Curriculum Vitae Summary
•
0 gefällt mir•102 views
Curriculum Vitae Summary
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (20)
Manage your Information Security Management System (ISMS) with Odoo

Manage your Information Security Management System (ISMS) with Odoo
How to implement a robust information security management system?

How to implement a robust information security management system?
Resolution - Security - Cisco Advanced Malware Protection for Endpoints - Fea...

Resolution - Security - Cisco Advanced Malware Protection for Endpoints - Fea...
Improve Cybersecurity posture by using ISO/IEC 27032

Improve Cybersecurity posture by using ISO/IEC 27032
5 Things to Know about Safety and Security of Embedded Systems

5 Things to Know about Safety and Security of Embedded Systems
13.Anton-Position-Security-Considerations-23June2015[1]![13.Anton-Position-Security-Considerations-23June2015[1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
![13.Anton-Position-Security-Considerations-23June2015[1]](data:image/gif;base64,R0lGODlhAQABAIAAAAAAAP///yH5BAEAAAAALAAAAAABAAEAAAIBRAA7)
13.Anton-Position-Security-Considerations-23June2015[1]
ISO 27001 - Information security user awareness training presentation - part 3

ISO 27001 - Information security user awareness training presentation - part 3
How Computer Network Support System Work Against Hacking?

How Computer Network Support System Work Against Hacking?
10 Common Security Mistakes Businesses Make and How to Avoid Them 

10 Common Security Mistakes Businesses Make and How to Avoid Them
Ähnlich wie Curriculum Vitae Summary
Cara pengujian Kemanan PerangkatSosialisasi sni iso iec 15408 common criteria - evaluasi keamanan ti

Sosialisasi sni iso iec 15408 common criteria - evaluasi keamanan tiSarwono Sutikno, Dr.Eng.,CISA,CISSP,CISM,CSX-F
Design Control atau Risk Treatment untuk Kartu Cerdas untuk Pembayaran. Control dari Tata kelola, manajemen sampai tingkat perangkat.Sarwono sutikno forum tik utk standardisasi keamanan kartu cerdas - 4 nov 2...

Sarwono sutikno forum tik utk standardisasi keamanan kartu cerdas - 4 nov 2...Sarwono Sutikno, Dr.Eng.,CISA,CISSP,CISM,CSX-F
Ähnlich wie Curriculum Vitae Summary (20)
ISO/IEC 27001, ISO/IEC 27002 and ISO/IEC 27032: How do they map?

ISO/IEC 27001, ISO/IEC 27002 and ISO/IEC 27032: How do they map?
ET4045-Information Security Management System-2018

ET4045-Information Security Management System-2018
Iso iec 27001 foundation training course by interprom

Iso iec 27001 foundation training course by interprom
Chapter 1 Best Practices, Standards, and a Plan of Action.pptx

Chapter 1 Best Practices, Standards, and a Plan of Action.pptx
102 Information security standards and specifications

102 Information security standards and specifications
Sosialisasi sni iso iec 15408 common criteria - evaluasi keamanan ti

Sosialisasi sni iso iec 15408 common criteria - evaluasi keamanan ti
Information Security Management System ISO/IEC 27001:2005

Information Security Management System ISO/IEC 27001:2005
Information Assurance And Security - Chapter 1 - Lesson 4

Information Assurance And Security - Chapter 1 - Lesson 4
Sarwono sutikno forum tik utk standardisasi keamanan kartu cerdas - 4 nov 2...

Sarwono sutikno forum tik utk standardisasi keamanan kartu cerdas - 4 nov 2...
Curriculum Vitae Summary
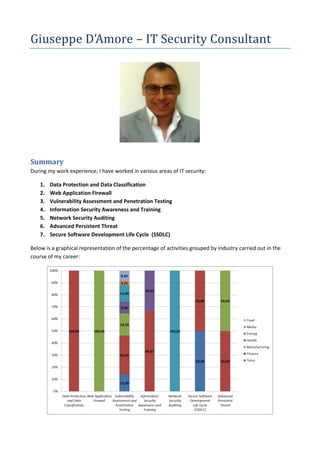
- 1. Giuseppe D’Amore – IT Security Consultant Summary During my work experience, I have worked in various areas of IT security: 1. Data Protection and Data Classification 2. Web Application Firewall 3. Vulnerability Assessment and Penetration Testing 4. Information Security Awareness and Training 5. Network Security Auditing 6. Advanced Persistent Threat 7. Secure Software Development Life Cycle (SSDLC) Below is a graphical representation of the percentage of activities grouped by industry carried out in the course of my career:
- 2. Information Security Standards Familiar with the following standards, best practices and guidelines: 1. ISO 27001 1.1. Information security management systems - Requirements 2. ISO 27002 2.1. Code of practice for information security controls 3. ISO 27003 3.1. Information security management system implementation guidance 4. ISO 27005 4.1. Information security risk management 5. NIST SP 800-30 5.1. Guide for Conducting Risk Assessments 6. NIST SP 800-37 6.1. Guide for Applying the Risk Management Framework 7. NIST SP 800-53 7.1. Security and Privacy Controls 8. NIST SP 800-82 8.1. Guide to Industrial Control Systems (ICS) Security 9. NIST SP 800-100 9.1. Information Security Handbook: A Guide for Managers Reading List I read the following books: 1. Sicurezza delle Informazioni 1.1. Cesare Gallotti 2. CISM Review Manual 2014 2.1. ISACA 3. IT Governance: A Manager’s Guide to Data Security and ISO 27001/ISO 27002 3.1. Alan Calder 3.2. Steve Watkins 4. Managing Risk and Information Security: Protect to Enable 4.1. Malcolm Harkins