An overview of web security
•
4 gefällt mir•3,295 views
Everything you ever wanted to know about web security in one single infographic: lien. Includes 20 essential tips for an effective protection against cyberattacks!!
Melden
Teilen
Melden
Teilen
Downloaden Sie, um offline zu lesen
Empfohlen
Empfohlen
Weitere ähnliche Inhalte
Was ist angesagt?
Was ist angesagt? (10)
Survey on the Impact of BYOD on Enterprise Security

Survey on the Impact of BYOD on Enterprise Security
Andere mochten auch
Andere mochten auch (20)
Claudine florence three tools to use in a singing career

Claudine florence three tools to use in a singing career
Ähnlich wie An overview of web security
Ähnlich wie An overview of web security (20)
Expert Web App Pen Testing - Aardwolf Security.pptx

Expert Web App Pen Testing - Aardwolf Security.pptx
State of Web Application Security by Ponemon Institute

State of Web Application Security by Ponemon Institute
ISACA 2016 Annual Conference SA_State of Risk_Tunde Ogunkoya_DeltaGRiC_Consul...

ISACA 2016 Annual Conference SA_State of Risk_Tunde Ogunkoya_DeltaGRiC_Consul...
A Proposal to Improve Security of IT Systems in UOTC Inc..docx

A Proposal to Improve Security of IT Systems in UOTC Inc..docx
Why Speech Recognition Technology is the New Watchword for Enterprise Cyber S...

Why Speech Recognition Technology is the New Watchword for Enterprise Cyber S...
The Internet Is a Dog-Eat-Dog World, and Your App Is Clad in Milk-Bone Underwear

The Internet Is a Dog-Eat-Dog World, and Your App Is Clad in Milk-Bone Underwear
Mojave Networks Webinar: A Three-Pronged Approach to Mobile Security

Mojave Networks Webinar: A Three-Pronged Approach to Mobile Security
Mehr von Bee_Ware
Mehr von Bee_Ware (20)
Les francais et la protection des données personnelles

Les francais et la protection des données personnelles
Les entreprises européennes sont elles bien armées pour affronter les cyber a...

Les entreprises européennes sont elles bien armées pour affronter les cyber a...
Les principales failles de sécurité des applications web actuelles

Les principales failles de sécurité des applications web actuelles
Guide de mise en oeuvre d'une authentification forte avec une cps

Guide de mise en oeuvre d'une authentification forte avec une cps
Clusif le role de l'organisation humaine dans la ssi 2013

Clusif le role de l'organisation humaine dans la ssi 2013
Kürzlich hochgeladen
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...Enterprise Knowledge
Kürzlich hochgeladen (20)
Driving Behavioral Change for Information Management through Data-Driven Gree...

Driving Behavioral Change for Information Management through Data-Driven Gree...
Axa Assurance Maroc - Insurer Innovation Award 2024

Axa Assurance Maroc - Insurer Innovation Award 2024
Injustice - Developers Among Us (SciFiDevCon 2024)

Injustice - Developers Among Us (SciFiDevCon 2024)
08448380779 Call Girls In Diplomatic Enclave Women Seeking Men

08448380779 Call Girls In Diplomatic Enclave Women Seeking Men
The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf

The Role of Taxonomy and Ontology in Semantic Layers - Heather Hedden.pdf
Breaking the Kubernetes Kill Chain: Host Path Mount

Breaking the Kubernetes Kill Chain: Host Path Mount
08448380779 Call Girls In Greater Kailash - I Women Seeking Men

08448380779 Call Girls In Greater Kailash - I Women Seeking Men
IAC 2024 - IA Fast Track to Search Focused AI Solutions

IAC 2024 - IA Fast Track to Search Focused AI Solutions
Automating Google Workspace (GWS) & more with Apps Script

Automating Google Workspace (GWS) & more with Apps Script
TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments

TrustArc Webinar - Stay Ahead of US State Data Privacy Law Developments
Kalyanpur ) Call Girls in Lucknow Finest Escorts Service 🍸 8923113531 🎰 Avail...

Kalyanpur ) Call Girls in Lucknow Finest Escorts Service 🍸 8923113531 🎰 Avail...
Top 5 Benefits OF Using Muvi Live Paywall For Live Streams

Top 5 Benefits OF Using Muvi Live Paywall For Live Streams
Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...

Strategies for Unlocking Knowledge Management in Microsoft 365 in the Copilot...
The 7 Things I Know About Cyber Security After 25 Years | April 2024

The 7 Things I Know About Cyber Security After 25 Years | April 2024
08448380779 Call Girls In Friends Colony Women Seeking Men

08448380779 Call Girls In Friends Colony Women Seeking Men
An overview of web security
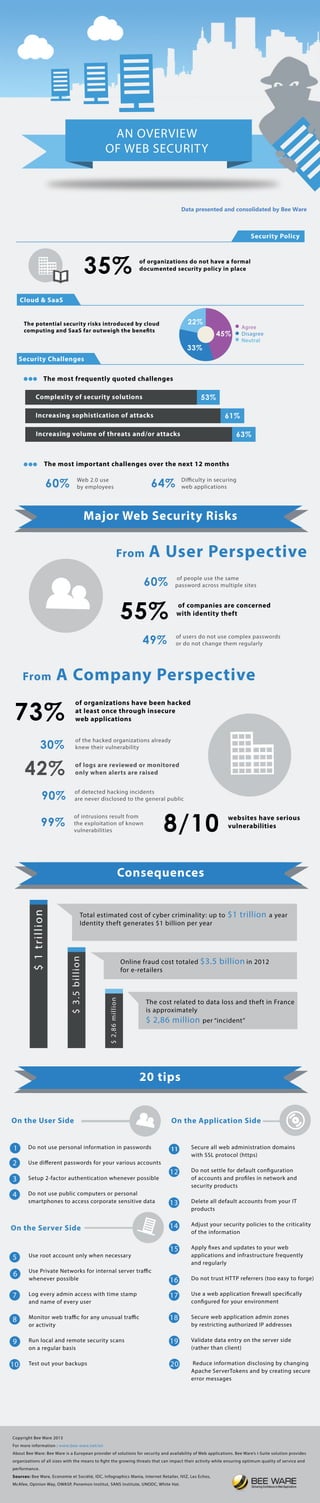
- 1. CopyrightBeeWare2013 Formoreinformation:www.bee-ware.net/en AboutBeeWare:BeeWareisaEuropeanproviderofsolutionsforsecurityandavailabilityofWebapplications.BeeWare’si-Suitesolutionprovides organizationsofallsizeswiththemeansto ghtthegrowingthreatsthatcanimpacttheiractivitywhileensuringoptimumqualityofserviceand performance. Sources:BeeWare,EconomieetSociété,IDC,InfographicsMania,InternetRetailer,IVIZ,LesEchos, MMcAfee,OpinionWay,OWASP,PonemonInstitut,SANSInstitute,UNODC,WhiteHat. From AUserPerspective 60% ofpeopleusethesame passwordacrossmultiplesites 55% ofcompaniesareconcerned withidentitytheft 49% ofusersdonotusecomplexpasswords ordonotchangethemregularly From ACompanyPerspective 73% 90% 30% 99% 42% 8/10websiteshaveserious vulnerabilities oforganizationshavebeenhacked atleastoncethroughinsecure webapplications ofdetectedhackingincidents areneverdisclosedtothegeneralpublic ofthehackedorganizationsalready knewtheirvulnerability oflogsarereviewedormonitored onlywhenalertsareraised ofintrusionsresultfrom theexploitationofknown vulnerabilities OntheUserSide Donotusepersonalinformationinpasswords Usedifferentpasswordsforyourvariousaccounts Setup2-factorauthenticationwheneverpossible Donotusepubliccomputersorpersonal smartphonestoaccesscorporatesensitivedata 1 2 3 4 OntheApplicationSide Secureallwebadministrationdomains withSSLprotocol(https) Donotsettlefordefaultcon guration ofaccountsandpro lesinnetworkand securityproducts DeletealldefaultaccountsfromyourIT pproducts Adjustyoursecuritypoliciestothecriticality oftheinformation Apply xesandupdatestoyourweb applicationsandinfrastructurefrequently andregularly DonottrustHTTPreferrers(tooeasytoforge) UUseawebapplication rewallspecically con guredforyourenvironment Securewebapplicationadminzones byrestrictingauthorizedIPaddresses Validatedataentryontheserverside (ratherthanclient) Reduceinformationdisclosingbychanging AApacheServerTokensandbycreatingsecure errormessages 11 12 13 14 15 16 17 18 19 20 OntheServerSide Userootaccountonlywhennecessary UsePrivateNetworksforinternalservertraffic wheneverpossible Logeveryadminaccesswithtimestamp andnameofeveryuser Monitorwebtrafficforanyunusualtraffic oraoractivity Runlocalandremotesecurityscans onaregularbasis Testoutyourbackups 5 6 7 8 9 10 $1trillion $3.5billion $2,86million Totalestimatedcostofcybercriminality:upto$1trillionayear Identitytheftgenerates$1billionperyear ThecostrelatedtodatalossandtheftinFrance isapproximately $2,86millionper“incident” Onlinefraudcosttotaled$3.5billionin2012 fore-retailers SecurityPolicy oforganizationsdonothaveaformal documentedsecuritypolicyinplace35% Cloud&SaaS Agree Disagree Neutral 45% 22% 33% Thepotentialsecurityrisksintroducedbycloud computingandSaaSfaroutweighthebene ts Increasingvolumeofthreatsand/orattacks 63% Increasingsophisticationofattacks 61% Complexityofsecuritysolutions 53% Themostfrequentlyquotedchallenges SecurityChallenges 64% Difficultyinsecuring webapplications60% Web2.0use byemployees Themostimportantchallengesoverthenext12months 20tips Consequences MajorWebSecurityRisks ANOVERVIEW OFWEBSECURITY DatapresentedandconsolidatedbyBeeWare
