Password-dependent password-killer
Post-truth cybersecurity? Another subject of AGNOTOLOGY? Can there be such a thing in this universe as a password-killer that is dependent on the password? In cyberspace, biometric solutions could be recommended only to the people who want better convenience, not to the people who need better security. Update on 3/Feb/2017- NIST is now with us about the use of biometrics, with its latest draft saying "Biometrics SHALL be used with another authentication factor (something you have)" at 5.2.3, which is tantamount to "Biometrics is no good when used without another factor" https://pages.nist.gov/800-63-3/sp800-63b.html < References > Password Fatigue and Expanded Password System http://www.slideshare.net/HitoshiKokumai/password-fatigue-and-expanded-password-system Waiting for NIST’s view on “password-dependent biometrics” http://www.slideshare.net/HitoshiKokumai/waiting-for-nists-view-on-passworddependent-biometrics
Recommended
Recommended
More Related Content
More from Hitoshi Kokumai
More from Hitoshi Kokumai (8)
Recently uploaded
Recently uploaded (20)
Password-dependent password-killer
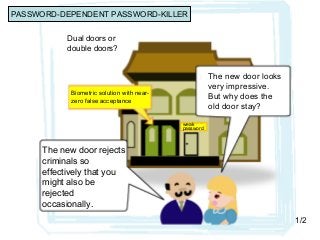
- 1. Dual doors or double doors? Biometric solution with near- zero false acceptance weak password The new door looks very impressive. But why does the old door stay? The new door rejects criminals so effectively that you might also be rejected occasionally. 1/2 PASSWORD-DEPENDENT PASSWORD-KILLER
- 2. What ! Biometric solution with near- zero false acceptance weak password Very convenient!! I can attack both of the two. 2/2
- 3. PASSWORD-DEPENDENT PASSWORD-KILLER Media seem busy spreading the hyped stories of “password-killing” biometric products. For biometrics to displace the password for better security, however, it must stop depending on a password registered in case of false rejection. A man who depends on a stick for a walk cannot claim that he is killing the stick dead while having a walk with his stick firmly held in his hand. Are we talking about cyber security or about what could occur in Alice’s Wonderland?
- 4. Biometrics operated together with Password Threats that can be thwarted by biometric products operated together with backup passwords (rescue/fallback/ alternative passwords) can be thwarted more securely by a passwords-only authentication. We could be certain that biometrics would help for security ONLY WHEN it is operated together with another factor by AND/Conjunction (we need to go through both of the two), NOT WHEN operated with another factor by OR/Disjunction (we need only to go through either one of the two) as in the cases of Touch ID and many other biometric products on the market that require a backup/fallback password, which only increase the convenience while bringing down the security.
- 5. AND/Conjunction or OR/Disjunction Biometric sensors and monitors, whether static, behavioral or electromagnetic, can theoretically be operated together with passwords in two ways, (1) by AND/conjunction or (2) by OR/disjunction. The cases of (1) are hardly known in the real world because the falsely rejected users would have to give up the access altogether even if they can recall their passwords Biometric products like Apple's Touch ID are operated by (2) so that the falsely rejected users can unlock the devices by registered passwords. This means that the overall vulnerability of the product is the sum of the vulnerability of biometrics (x) and that of a password (y). The sum (x + y - xy) is necessarily larger than the vulnerability of a password (y), say, the devices with Touch ID and other biometric sensors are less secure than the devices protected by a password-only authentication,.
- 6. Save Biometrics’ Reputation It is not possible to compare the strength of biometrics operated on its own with that of a password operated on its own. There are no objective data about the overall vulnerability of biometric solutions (not just false acceptance rate when false rejection is near-zero but also the risk of forgery of body features and the risk of use when the user is unconscious) and that of the passwords (not only that it may be as low as 10 bits or as high as 100 bits but also that it could be stolen and leaked.) Such a terrible nonsense as the “password-dependent password- killer” should be killed dead lest the good reputation of biometrics as excellent identification tools for physical security should be damaged. Biometric solutions in cyber space could be recommended to the people who want better convenience, not to the people who need better security so long as they are dependent on the backup/fallback passwords..
- 7. Save Biometrics’ Reputation It is not possible to compare the strength of biometrics operated on its own with that of a password operated on its own. There are no objective data about the overall vulnerability of biometric solutions (not just false acceptance rate when false rejection is near-zero but also the risk of forgery of body features and the risk of use when the user is unconscious) and that of the passwords (not only that it may be as low as 10 bits or as high as 100 bits but also that it could be stolen and leaked.) Such a terrible nonsense as the “password-dependent password- killer” should be killed dead lest the good reputation of biometrics as excellent identification tools for physical security should be damaged. Biometric solutions in cyber space could be recommended to the people who want better convenience, not to the people who need better security so long as they are dependent on the backup/fallback passwords..
