net/OxfordCambridge 39 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) E. Configuring and Monitoring SIP After completing this topic, you should be able to identify the configuration commands used to implement SIP call setup models, and the commands used to provide support for monitoring and troubleshooting SIP. 1. Configuring SIP on a Cisco router 2. Monitoring and troubleshooting SIP Summary 1. Configuring SIP on a Cisco router A SIPA SIP configuration consists of two parts: the SIP UA and the VoIP dial peers that select SIP as the session protocol. You need to use configuration commands to implement SIP call setup models.
- 40. Study Notes http://SlideShare.net/OxfordCambridge 40 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) The SIP UA is one part of the SIP configuration. This example displays a sample SIP UA configuration. The UA is enabled with the sip-ua command. Subcommands are optional. This example shows how you can change the value of four retry counters. The configuration also specifies the name of a SIP proxy or redirect server. ! sip-ua retry invite 2 retry response 2 retry bye 2 retry cancel 2 sip-server dns:server ! SIP is selected as the call control protocol from inside a dial peer. SIP is requested by the session protocol sipv2 dial-peer subcommand. This example displays two dial-peer variations.
- 41. Study Notes http://SlideShare.net/OxfordCambridge 41 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) ! dial-peer voice 444 voip destination-pattern 2339000 session protocol sipv2 session target ipv4:172.18.192.205 ! dial-peer voice 111 voip destination-pattern 111 session protocol sipv2 session target sip-server ! In this example, both dial peers include the session protocol sipv2 subcommand, and SIP is used when the destination pattern matches either dial peer. The session target distinguishes one session from the other. dial-peer 444 dial-peer 111 dial-peer 444 In dial-peer 444, the IP address of the server is provided as the session target. The address can be the address of a UA, proxy server, or redirect server. dial-peer 111 In dial-peer 111, the session target is the sip-server parameter. When the sip-server parameter is the target, the IP address of the actual server is taken from the sip-server subcommand in the SIP UA configuration. This means that from global configuration mode, the network administrator has entered the sip-ua command and the sip-server dns:server subcommand. The address represents the location of a proxy server or redirect server. In this example, the name of the SIP server is "server". Questionxiii Identify the show command that displays SIP UA response and retry information. Options:
- 42. Study Notes http://SlideShare.net/OxfordCambridge 42 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) 1. show call active voice 2. show sip-ua retry 3. show sip-ua statistics 4. show sip-ua status 2. Monitoring and troubleshooting SIP You can use the show and debug commands to provide support for monitoring and troubleshooting SIP. There are six show commands that are valuable when examining the status of SIP components and troubleshooting: show call active voice [brief] show call history voice [last n | record | brief] show sip-ua retry show sip-ua statistics show sip-ua status show sip-ua timers
- 43. Study Notes http://SlideShare.net/OxfordCambridge 43 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) show call active voice [brief] The show call active voice [brief] command displays the status, statistics, and parameters for all active voice calls. show call history voice [last n | record | brief] The show call history voice [last n | record | brief] command displays call records from the history buffer. show sip-ua retry The show sip-ua retry command displays the SIP protocol retry counts. High counts should be investigated. show sip-ua statistics The show sip-ua statistics command displays the SIP UA response, traffic, and retry statistics. show sip-ua status The show sip-ua status command displays the SIP UA listener status, which should be enabled. show sip-ua timers The show sip-ua timers command displays the current value of the SIP UA timers (shown in the figure). There are seven debug commands that are valuable when examining the status of SIP components and troubleshooting. Here are the first four commands: debug voip ccapi inout debug ccsip all debug ccsip calls debug ccsip errors debug voip ccapi inout The debug voip ccapi inout command shows every interaction with the call control application programming interface (API) on both the telephone interface and on the VoIP side. By monitoring the output, you can follow the progress of a call from the inbound interface or VoIP peer to the outbound side of the call. This debug command is very active, so you must use it sparingly in a live network. debug ccsip all
- 44. Study Notes http://SlideShare.net/OxfordCambridge 44 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) The debug ccsip all command enables all ccsip-type debugging. This debug command is very active, so you must use it sparingly in a live network. debug ccsip calls The debug ccsip calls command displays all SIP call details as they are updated in the SIP call control block. You must use this debug command to monitor call records for suspicious clearing causes. debug ccsip errors The debug ccsip errors command traces all errors encountered by the SIP subsystem. The last three debug commands are displayed. debug ccsip events debug ccsip messages debug ccsip states debug ccsip events The debug ccsip events command traces events, such as call setups, connections, and disconnections. An events version of a debug command is often the best place to start, because detailed debugs provide a great deal of useful information. debug ccsip messages The debug ccsip messages command shows the headers of SIP messages that are exchanged between a client and a server. debug ccsip states The debug ccsip states command displays the SIP states and state changes for sessions within the SIP subsystem. Questionxiv Which debug command would you use to trace call setups, connections, and disconnections? Options: 1. debug ccsip calls 2. debug ccsip events 3. debug ccsip messages 4. debug ccsip states 5. debug voip ccapi inout
- 45. Study Notes http://SlideShare.net/OxfordCambridge 45 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Questionxv Which debug command must you use to monitor call records for suspicious clearing causes? Options: 1. debug ccsip all 2. debug ccsip calls 3. debug ccsip errors 4. debug ccsip states Questionxvi Identify the show command that displays the SIP UA listener status, which should be enabled. Options: 1. show call active voice 2. show sip-ua retry 3. show sip-ua statistics 4. show sip-ua status Summary A SIP configuration comprises two elements: the SIP UA and the VoIP dial peers that select SIP as the session protocol. You enable the SIP UA using the sip-ua command. SIP is selected as the call control protocol from inside a dial peer using the session protocol sipv2 dial-peer subcommand. You can use the six show and seven debug commands to provide support for monitoring and troubleshooting SIP.
- 46. Study Notes http://SlideShare.net/OxfordCambridge 46 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l )
- 47. Study Notes http://SlideShare.net/OxfordCambridge 47 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) F. Words and Definitions AAA Acronym for authentication, authorization, and accounting. Systems implemented to securely determine the identity and privileges of a user and track that user's activities. access class The class of service a customer chooses when subscribing to DS-3 based Switched MultiMegabit Data Services (SMDS). The access class is defined as 4, 10, 16, 25, or 34 Mbps. For users who subscribe to an access class lower than 34 Mbps, a 34 Mbps bandwidth is available for burst transmissions; However, the duration of user bursts is limited so that the average throughput does not exceed the specified access class. See also SMDS. access code A sequence of dialed digits that allows a user to gain access to a facility, service, feature, or function of a network or system. access coordination The design, ordering, installation, testing, and maintenance of local access services. access delay The time interval from the last digit of a dialed number until the call is delivered by the local exchange carrier (LEC) to the appropriate interexchange carrier (IXC). Also known as call setup time. See also IXC. access device The hardware component used in a signaling controller system, access server, or multiplexer. access digit On a PBX, an outside line is normally accessed by dialing an access digit, such as 9. access gateway A gateway that allows the IP PBX to communicate with the PSTN or traditional PBX systems. See also IP, PBX, and PSTN. access layer Part of ISO-OSI layered protocol model. access line A transmission line that provides access to a larger system or network. access link The local access connection between a customer's premises and a carrier's point of presence (POP), which is the carrier's central switching office or closest point of local termination. See also POP. access method The technique for moving data, voice, or video between storage and input/output devices. Also, the technique and/or program code used in local area networks (LANs) to grant selective access to individual stations. access node See AN. access port Connects a network device to an IP device. For example, a computer can be connected to an IP phone through an access port. access protocol A set of specific procedures that enable a user to obtain services from a telephone company or network. access server Communications processor that connects asynchronous devices to a LAN or WAN through network and terminal emulation software. Performs both synchronous and asynchronous routing of supported protocols. Sometimes called a network access server. Access servers for the Cisco signaling controller are the Cisco AS5200, Cisco AS5300, and Cisco AS5800. account code
- 48. Study Notes http://SlideShare.net/OxfordCambridge 48 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) A numeric code that identifies the calling party for internal billing or accounting purposes. Account codes are often used by service companies such as accountants and lawyers to bill specific clients for telephone expenses. Also known as a project code or bill-back code. ACD Acronym for automatic call distributor. A device that handles a large number or incoming calls. An ACD performs four functions: first, it recognizes and answers incoming calls; second, it looks in a database to decide how to route the call; third, based on these instructions, it sends the call to an answering position based on a pre-determined, logical answering pattern. (Or, if all positions are busy, the ACD plays a recorded message and places the call in a queue until an answering position becomes available); finally, the ACD connects the call to an agent, once that agent has completed the previous call. ACL Acronym for access control list. A roster of users and groups of users, along with their access rights. ACP Acronym for automatic call processing. A system in which calls are processed entirely by computer. additional call offering An Integrated Services Digital Network (ISDN) feature that allows multiple calls to be placed simultaneously to the same telephone number. A serving switch is programmed with the number of lines on the receiving telephone equipment. The switch will offer an additional call if there is a line available to accept it. See also ISDN. address In a communications network, the identifying designation of an entity that is physically and/or logically distinct. Also, the destination of a message. Also, in software, any location that can be specifically referred to in a program storage location, terminal, peripheral device, cursor location or any other component. Ad-Hoc conference A Cisco CallManager feature that allows a conference controller to build a conference that has not been previously arranged. In an Ad-Hoc conference, the conference controller individually calls and adds each participant to the conference. Compare to Meet-Me Conference. Administrative Reporting Tool See ART. Administrative VLAN Used in non-Cisco switched networks in conjunction with Cisco IP Phones to indicate the virtual local area network (VLAN) of which the phone is a member. Assigns the phone to an auxiliary VLAN. See also Operational VLAN. ADPCM Acronym for adaptive differential pulse code modulation. A speech coding method that uses fewer bits than the traditional pulse code modulation (PCM). ADU Acronym for automatic dialing unit. A device that automatically generates a predetermined telephone number when a specific button is pressed. AEC Acronym for automatic echo cancellation. agent Individuals or companies that market the services of a carrier, but are not directly employed by the carrier. AIM Advanced Interface Module. The data compression AIM provides hardware-based compression and decompression of packet data transmitted and received on the serial network interfaces of the Cisco 2600 series router without occupying the Port Module Slot that might otherwise be used for additional customer network ports. Designed to plug directly into a header on the Cisco 2600 series router motherboard. a-law
- 49. Study Notes http://SlideShare.net/OxfordCambridge 49 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) ITU-T companding standard used in the conversion between analog and digital signals in pulse code modulation (PCM) systems. In contrast to the North American mu-law, a-law provides a constant signal-to-distortion ratio over a broader dynamic range of analog input signals at the expense of a poorer signal-to-distortion ratio for low-level signals. See also companding and µ-law. ALB Acronym for analog loop back. A method of testing modems in which the telephone line is disconnected and the transmitted signal is looped back to the receiver. alerting The process a switch uses to inform customer premises equipment (CPE) that an incoming call is present and waiting for an answer. For analog lines, alerting consists of applying a ringing voltage; for hybrid telephones, alerting consists of sending signaling bits; and for digital telephones, cellular telephones, or personal communications service (PCS) handsets, it consists of sending a message to the CPE that alerts the user. Alerting of the end user is a function of the CPE (e.g., audible ring, flashing lamp, voice announcement). On some CPE, additional incoming calls for busy lines may be indicated via messages, lamps or call waiting tones. See also CPE and PCS. ambient noise The background noise that is present on a non-digital communications line at all times. AMIS Acronym for Audio Messaging Interchange Specification. A series of standards aimed at addressing the problem of how voice messaging systems produced by different vendors can network or inter-network. Before AMIS, systems from different vendors could not exchange voice messages. AMIS deals only with the interaction between two systems for the purpose of exchanging voice messages. It does not describe the user interface to a voice messaging system, specify how to implement AMIS in a particular system, or limit the features a vendor may implement. See also AMIS-A. AMIS-A Acronym for Audio Messaging Interchange Specification-Analog. See also AMIS. amplifier An electronic device used to increase the amplitude or power level of a signal. Amplifiers are used in telecommunications on analog transmission lines to offset the signal loss that occurs as the signal is propagated along the line. AN Acronym for access node. A broadband Integrated Services Digital Network (ISDN) remote switch that performs grooming, concentration, and switching functions. analog bridge A device for connecting multiple analog circuits to a common circuit. analog channel compression A technique for fitting more than one program into a single channel using analog processes. analog loop back See ALB. analog signal A continuous signal that is infinitely and continuously variable in amplitude and/or frequency. analog transmission The transmission of continuously variable (analog) signals. As a signal is transmitted along an analog network, the signal strength eventually weakens or attenuates. Amplifiers may be installed in the network to amplify the signal, but because there is no way to differentiate between an analog signal and noise, both are amplified. Therefore, noise tends to accumulate in an analog network. ANC Acronym for Answer, Charge. ANI Acronym for automatic number identification. A PSTN system that transmits the billing number of the calling party for accounting and billing purposes. ANM
- 50. Study Notes http://SlideShare.net/OxfordCambridge 50 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Acronym for answer message. An off-hook signal sent in the reverse direction that indicates when the called party answers. Billing starts when the answer message is received. ANN Acronym for Answer, No Charge. ANSI Acronym for American National Standards Institute. A U.S. organization chartered to accredit standards developed by a wide variety of industry groups while avoiding improper influence from any one company or organization. ANSI does not develop standards, but reviews and implements those developed by other organizations. For example, ANSI accredits standards for telephony developed by the Alliance for Telecommunications Industry Standards (ATIS) under the auspices of the T1 Committee, and standards for cellular radio developed by the Electronics Industry Association (EIA) and the Telecommunications Industry Association (TIA). ANSI is a member of the International Organization for Standardization (ISO). See also ATIS, EIA, and ISO. answerback A signal sent by a data receiver to a data transmitter indicating that it is ready to receive data or to acknowledge the receipt of data. answering machine A CPE device that, in the absence of the called party, automatically answers incoming calls with a prerecorded message and records messages from callers. ANU Acronym for Answer, Unqualified. a-number A cellular term referring to the number of the calling party. The originating switch analyzes the a-number in order to route a call to the b-number, the number of the called party. The a-number can be analyzed by configuring dial plans created with the dial plan provisioning (DPP) utility. See also dial plan and b-number. AOS Acronym for alternative operator service. A non-telephone company operator service. Users of AOS include hotels and non-telco public telephones where a commission is paid to the establishment for allowing the AOS to bill for the call. Many AOS operations have billing agreements with local exchange companies (LECs) which will pass the billed charges back to the customer's hotel room or home telephone number. API Acronym for application programming interface. Software that an application program uses to request and carry out lower-level services. application A software program that performs a function directly for a user. Examples include the Cisco CallManager administrative reporting tool (ART) and Bulk Administration Tool (BAT), as well as Microsoft Word. A web browser is a network application. application sharing A form of data collaboration that allows a participant to select one or more of the applications resident on his/her PC and make it available to the other participants. All participants may then manipulate the application as if it were executing on their PCs. area code The first three digits of a 10-digit telephone number in the North American Numbering Plan. See also NANP. ARP Acronym for Address Resolution Protocol. Internet protocol used to map an IP address to a MAC address. Defined in RFC 826. Allows host computers and routers to determine the data link layer address corresponding to the IP address in a packet routed through the LAN. Although the packet is addressed to an IP address, the LAN hardware responds only to data link layer addresses. The host or router with the destination IP address replies with its own data link layer address in an ARP response, which the forwarding host or router will use to construct a data link layer frame. The result is stored in cache memory so subsequent packets addressed to the same destination can be routed without an explicit ARP process. ARPA Acronym for Advanced Research Projects Agency of the U.S. Department of Defense. ARPA funded research and experimentation with ARPANET, the predecessor to the Internet. See also TCP/IP.
- 51. Study Notes http://SlideShare.net/OxfordCambridge 51 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) ARQ Acronym for automatic retransmission request (ARQ). A method of checking transmitted data on high speed data communications systems in which the sender encodes an error detection field based on the contents of the message. The receiver recalculates the check field and compares it with the received field. If the fields match, a positive acknowledgment ("ACK" or "PAK") is returned to the sender. If the fields do not match, a negative acknowledgment (NAK) is returned to the sender. ART An acronym for audible ringing tone. A signal sent back to the calling party to indicate the called number is ringing. Also, an acronym for administrative reporting tool. A web-based application for Cisco CallManager that generates reports on performance and service details. See also CDR and CMR. ARU Acronym for audio response unit. An output device that provides a spoken response to digital inquiries from a telephone or other device (For example, "Press 1 to hear this information again; Press 2 to hear more options.") Also known by the generic name audiotex. ASIC Acronym for application specific integrated circuit. Circuit designs used by manufacturers to consolidate many chips into a single package, reducing board size and power consumption. AST Acronym for automatic spanning tree. Function that supports the automatic resolution of spanning trees in source-route bridging networks, providing a single path for spanning explorer frames to traverse from a given node in the network to another. AST is based on the IEEE 802.1 standard. See also SRB. AT Acronym for Analog Access Trunk. Expressed as AT-2, AT-4, or AT-8 to correspond to 2-, 4-, and 8-port gateways. ATB Acronym for all trunks busy. A single tone repeated at a 120 impulse per minute (ipm) rate to indicate that all trunks in a routing group are in use. ATIS Acronym for Alliance for Telecommunications Industry Standards, a Washington D.C. trade group heavily involved in standards issues, including interconnection and interoperability issues. ATM Acronym for Asynchronous Transfer Mode. International standard for cell relay in which multiple service types (such as voice, video, or data) are conveyed in fixed-length (53-byte) cells. Fixed-length cells allow cell processing to occur in hardware, thereby reducing transit delays. ATM is designed to take advantage of high-speed transmission media such as E3, SONET, and T3. attendant console A large, specialized telephone set used by the operator to answer incoming calls and send those calls to the proper extension. audio stream RTP packets Capable of conducting real-time voice data over connectionless networks such as TCP/IP. See also RTP. audio switch A remote controlled device for switching conference room audio circuits that are used to deliver compressed video transmission service. An audio switch can switch room audio connections to either a coder/decoder or a separate return required for multipoint conferences. See also codec. audiotex Generic term for interactive voice response equipment and services. See also ARU. authentication The process of determining the identity of a user attempting to access a system. authorization The process of granting a user access to a system. auto registration
- 52. Study Notes http://SlideShare.net/OxfordCambridge 52 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Process by which Cisco CallManager automatically detects and adds new IP telephony devices to its database, such as Cisco IP Phones and Cisco DPA 7630 devices. Auto registration assigns the next available directory number designated for the device type at the time that each new device is plugged into the network. automatic callback A feature of a telecommunications system or an IP telephony device that records, and can dial, the originating phone number of the last incoming call. availability The degree to which a system or resource is operable and not in a state of congestion or failure at any given point in time. AVD Acronym for alternate voice data. A single transmission facility used for either voice or data. AVVID See Cisco AVVID. back end Functions and procedures of a database server, such as a node or software application, designed to manipulate data on a network. See also client, FRF.11, and server. back haul A method of call routing in which the call is taken beyond its destination and then back to that destination. Usually used to attain cheaper rates. backup The logical or physical provisioning of facilities to speed the process of restart and recovery following network failures. Also, redundant facilities, including duplicated transaction files, duplicated processors, storage devices, terminal, telecommunications hardware or switches. band The range of frequencies between two defined limits. Also, one of the six specific wide-area telephone service (WATS) geographic service areas. bandwidth Difference between the highest and lowest frequencies available for network signals. Amount of data that can be transmitted in a fixed amount of time, or the rated throughput capacity of a given network medium or protocol. baseband A network technology in which only one carrier frequency is used (for example, Ethernet). bastion server A server that is accessible from a public network (such as the Internet) without protection from a firewall. BAT Acronym for bulk administration tool. A web-based application for Cisco CallManager that enables bulk system modifications, including adding and deleting phones, modifying phones, and adding users and mailboxes. BGP Acronym for Border Gateway Protocol. The routing protocol used between separate administrative domains (for example, between an enterprise corporation and its ISP). BH Acronym for busy hour. The peak 60-minute period during a business day when the largest volume of traffic is handled by a network. B-ISDN Acronym for Broadband Integrated Services Digital Network. A network that employs switching techniques independent of transmission speeds, and that allows a network to expand its capacity without major equipment overhauls. B-lSDNs support gigabit speed circuits in the public network and high speed switching of all traffic types in public and private networks. B-lSDNs also provide bandwidth-on-demand capabilities. Contrast with N-ISDN. See also BRI, ISDN, and PRI.
- 53. Study Notes http://SlideShare.net/OxfordCambridge 53 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) blind transfer Passing a call without notifying the recipient. Also known as unsupervised transfer or cold transfer. blocked call An attempted call that cannot be connected. The two most common reasons for blocked calls are all lines or trunks to the central office are in use, or all paths through a private branch exchange (PBX) or switch are in use. Also, a service offered by 900 providers that permits users to request that their local carrier blocks all 900 calls in order to avoid incurring charges. blocking The inability to establish a new call because of restrictions or inaccessibility of facilities in the system being called. b-number A cellular term for the number of the called party. The originating switch analyzes the a-number, the number of the calling party, in order to route the call to the b-number. See also a-number. BOOTP Acronym for Bootstrap Protocol. A TCP/IP protocol that enables a network device to discover certain startup information, such as its IP address. BPDU Acronym for Bridge Protocol Data Unit. Spanning-Tree Protocol hello packet that is sent out at configurable intervals to exchange information among bridges in the network. See also PDU. break To interrupt the sending of a message and take control of the circuit at the receiving end. Also, an interruption of a transmission or process. BRF Acronym for Bridge Relay Function. As defined by the IEEE, an internal bridge function on a Token Ring switch that is responsible for forwarding frames between port groupings with the same logical ring number. Within a BRF, source-route bridging or source-route transparent bridging can be used to forward frames. See also CRF. BRI Acronym for Basic Rate Interface. ISDN interface composed of two B-channels and one D-channel for circuit-switched communication of voice, video, and data. Compare with PRI. See also B-ISDN, ISDN, and N-ISDN. bridge A device that passes information between two network segments. Operates at layer 2 of the Open Systems Interconnection (OSI) reference model (the data link layer). See OSI. Also, a device used to match circuits to each other to ensure minimum transmission impairment. Bridging is normally required on multipoint data channels where several local loops or channels are interconnected. Bridged Telnet Offers Cisco Service Engineers (CSEs) transparent firewall access to the Cisco CallManager server on a customer site for diagnostic and troubleshooting purposes. It enables a telnet client inside the Cisco Systems firewall to connect to a telnet process behind a customer firewall. broadband A type of communications channel capable of carrying a large portion of the electromagnetic spectrum. A broadband channel can accommodate the following media: audio, digital, and television. Also, a transmission facility having a bandwidth greater than 20 kHz capable of high speed data transmission. Also, an analog transmission technique used with data and video transmissions that provides multiple user channels through frequency-division multiplexing (FDM). See FDM. broadcast Data packet that is sent to all nodes on a network. Broadcasts are identified by a broadcast address. Compare with multicast and unicast. See also broadcast address. broadcast address Special address reserved for sending a message to all stations. Generally, a broadcast address is a MAC destination address of all ones. Compare with multicast address and unicast address. See also broadcast. broadcast packet
- 54. Study Notes http://SlideShare.net/OxfordCambridge 54 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) A data packet transmitted simultaneously to all network devices. broadcast storm An undesirable network event in which many broadcasts are sent at once. Broadcast storms use substantial network bandwidth and may cause network time-outs. browser GUI-based hypertext client application, such as Internet Explorer, Mosaic, and Netscape Navigator, used to access hypertext documents and other services located on innumerable remote servers throughout the World Wide Web and Internet. See also GUI. BSI Acronym for Basic Rate Interface. ISDN interface composed of two B-channels and one D-channel for circuit-switched communication of voice, video, and data. Bulk Administration Tool See BAT. busy A call condition in which transmission facilities are already in use. A line is considered busy when the caller goes off-hook. busy tone A single tone that is repeated at a 60 impulse per minute (ipm) rate to indicate that a call's terminating location is already in use. CAC Acronym for call admission control. In Cisco CallManager, CAC maintains a desired level of voice quality over a WAN link by regulating bandwidth consumption used by calls over the link. Limits the number of simultaneous active calls over the link. See also locations and gatekeeper. call admission control See CAC. call control Telephone industry term used to describe the setting up, monitoring, and tearing down of phone calls. call detail recording See CDR. call forward all calls Configurable feature that re-routes all incoming calls destined for one telephony device to another phone or device. call forward busy Configurable feature that re-routes incoming calls to an alternate line when the first line is in use. call forward no answer Configurable feature that re-routes incoming calls from one phone to another phone when the first phone is not answered after a certain number of rings. call forwarding Configurable feature that sends incoming calls routed to a particular directory number to another number. Call Management Record See CMR. call park Configurable feature that allows the user to deposit a stable call at a specified directory number, then go to another phone and dial the park number to retrieve the call. (Call park differs from a "hold" feature by allowing the user to retrieve the call from any phone on the same system. A system administrator must configure a call park number, or range of numbers, for this feature to work). call pickup Configurable feature that allows a user to redirect an incoming call that routed to another destination in order to retrieve the call on the user's own phone or directory number. See also group call pickup.
- 55. Study Notes http://SlideShare.net/OxfordCambridge 55 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) call processing See distributed call processing and centralized call processing. call waiting Feature of telephony systems that notifies a caller when another call is coming in during an active call. callback Callback allows remote clients to dial into a central site, and then have the central site immediately call back the remote site. caller ID A display, available to the called party before the party answers a telephone call, that identifies the originating telephone number and the subscriber's name associated with that number. See also CLID. Calling Line Identification See CLID. calling party transformation settings Allows the user to manipulate the appearance of the calling party's number for outgoing calls. calling search space Determines which partitions a calling device searches when attempting to complete a call. camp on A technique in which an incoming call is stored on hold until an attendant, trunk, trunk group, or station is available to accept it, at which time the call is completed. CAS Acronym for centralized attendant service. One group of switchboard operators answers all incoming calls for several telephone systems located throughout one city or region. Also, acronym for channel associated signaling. In-band signaling used to provide emergency signaling information along with a wireless 911 call to the Public Safety Answering Point (PSAP). CBQ Acronym for class-based queuing. A queuing algorithm used in routers to manage congestion. Through user-definable class definitions, incoming packet traffic is divided into classes. These divisions might fall along the lines of traffic from a given interface, associated with a particular application, intended for a particular network or device destination, and all traffic of a specific priority classification. Each class of traffic is assigned to a specific first-in-first-out (FIFO) queue, each of which is guaranteed some portion of the total bandwidth of the router. See also WFQ. CBWFQ Acronym for class-based weighted fair queuing. Allows you to define traffic classes that are based on certain match criteria, such as access control lists, input interface names, protocols, and Quality of Service (QoS) labels. CC Acronym for common carrier. A government regulated private company that furnishes the general public with telecommunications services and facilities. Also, acronym for country code. Part of a numbering plan. CCAPI Acronym for Call Control Applications Programming Interface. CCIS Acronym for Common Channel Interoffice Signaling. A way of carrying telephone signaling information along a path different from the path used to carry voice. CCIS occurs over a separate packet-switched digital network. Accelerates the setting up and tearing down of phone calls and increases the amount of information compared to what can be carried by in-band signaling. See SS7. CCITT Acronym for Consultative Committee for International Telegraph and Telephone. A telecommunications organization that recommended worldwide standards for common carrier communications services. This organization was superseded by the International Telecommunications Union, now called the ITU-T. See ITU-T. CCS
- 56. Study Notes http://SlideShare.net/OxfordCambridge 56 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Acronym for Common Channel Signaling. Signaling system used in telephone networks that separates signaling information from user data. A specified channel is exclusively designated to carry signaling information for all other channels in the system. See CCIS. CDB Acronym for call detail blocking. CDP Acronym for Cisco Discovery Protocol. A device-discovery protocol that runs on all Cisco-manufactured equipment. Enables a device to advertise its existence to other devices and receive information about other devices in the network. Cisco IP devices use CDP to communicate information such as auxiliary VLAN ID, per port power management details, and quality of service (QoS) configuration information with the Cisco Catalyst switch. See also VLAN and QoS. CDR Acronym for call detail recording. A stored database record containing data about a specific call. Processed as a unit and used to create billing records, a CDR contains details such as the called and calling parties, originating switch, terminating switch, call length, and time of day. cell Basic data unit for ATM switching and multiplexing. Cells contain identifiers that specify the data stream to which they belong. Each cell consists of a 5-byte header and 48 bytes of payload. See also cell relay and ATM. cell relay Network technology based on the use of small, fixed-size packets, or cells. Because cells are fixed-length, they can be processed and switched in hardware at high speeds. Cell relay is the basis for many high-speed network protocols including ATM, 802.6, and SMDS. See also cell, ATM, and SMDS. central office See CO. centralized call processing Refers to a processing construct where all call processing is performed at a central site, or hub, and no call processing is performed at branch sites. channel service unit See CSU. CHAP Acronym for Challenge/Handshake Authentication Protocol. A system for determining if a user has the correct password without openly revealing that password. CHAP does not itself prevent unauthorized access, it merely identifies the remote end. The router or access server then determines whether that user is allowed access. checksum Method for checking the integrity of transmitted data. A checksum is an integer value computed from a sequence of octets taken through a series of arithmetic operations. The value is recomputed at the receiving end and compared for verification. CIR Acronym for committed information rate. A Frame Relay term identifying a certain average maximum data transmission rate. circuit switching Switching system in which a dedicated physical circuit path must exist between sender and receiver for the duration of the "call." Used heavily in the public switched telephone network. circuit-switched gateways Gateways that require an open circuit for communications until the connection is released. See also gateway. Cisco AVVID Acronym for Cisco Architecture for Voice, Video, and Integrated Data. Cisco CallManager Software-based call processing component of the Cisco IP telephony solution, which extends enterprise telephony features and functions to packet telephony network devices such as IP phones, media processing devices, voice-over-IP (VoIP) gateways, and multimedia applications. See also Cisco CallManager Administration.
- 57. Study Notes http://SlideShare.net/OxfordCambridge 57 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) Cisco CallManager Administration Graphical user interface used to configure and maintain the Cisco CallManager. Cisco CallManager Directory An LDAP directory that stores authentication and authorization information about telephony application users. See also LDAP. Cisco CallManager group A set of Cisco CallManagers that provide a failover scheme for the devices associated with that group. Defined and maintained through Cisco CallManager Administration. Cisco CallManager server Cisco's high-availability server platform on which Cisco CallManager software comes preinstalled. Cisco Discovery Protocol See CDP. Cisco IP Phone A full-feature telephone that provides voice communication over an IP network while functioning much like a traditional analog phone. Allows you to place and receive telephone calls, and supports features such as call forwarding, redial, speed dialing, call transfer, and conference calling. Also allows you to access voice mail, providing connectivity to Cisco IP Telephony Solutions. Cisco IP Telephony Solutions A software and hardware product suite offering an IP alternative to traditional PBXs. Includes Cisco IP Phones, H.323-compatible gateway clients, and server software enabling voice and data over an existing LAN or WAN infrastructure. See also Cisco IP Phone, Cisco CallManager. Cisco Media Convergence Servers The Cisco MCS-7800 series server family, which includes the high-availability MCS-7830 and the Cisco AVVID IP telephony starter kits. Comes with Cisco CallManager preloaded. CLID Acronym for caller line ID. Information about the billing telephone number from which a call originated. The CLID value might be the entire phone number, the area code, or the area code plus local exchange. Also known as called Caller ID. client Node or software program (front-end device) that requests services from a server. The Cisco IP Phone is an example of a client. client/server computing Term used to describe distributed computing (processing) network systems in which transaction responsibilities are divided into two parts: client (front end) and server (back end). Both terms (client and server) can be applied to software programs or actual computing devices. Also called distributed computing (processing). See also back end and client. client-server model The process of workload sharing between the client, the server, and the network. Examples include the nameserver/nameresolver paradigm of the domain name system (DNS), as well as fileserver/file-client relationships, such as network file system (NFS) and diskless hosts. See also DNS and NFS. closest-match routing The process of matching the narrowest range of numbers in a given route pattern. CMR Acronym for call management record. Contains the count of bytes sent, packets sent, jitter, latency, dropped packets, etc. Also called diagnostic records. CNF Acronym for a configuration file. CO Acronym for central office. Local telephone company office to which all local loops in a given area connect and in which circuit switching of subscriber lines occurs. Central office can also refer to a single telephone switch, or what is known as a "public exchange" in Europe.
- 58. Study Notes http://SlideShare.net/OxfordCambridge 58 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) codec Acronym for coder-decoder. A device that typically uses pulse code modulation to transform analog signals into a digital bit stream, and digital signals back to analog. See also <a href="#n."><span class="crossref">G .</span></a> , , and . Also, in Voice over IP, Voice over Frame Relay, and Voice over ATM, a software algorithm used to compress/decompress speech or audio signals. community strings Passwords used by Simple Network Management Protocol to remotely manage network devices. See also SNMP. companding Contraction derived from the opposite processes of compression and expansion. Part of the pulse code modulation process, whereby analog signal values are logically rounded to discrete scale-step values on a nonlinear scale. The decimal step number is then coded in its binary equivalent prior to transmission. The process is reversed at the receiving terminal using the same nonlinear scale. Compare with compression and expansion. See also a-law and µ-law. companding law See a-law and µ-law. compression Reducing the representation of the information, but not the information itself. Compression is accomplished by running a data set through an algorithm that reduces the space required to store or the bandwidth required to transmit the data set. See also expansion. compression types One of the key factors that determines the amount of bandwidth used per call. Compression types available in Cisco CallManager are G.711 (default), G.723, and G.729. conference bridge A network used to interconnect three or more lines or trunks to allow simultaneous conversations. conference call A connection established between three or more stations that allows each station to communicate with all others simultaneously. configuration file An unformatted ASCII file that stores initialization information for an application. For Cisco CallManager, files in the .cnf format that define the parameters for Cisco IP Phone connection. CoS Acronym for class of service. Also, an indication of how an upper-layer protocol requires a lower-layer protocol to treat its messages. In SNA sub-area routing, CoS definitions are used by sub-area nodes to determine the optimal route to establish a given session. A CoS definition contains a virtual route number and a transmission priority field. Also called type of service (ToS). Also, a collection of features, privileges, and services that are easily assignable to a group or "class" of telephones. Class of service is used to simplify administration and maintenance tasks in complex telephony networks. country code A one-, two-, or three-digit number used to specify the destination country for international calls. See also route filter tags. CPE Acronym for customer premises equipment. Telephone equipment, such as key systems, PBXs, answering machines, etc., that reside on the customer's premises (e.g., office building, home office, or factory). Also called customer provided equipment. CPU Acronym for Central Processing Unit. The computing part, or "brain," of the computer. The CPU manipulates data and processes instructions coming from software or manual operations. CRF Acronym for cell relay function. The basic function that an ATM network performs in order to provide a cell relay service to ATM end- stations. Also, acronym for connection related function. A term used by Traffic Management to reference a point in a network or a network element where per connection functions are occurring. This is the point where policing at the virtual channel connection or virtual path connection level may occur.
- 59. Study Notes http://SlideShare.net/OxfordCambridge 59 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) cRTP Acronym for compressed Real-time Transport Protocol. See RTP. CSU Acronym for channel service unit. Digital interface device that connects end-user equipment to the local digital telephone loop. Often referred to together with DSU as CSU/DSU. See also DSU. Also, acronym for channel status unit. A device used in conjunction with a T-1 multiplexor that monitors each channel of the T-1 to ensure it is functioning properly. CTI ports Acronym for Computer Telephony Interface ports. Virtual devices that are used by Cisco CallManager applications such as Cisco SoftPhone, Cisco IP AutoAttendent, and Cisco IP Interactive Voice Response System (IVR) to create virtual lines. CTI ports are configured through the same Cisco CallManager Administration area as phones, but require different configuration settings. CTI route point Acronym for Computer Telephony Interface route point. Virtual device that can receive multiple simultaneous calls for the purpose of application-controlled redirection. Once a CTI route point has been created, lines (directory numbers) can be added and configured. Applications that use CTI route points include Cisco IP Auto Attendant, Cisco IP Interactive Voice Response System (IVR), and Cisco TAPI/JTAPI. data channel See D-channel. data service unit See DSU. database redundancy See redundancy. datagram Logical grouping of information sent as a network layer unit over a transmission medium without prior establishment of a virtual circuit. IP datagrams are the primary information units in the Internet. The terms cell, frame, message, packet, and segment are also used to describe logical information groupings at various layers of the OSI reference model and in various technology circles. D-channel Acronym for data channel. Full-duplex, 16-kbps (BRI) or 64-kbps (PRI) ISDN channel used to carry control signals and customer call data in a packet switched mode. Provides the signaling information for each of the voice channels (or B-channels). DCOM Acronym for Distributed Component Object Model. Protocol that enables software components to communicate directly over a network. Developed by Microsoft and previously called Network OLE, DCOM is designed for use across multiple network transports, including Internet protocols such as HTTP. DDI Acronym for discard digits instruction. Removes a portion of the dialed digit string before passing the number on to the adjacent system. For example, DDI can remove an external access code from the dialed digit string for calls placed to a PSTN. default router For IP devices, identifies the default gateway used by the device. Also called default gateway. device loads Files that contain updated application software for phones or gateways. Provided automatically during installation or upgrades. See also patch. device pool In Cisco CallManager, a collection of commonly configured devices (such as phones, computers and gateways,) that belong to a common database, cluster and group. Use device pools to define common characteristics for devices, including region, Date/Time Group, Cisco CallManager group, and calling search space for auto-registration. DHCP Acronym for Dynamic Host Configuration Protocol. A TCP/IP protocol that enables PCs and workstations to get temporary or permanent IP addresses out of a pool from centrally-administered servers. Like its predecessor, BOOTP, DHCP provides a mechanism
- 60. Study Notes http://SlideShare.net/OxfordCambridge 60 | P a g e S I P ( S e s s i o n I n i t i a t i o n P r o t o c o l ) for allocating IP addresses manually, automatically and dynamically, so that addresses can be reused when hosts no longer need them. Also, for Cisco CallManager, a DHC server is queried by a telephone or gateway device upon booting to determine network configuration information. The DHCP server provides the device with an IP address, subnet mask, default gateway, DNS server, and a TFTP server name or address. With Cisco IP Phones, DHCP is enabled by default. If disabled, you must manually enter the IP address and other specifications manually on each phone locally. dial pad Buttons on a phone that are used to dial a phone number. The dial pad on a Cisco IP Phone operates like the dial pad on a traditional telephone. dial plan A system that allows one telephone or Cisco IP device to connect to another telephone or Cisco IP device by using dialed digits. In North America and many Caribbean nations, the dial plan is called the North American Numbering Plan. See also NANP. dial tone An audible signal that indicates automatic switching equipment is ready to receive DTMF or dial pulse signals required for a connection. See also DTMF. dialing sequence Used to enable and disable the message waiting indicator. See also MWI. Dialogic voice board Printed circuit board containing digital signal processor (DSP) chips to digitize voice. dial-up The use of a rotary or dual tone multiple frequency (DTMF) telephone to initiate a call over the public switched telephone network. See also DTMF. dial-up line A communications circuit established by a switched connection. Also, any circuit available over the public switched telephone network. See also PSTN. DID Acronym for direct inward dialing. A method of directly dialing the directory number of a Cisco IP Phone or a telephone attached to a PBX without routing calls through an attendant or an automated attendant console, such as Cisco WebAttendant. Compare to DOD. direct inward dialing See DID. direct outward dialing See DOD. directory number See DN. directory services A service that provides information about network objects and helps network devices locate service providers. distributed call processing A processing construct in which each central site and branch office contains its own call processing resources. In terms of the Cisco CallManager, distributed call processing means that each central site and branch site contains its own Cisco CallManager or Cisco CallManager cluster. DN Acronym for directory number. The telephone number or internal extension assigned to a Cisco IP Phone. The directory number is assigned to the phone itself, not a location or a user, so if the phone is moved, it still retains the same directory number. Also called subscriber number. DNIS Acronym for dialed number identification service. DNS
